Audit Logs
Ingest and export Audit Log Events from your application.
Audit Logs are a collection of events that contain information relevant to notable actions taken by users in your application. Every event in the collection contains details regarding what kind of action was taken (action), who performed the action (actor), what resources were affected by the action (targets), and additional details of when and where the action took place.
{ "action": "user.signed_in", "occurred_at": "2022-08-29T19:47:52.336Z", "actor": { "type": "user", "id": "user_01GBNJC3MX9ZZJW1FSTF4C5938" }, "targets": [ { "type": "team", "id": "team_01GBNJD4MKHVKJGEWK42JNMBGS" } ], "context": { "location": "123.123.123.123", "user_agent": "Chrome/104.0.0.0" } }
These events are similar to application logs and analytic events, but are fundamentally different in their intent. They aren’t typically used for active monitoring/alerting, rather they exist as a paper trail of potentially sensitive actions taken by members of an organization for compliance and security reasons.
This guide will show you how to:
- Configure and emit Audit Log Events
- Export Audit Log Events
- Create custom metadata schemas for Audit Log Events
- Create new versions of Audit Log Event schemas
- Audit Log Event
- An individual event that represents an action taken by an actor within your app.
- Audit Log Export
- A collection of Audit Log Events that are exported from WorkOS as a CSV file.
- Organization
- Describes a customer where Audit Log Events originate from.
WorkOS offers native SDKs in several popular programming languages. Choose a language below to see instructions in your application’s language.
Don't see an SDK you need? Contact us to request an SDK!
Install the SDK using the command below.
npm install @workos-inc/node
To make calls to WorkOS, provide the API key and, in some cases, the client ID. Store these values as managed secrets, such as WORKOS_API_KEY and WORKOS_CLIENT_ID, and pass them to the SDKs either as environment variables or directly in your app’s configuration based on your preferences.
WORKOS_API_KEY='sk_example_123456789' WORKOS_CLIENT_ID='client_123456789'
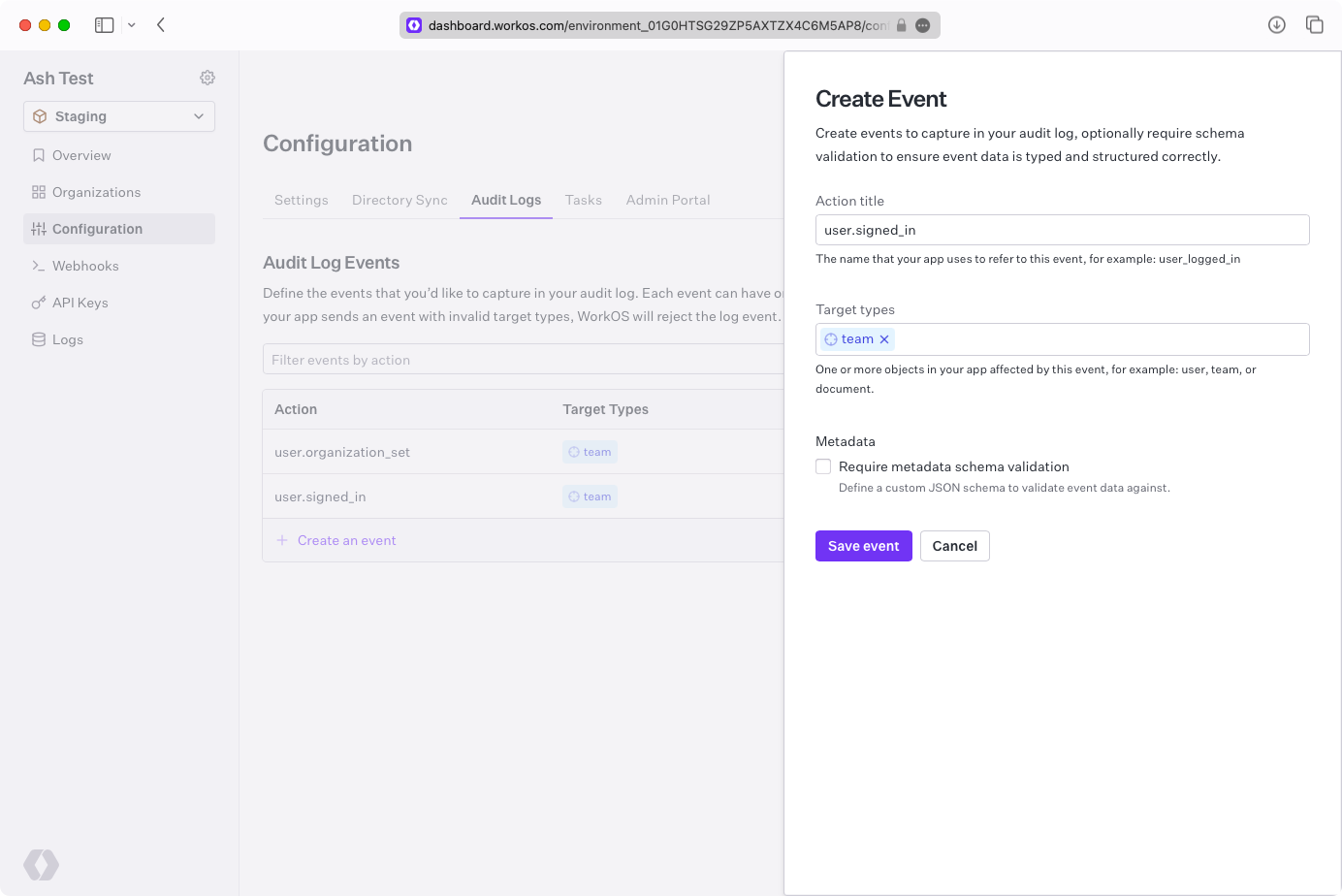
Before you can emit any Audit Log Events you must configure the allowed event schemas. To start, click “Create an event” and enter user.signed_in for action, team for targets, and click “Save event”.
All events are scoped to an Organization, so you will need the ID of an Organization in order to emit events.
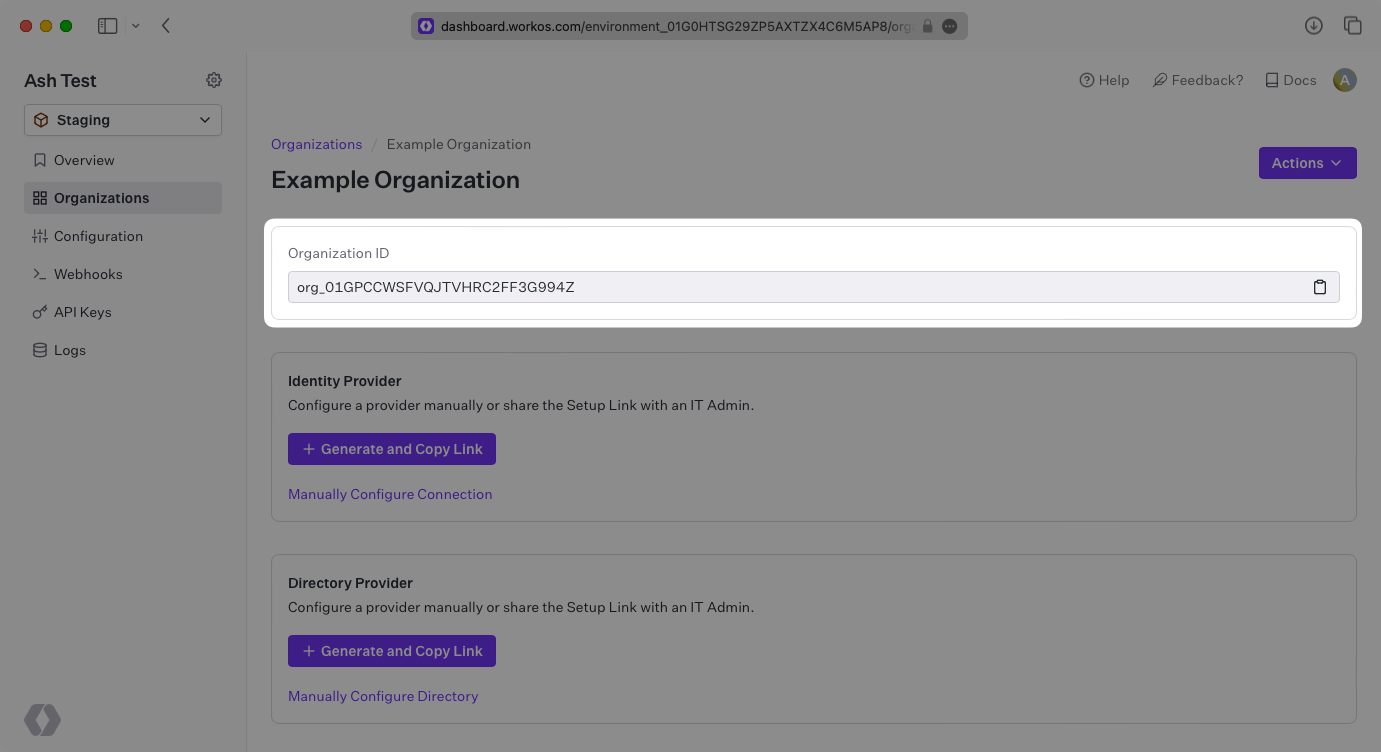
Using the ID from the Organization, emit an Audit Log Event with the action and targets previously configured.
import { WorkOS } from '@workos-inc/node'; const workos = new WorkOS('sk_example_123456789'); await workos.auditLogs.createEvent('org_01EHWNCE74X7JSDV0X3SZ3KJNY', { action: 'user.signed_in', occurredAt: new Date(), actor: { type: 'user', id: 'user_01GBNJC3MX9ZZJW1FSTF4C5938', }, targets: [ { type: 'team', id: 'team_01GBNJD4MKHVKJGEWK42JNMBGS', }, ], context: { location: '123.123.123.123', userAgent: 'Chrome/104.0.0.0', }, });
Idempotency
WorkOS Audit Logs supports idempotency to ensure events are not duplicated when retrying requests. You can provide an idempotency-key header with your event creation request. If you don’t provide one, WorkOS will automatically generate one based on the event content.
When you provide an idempotency key:
- WorkOS creates a hashed key combining your provided key with the event data
- Subsequent requests with the same idempotency key and event data will return the same response
- This prevents duplicate events from being created due to network retries or other issues
When you don’t provide an idempotency key:
- WorkOS automatically generates one using the event content
- This provides basic duplicate protection based on event data alone
