LastPass
Learn how to configure a connection to LastPass via SAML.
Each SSO Identity Provider requires specific information to create and configure a new Connection. Often, the information required to create a Connection will differ by Identity Provider.
To create a LastPass SAML Connection, you’ll need an IdP Metadata XML file.
Start by logging in to your WorkOS dashboard and browse to the “Organizations” tab on the left hand navigation bar.
Select the organization you’d like to configure a LastPass SAML Connection for, and select “Manually Configure Connection” under “Identity Provider”.
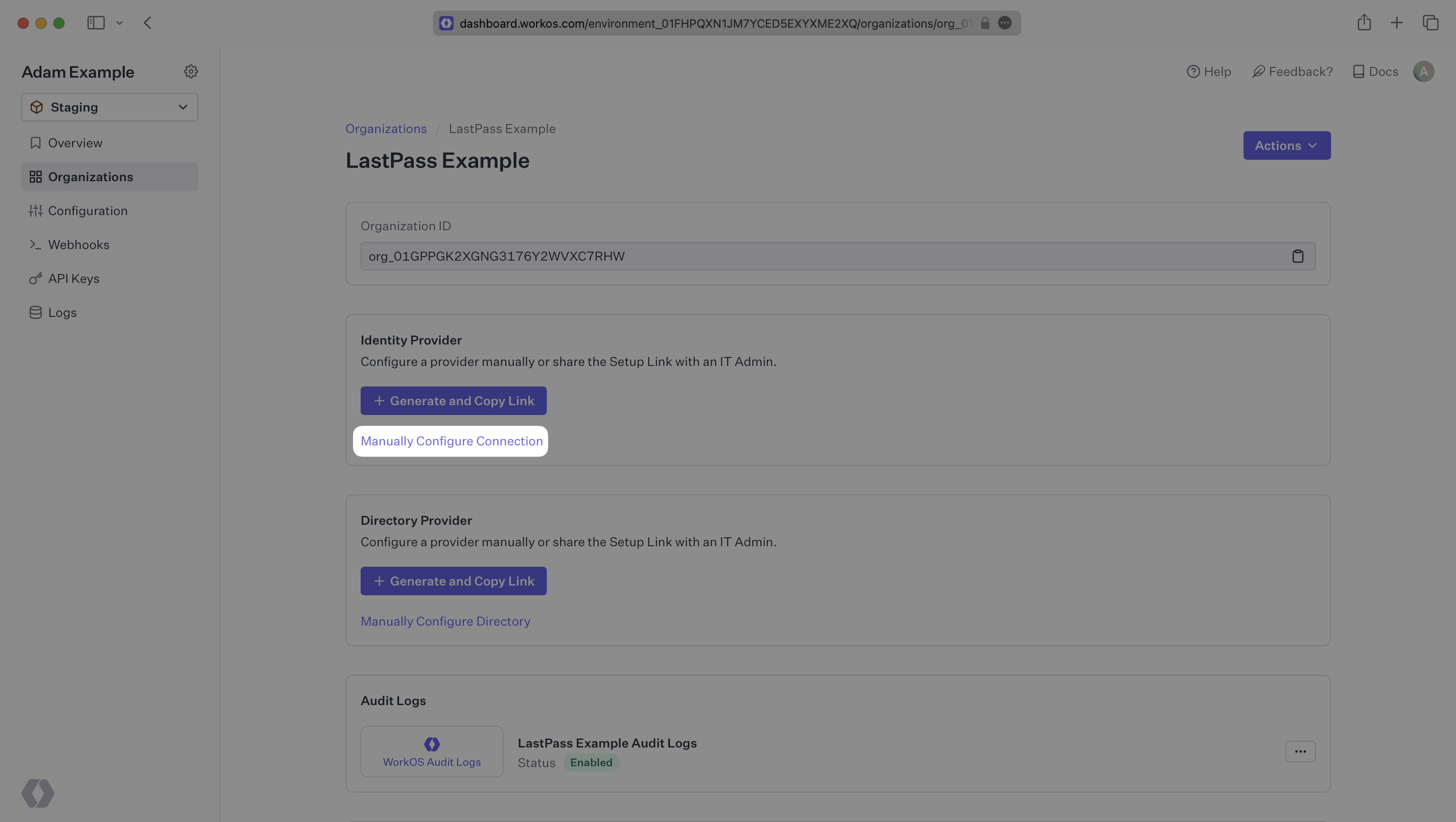
Select “LastPass SAML” from the Identity Provider dropdown, enter a descriptive name for the connection, and then select the “Create Connection” button.
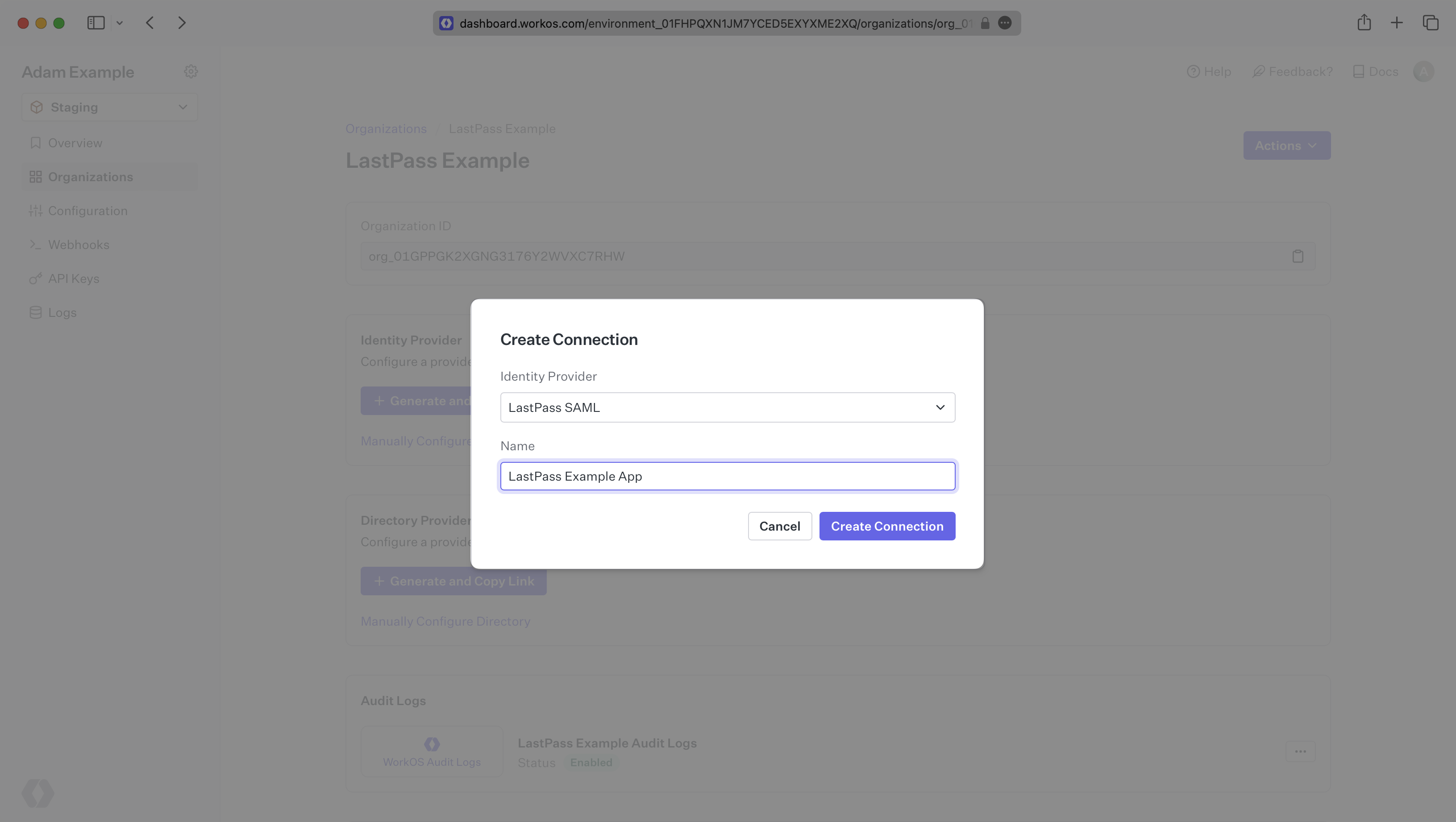
WorkOS provides the ACS URL, SP Entity ID, and SP Metadata URL. They’re readily available in your Connection Settings in the WorkOS Dashboard.
Next, provide the IdP Metadata file. Normally, this information will come from your enterprise customer’s IT Management team when they set up your application’s SAML 2.0 configuration in their LastPass admin console. But, should that not be the case during your setup, the next steps will show you how to obtain it.
Log in to LastPass, go to the admin console and select “Applications” on the top navigation. Then select “SSO apps” from the left side navigation. If your application is already created, select it from the list of applications and move to Step 2. Otherwise, select “Add app”.
In the modal that pops up, click on “Add an unlisted app”.
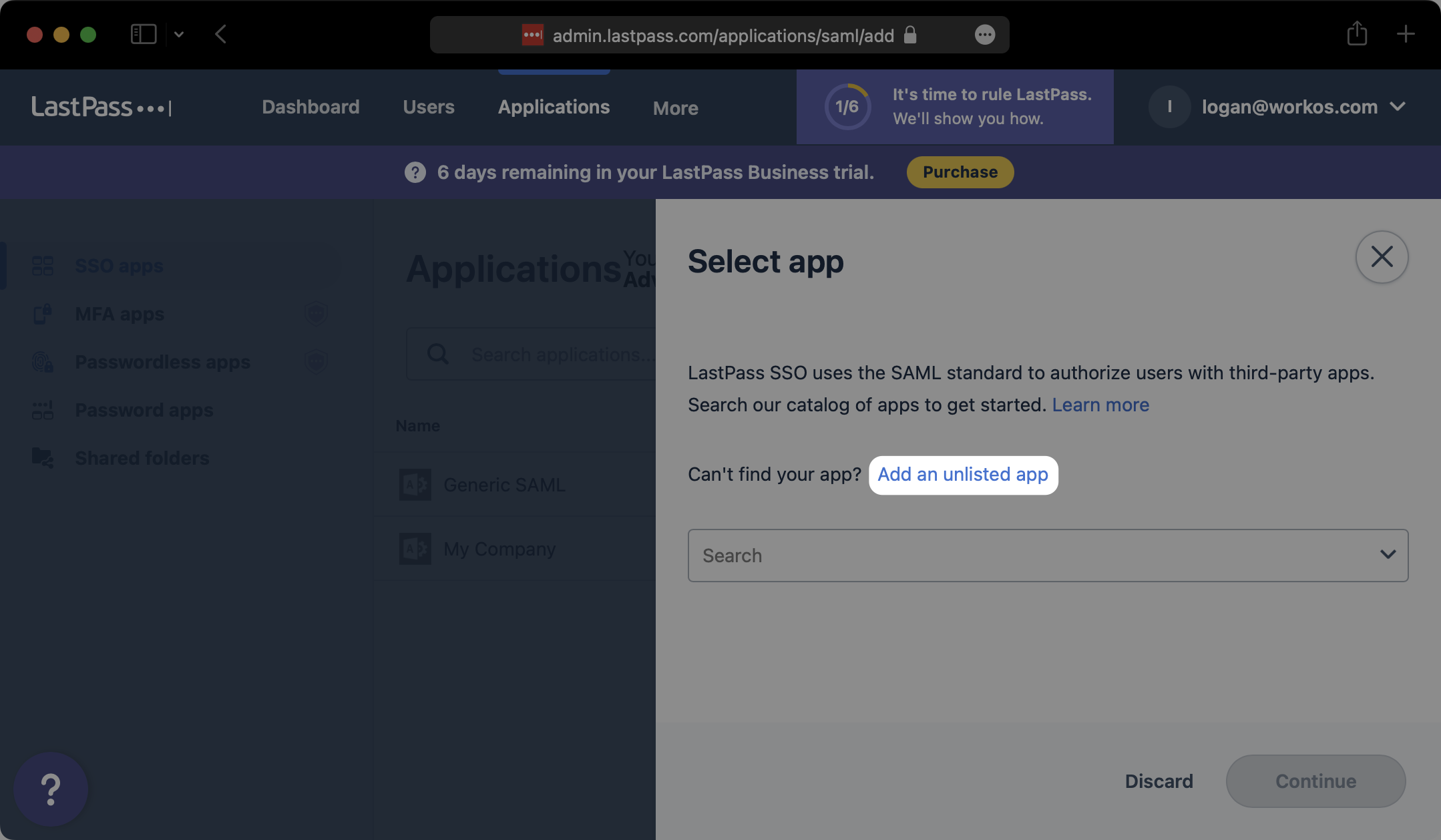
Give your SAML App a descriptive name and select “Continue”.
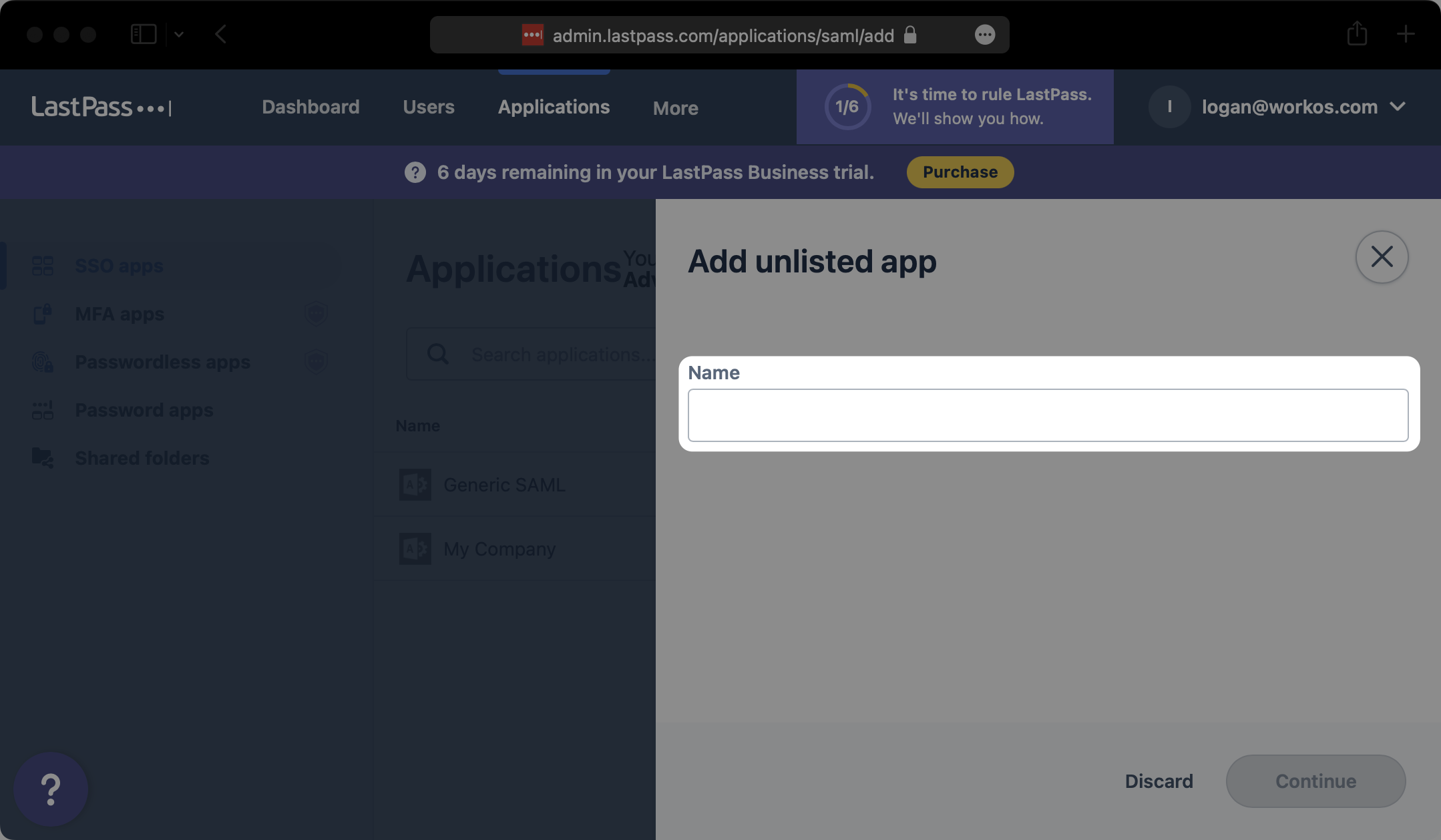
Under the “Set up LastPass” section of the “Configure app” modal, input the ACS URL from the WorkOS Dashboard Connection details under “ACS”. Then click on “Advanced Settings”.
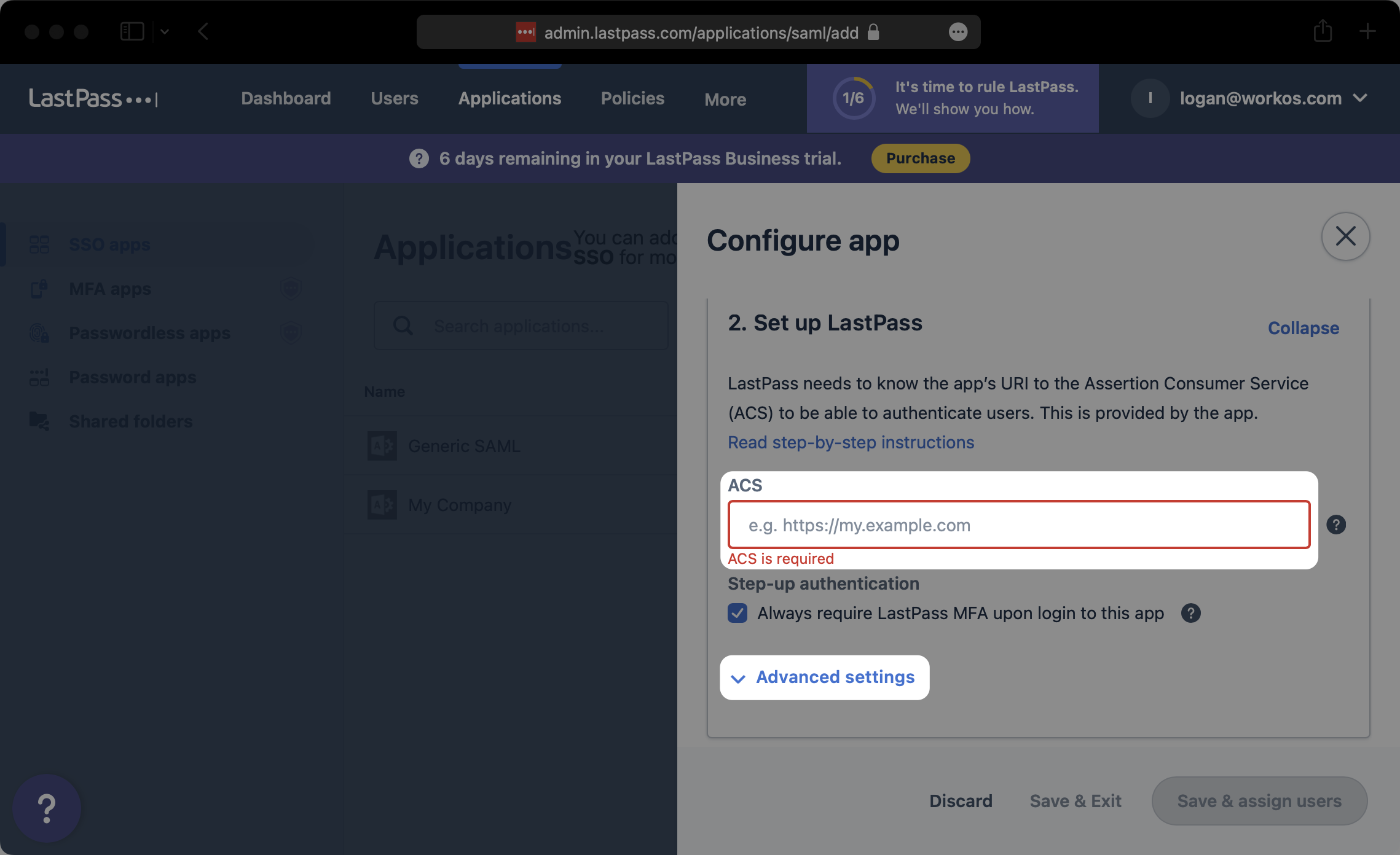
Under “Entity ID”, input the SP Entity ID from the WorkOS Dashboard Connection details. Next, under “SAML signature method”, select “SHA256”.
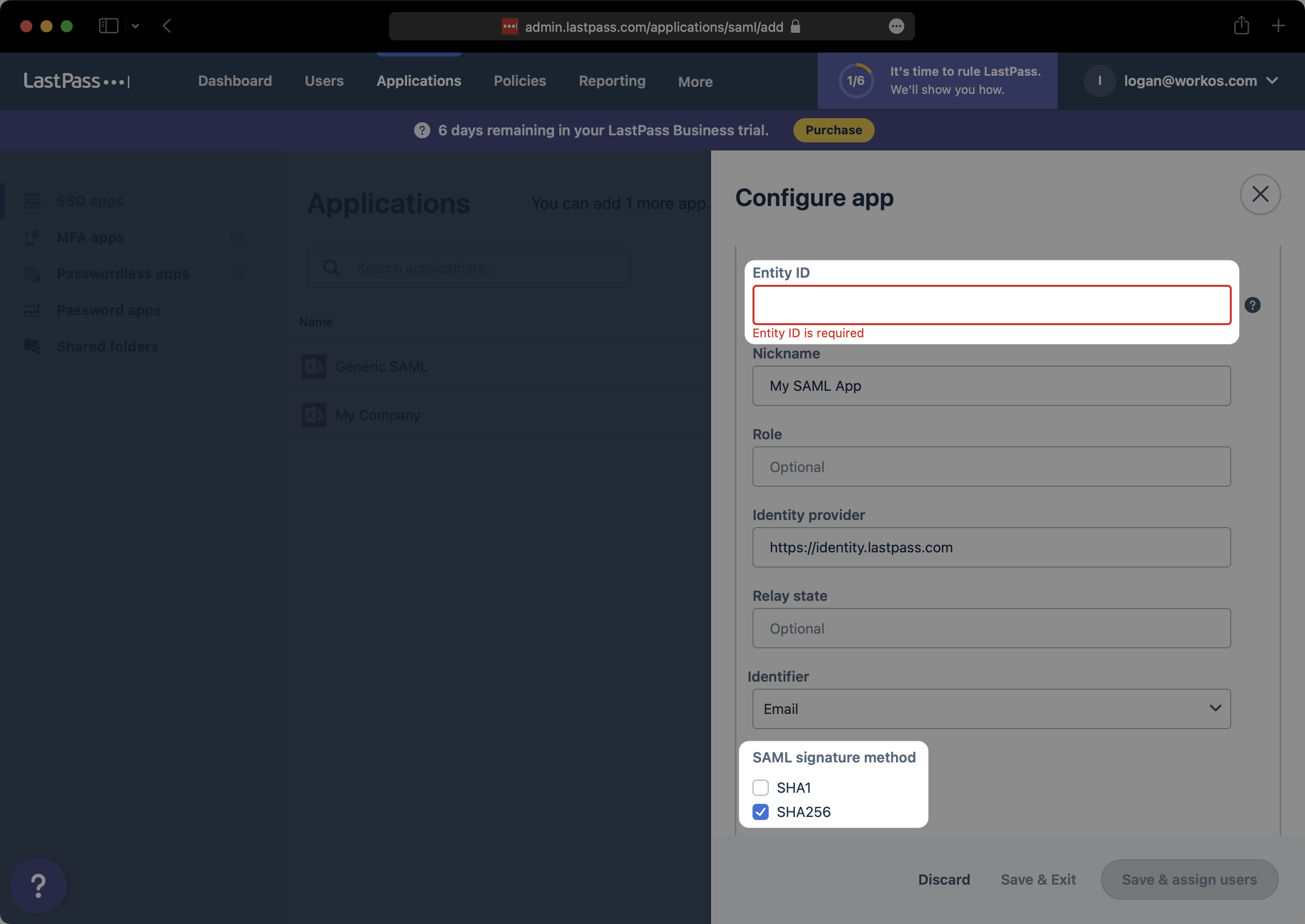
Under “Signing and encryption”, ensure that you have at least selected “Sign assertion”. Then, click on “Add SAML attribute”.
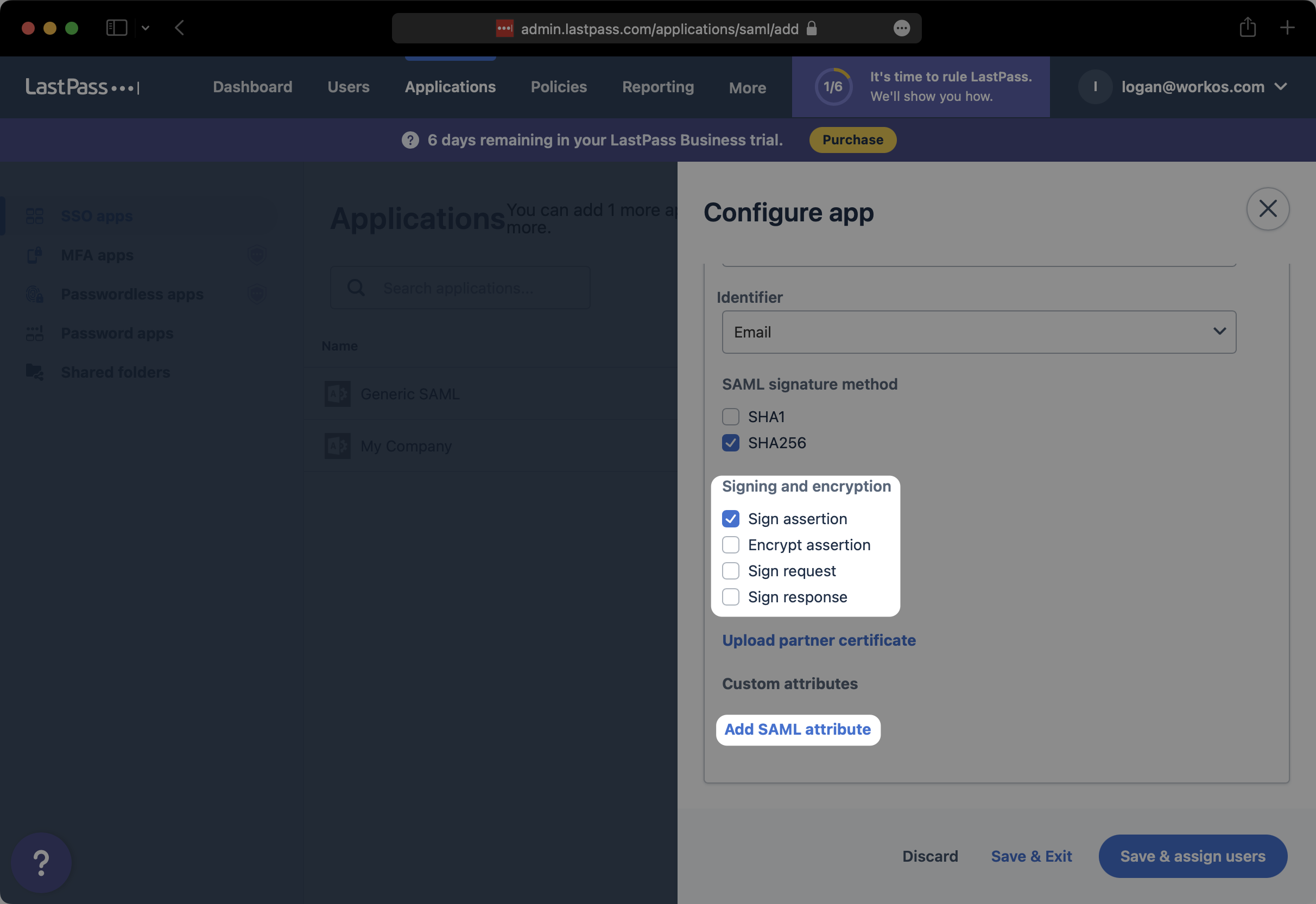
Map the following four attributes as shown below, and select “Save & assign users”.
- First Name →
firstName - Last Name →
lastName - Email →
email - User ID →
id
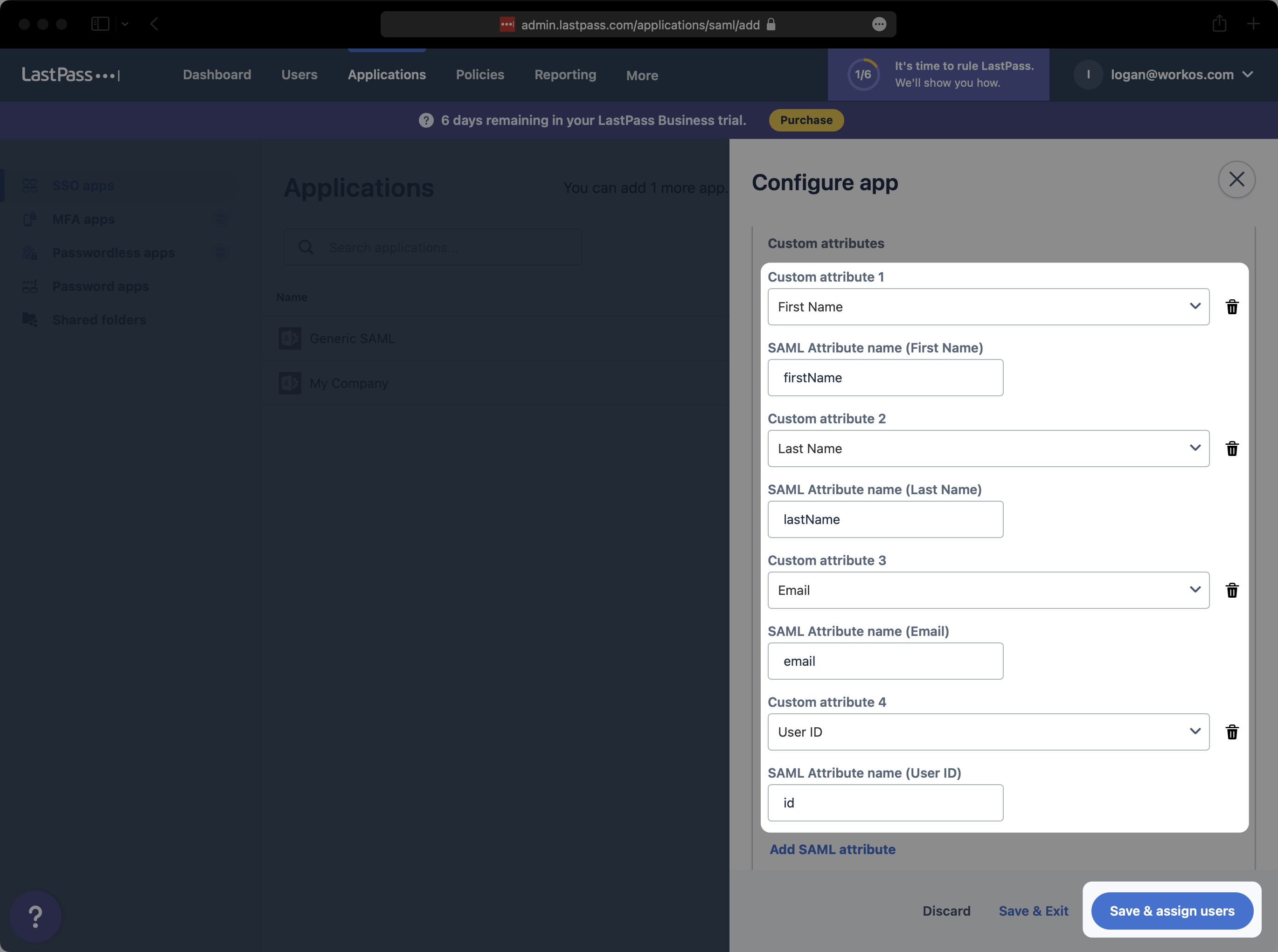
With identity provider role assignment, users can receive roles within your application based on their group memberships. To return this information in the attribute statement, add a new SAML attribute for the “Groups” field and input groups as the attribute name, as shown below. Then, select “Save & assign users”.
Finish role assignment set-up by navigating to the SSO connection page in the Organization section of the WorkOS Dashboard. Create SSO groups by referencing the group IdP ID. Then, assign roles to these SSO groups so group members are automatically granted roles within your application.
On the “Users, groups & roles” page, click on “Assign users, groups & roles”.
Search and select any users or groups that you would like to provision to this SAML app. Then, click “Assign”.
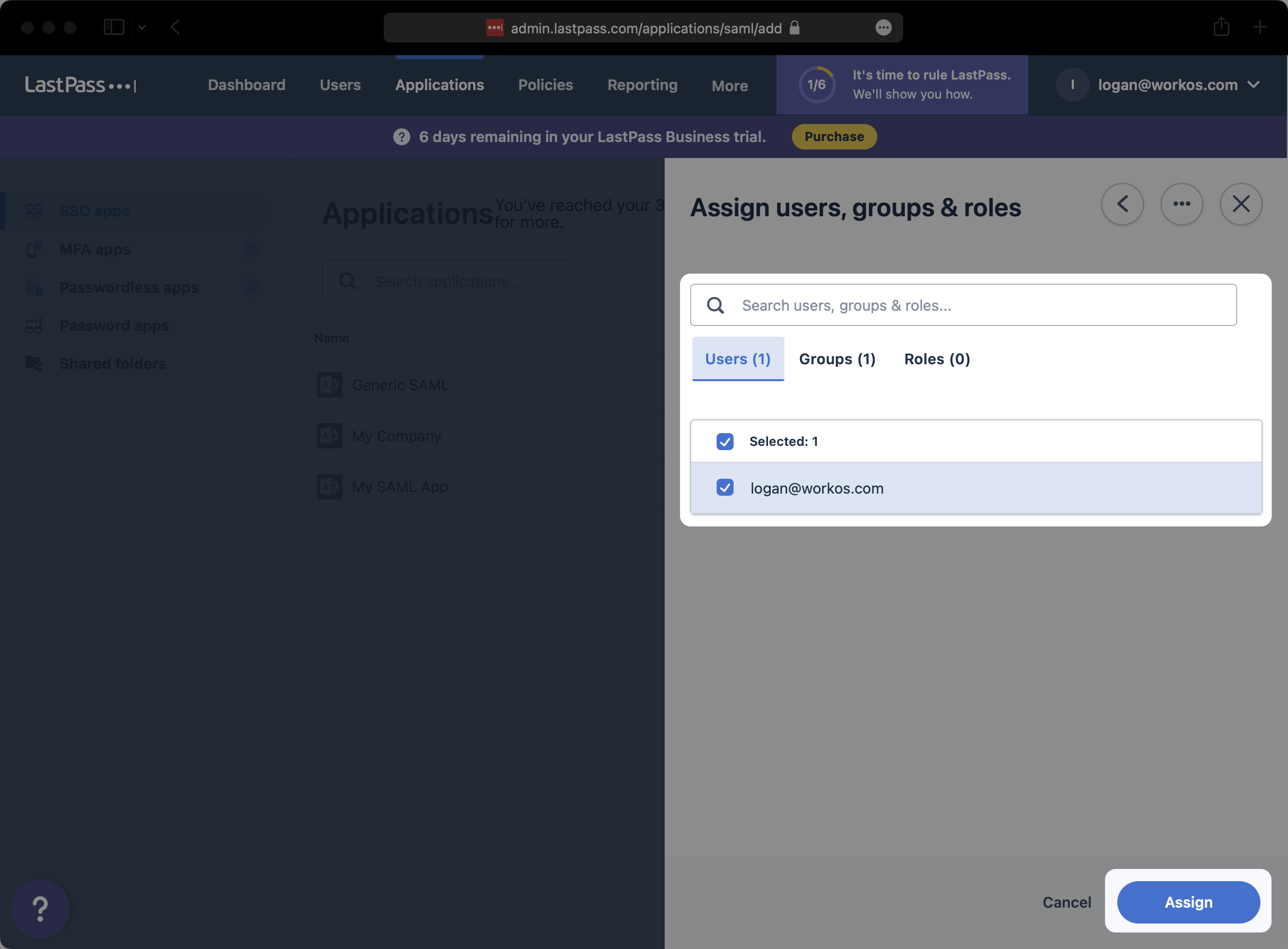
Click on “Save & continue”.
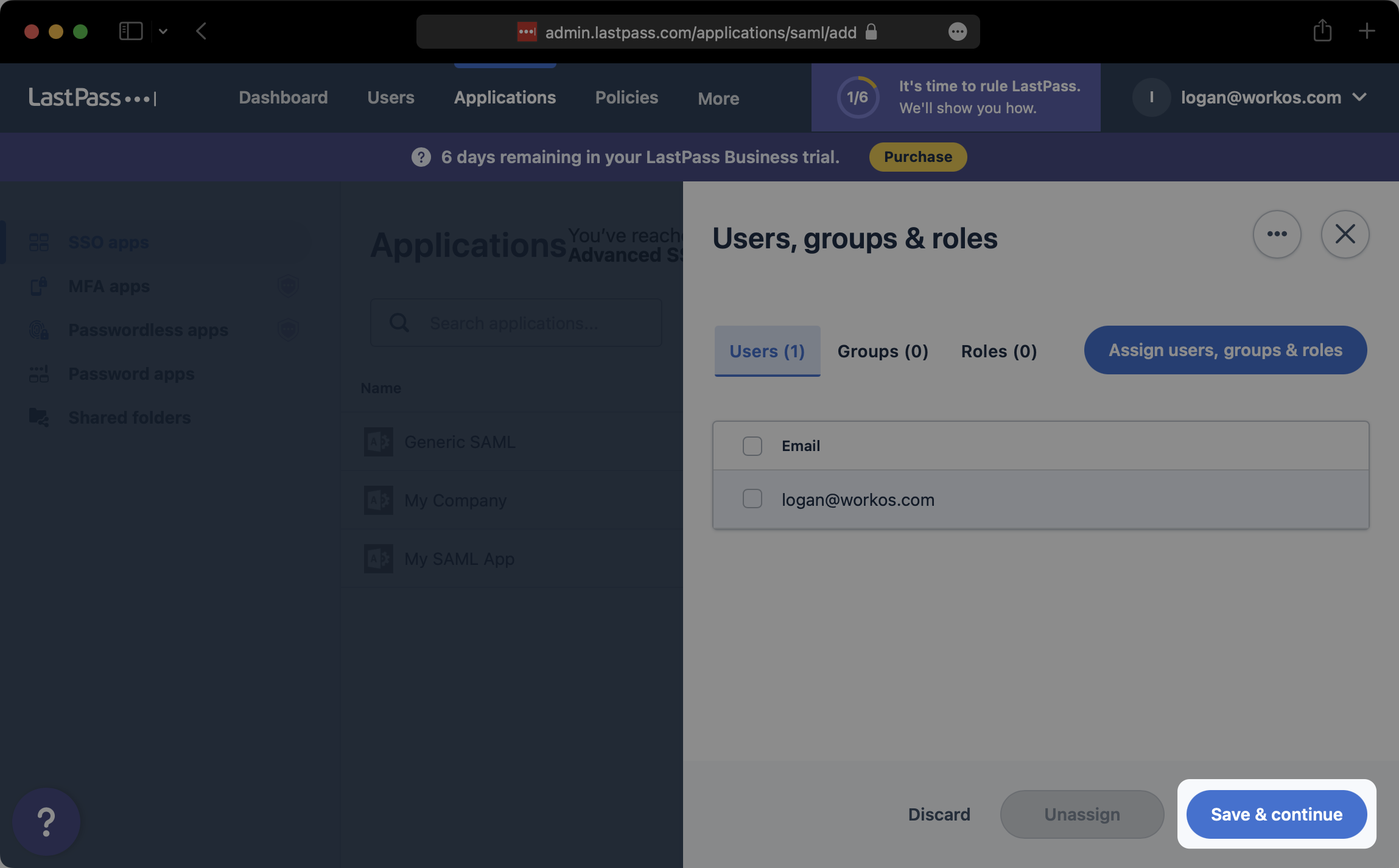
Back on the “SSO apps” tab of the LastPass admin console, select the SAML app that you just created.
!A screenshot showing where how to select SAML App in LastPass.](https://images.workoscdn.com/images/99a9a771-02bc-4817-b576-414bafa2d6f2.png?auto=format&fit=clip&q=50)
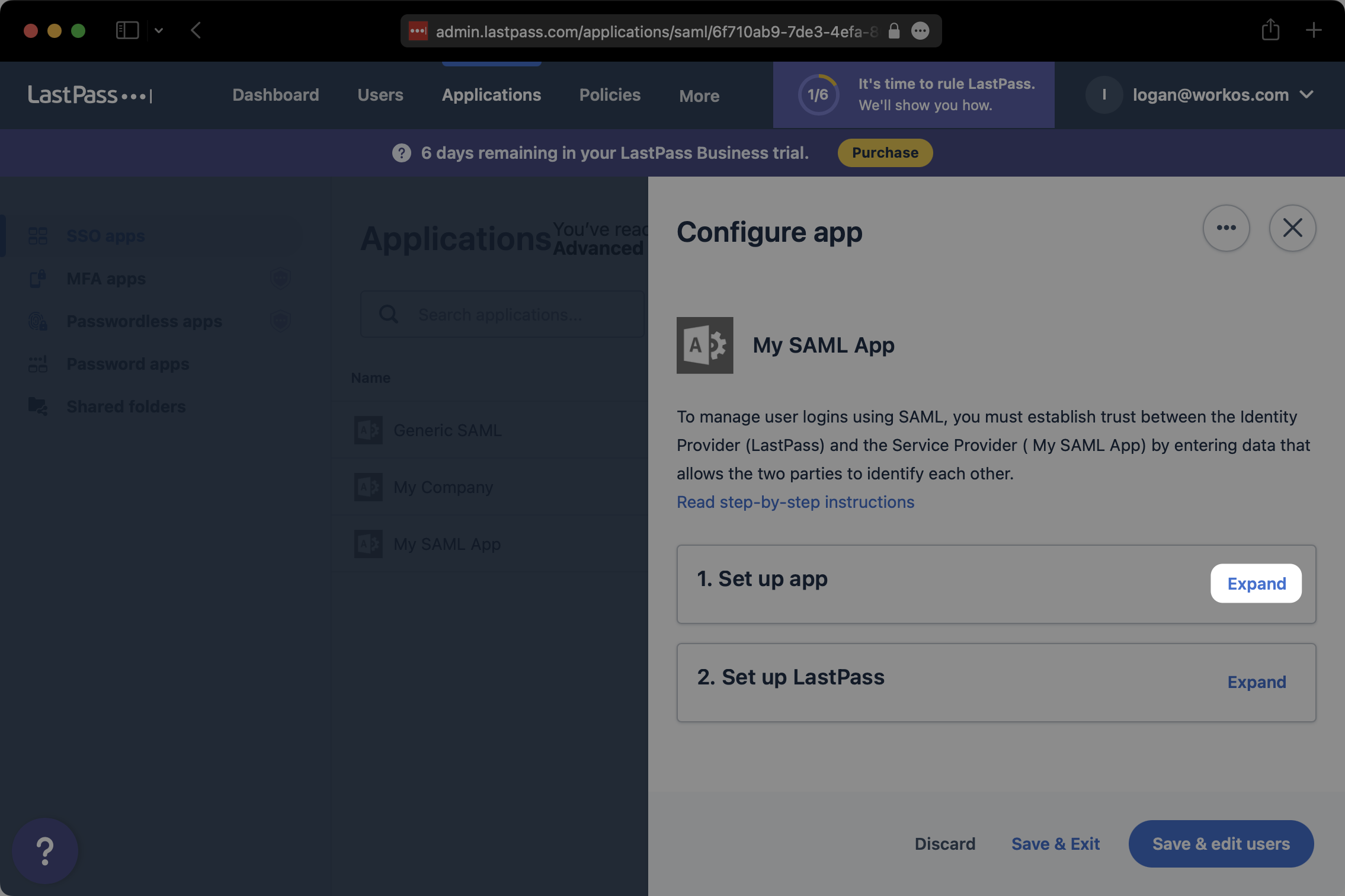
On the “Configure app” modal, click on “Expand” to the right of “Set up app”.
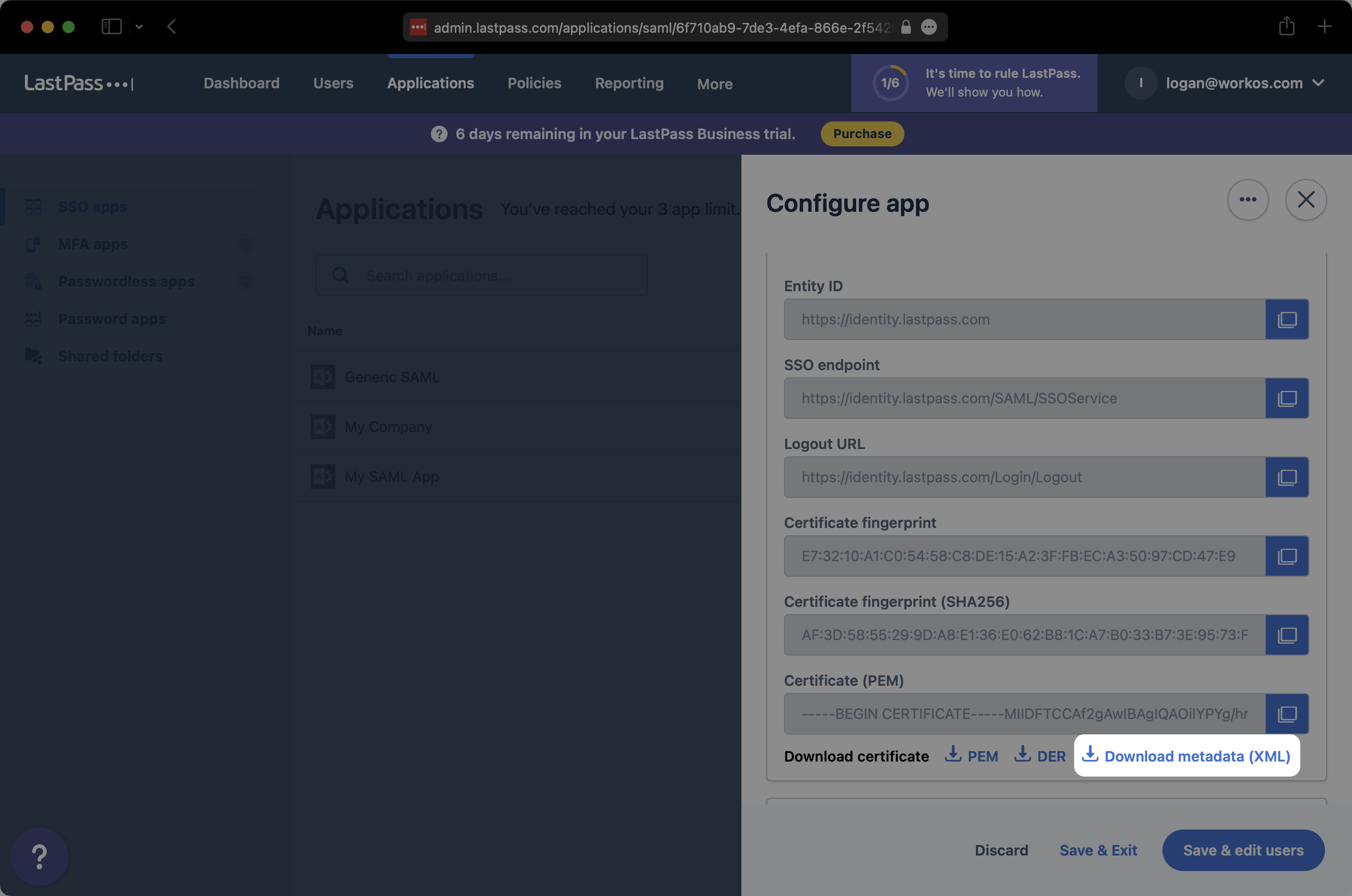
At the bottom of the “Set up app” section, click on “Download metadata (XML)”. Save the downloaded XML metadata somewhere accessible.
In the Connection settings in the WorkOS Dashboard, click “Edit Metadata Configuration”.
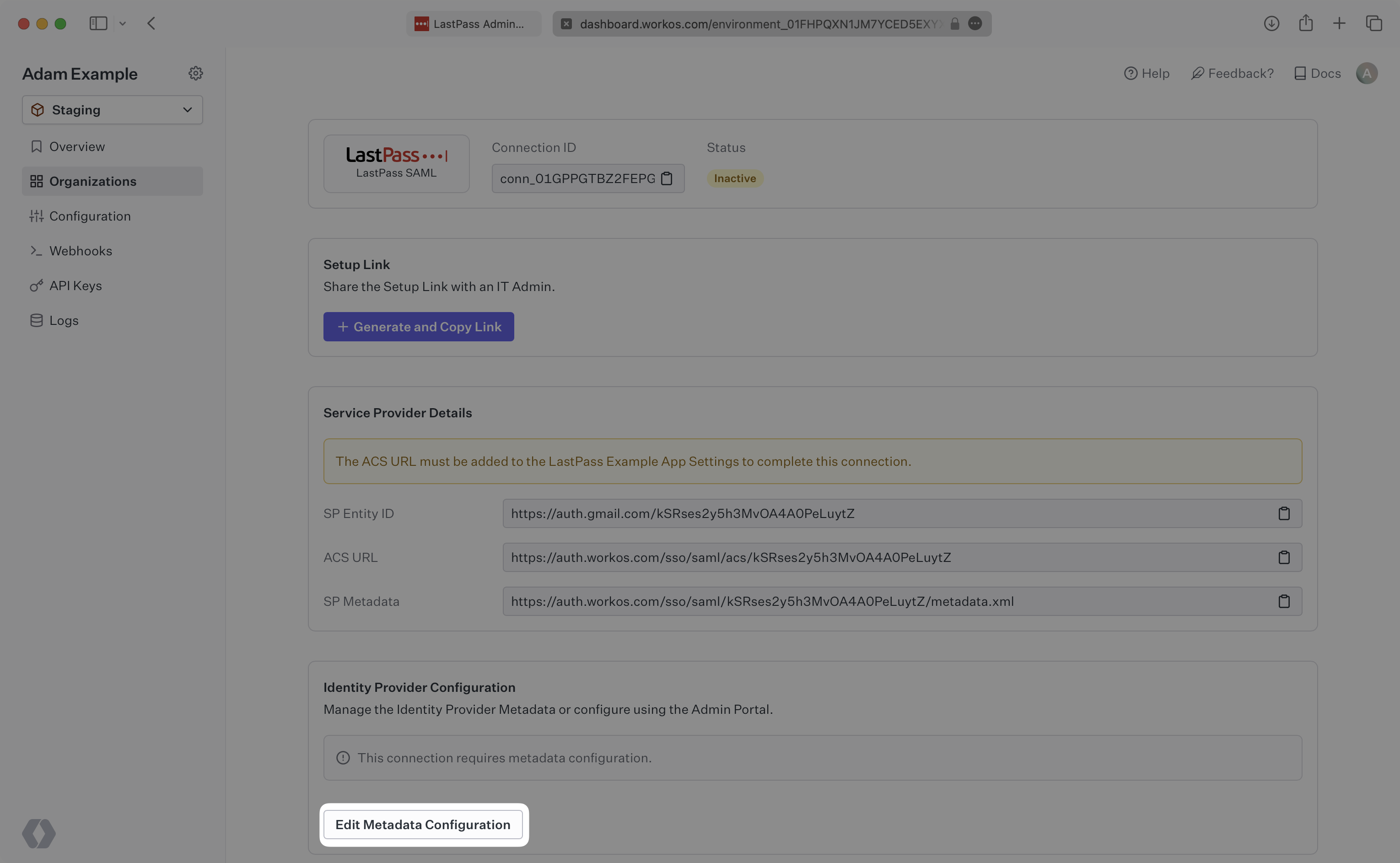
Upload the XML metadata file from LastPass into the “Metadata File” field and select “Save Metadata Configuration”.
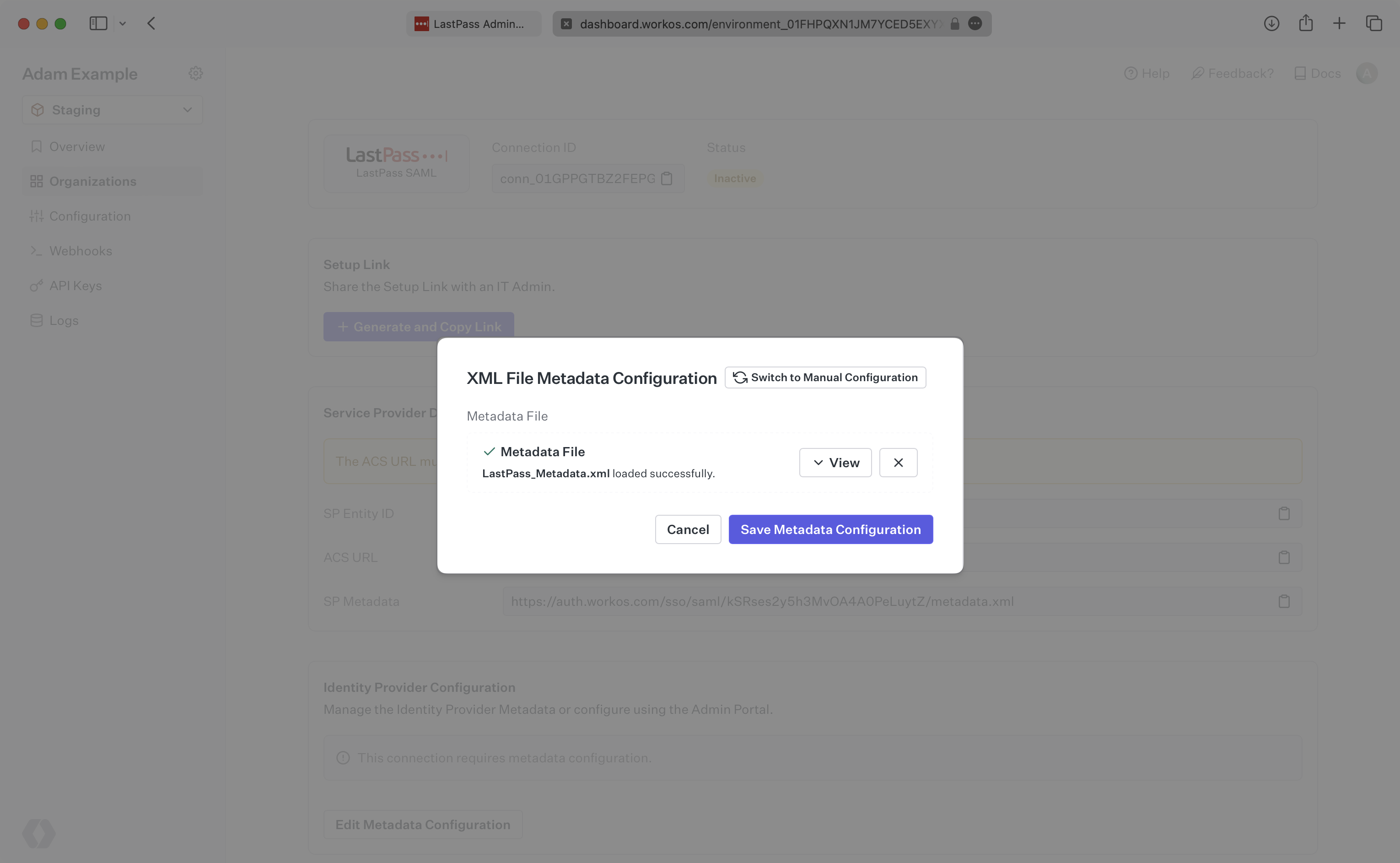
Your Connection will then be linked and good to go!