Identity Provider Role Assignment
Learn how to map role data from identity providers to roles in your app with SSO.
A role represents a logical grouping of permissions, defining access control levels for users within your application. Roles are identified by a unique, immutable slug and are assigned to SSO user profiles through their identity provider group memberships. These group role mappings can be configured on the WorkOS dashboard.
To utilize Identity Provider (IdP) role assignment, you must first configure roles.
Users are assigned to groups via the identity provider. Groups usually correspond to roles in your app. Therefore, IT admins will often map a group one-to-one to a role.
During authentication, a user’s identity provider group memberships can be read via attributes. This enables you to define SSO groups that correspond to IdP groups and set role assignments for those groups in the WorkOS Dashboard.
Based on these settings, SSO user profiles returned from WorkOS will include a role attribute that reflects their highest priority group membership. The SSO user profile role is calculated during each sign-in.
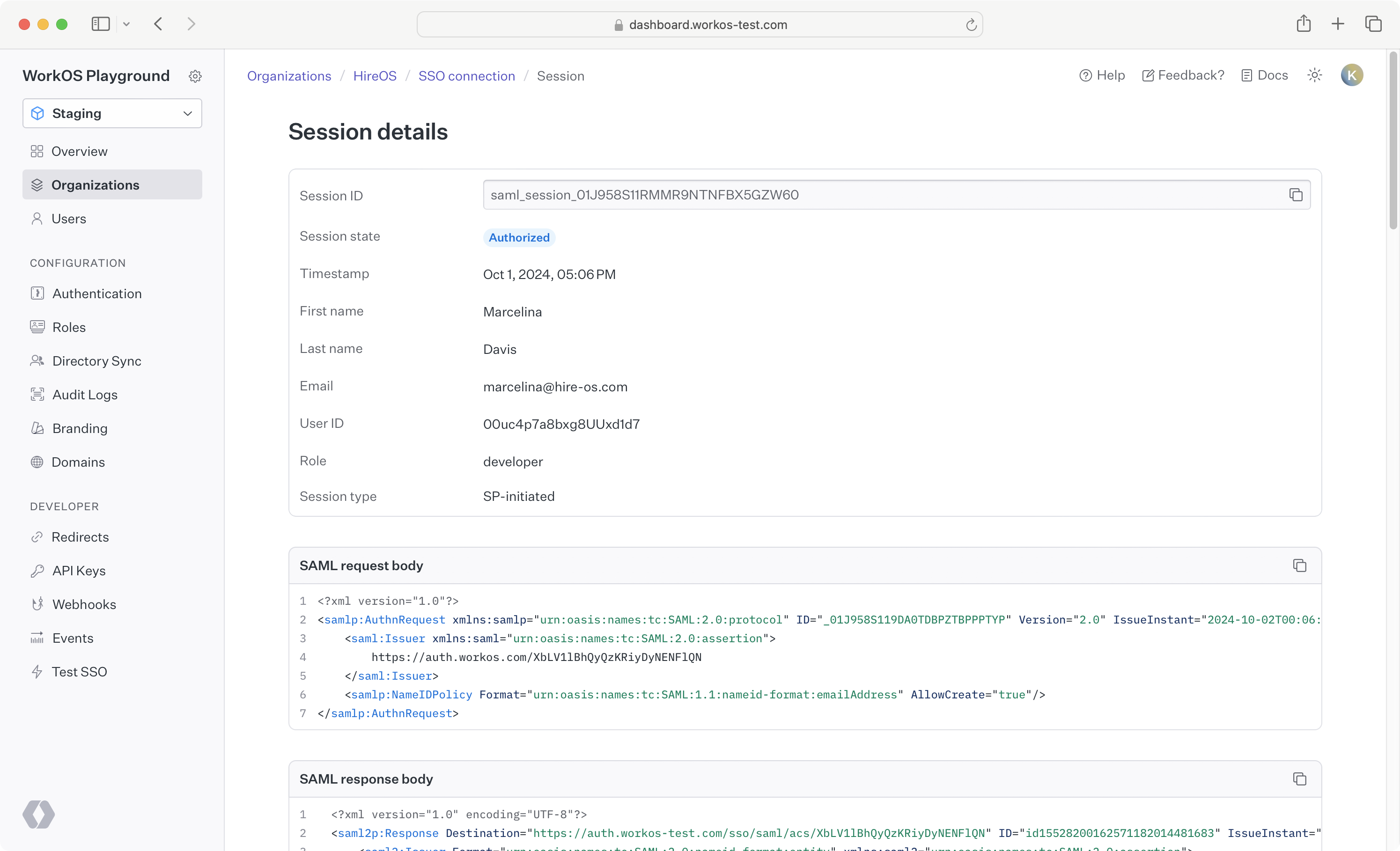
Consider the fictional SaaS company HireOS. HireOS has set up an SSO Connection and configured group-based role assignment. For example, a HireOS customer would like to assign their engineering team to the application. The customer’s IT admin would take the following steps:
- Create an “Engineering” group using their identity provider.
- Configure the
groupsattribute in their SAML app to return the group memberships. - Provide the developer with the IdP ID for the “Engineering” group.
In the WorkOS dashboard, the developer can then assign users of that group to the role “Engineer”.
- Navigate to the Connection section of the WorkOS dashboard.
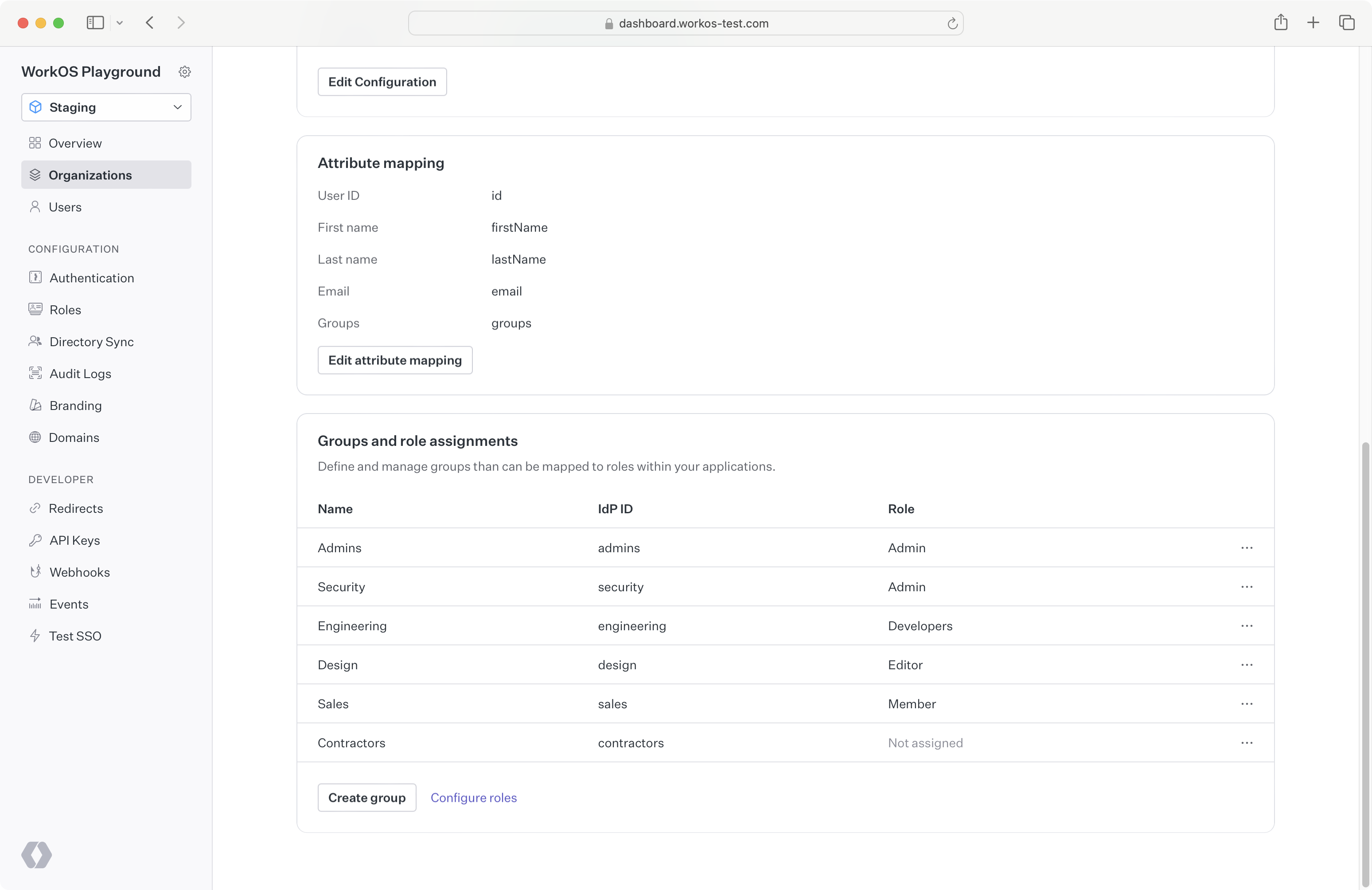
- Create an SSO group defining the IdP ID for the “Engineering” group. Then, assign this group to the “Engineer” role.
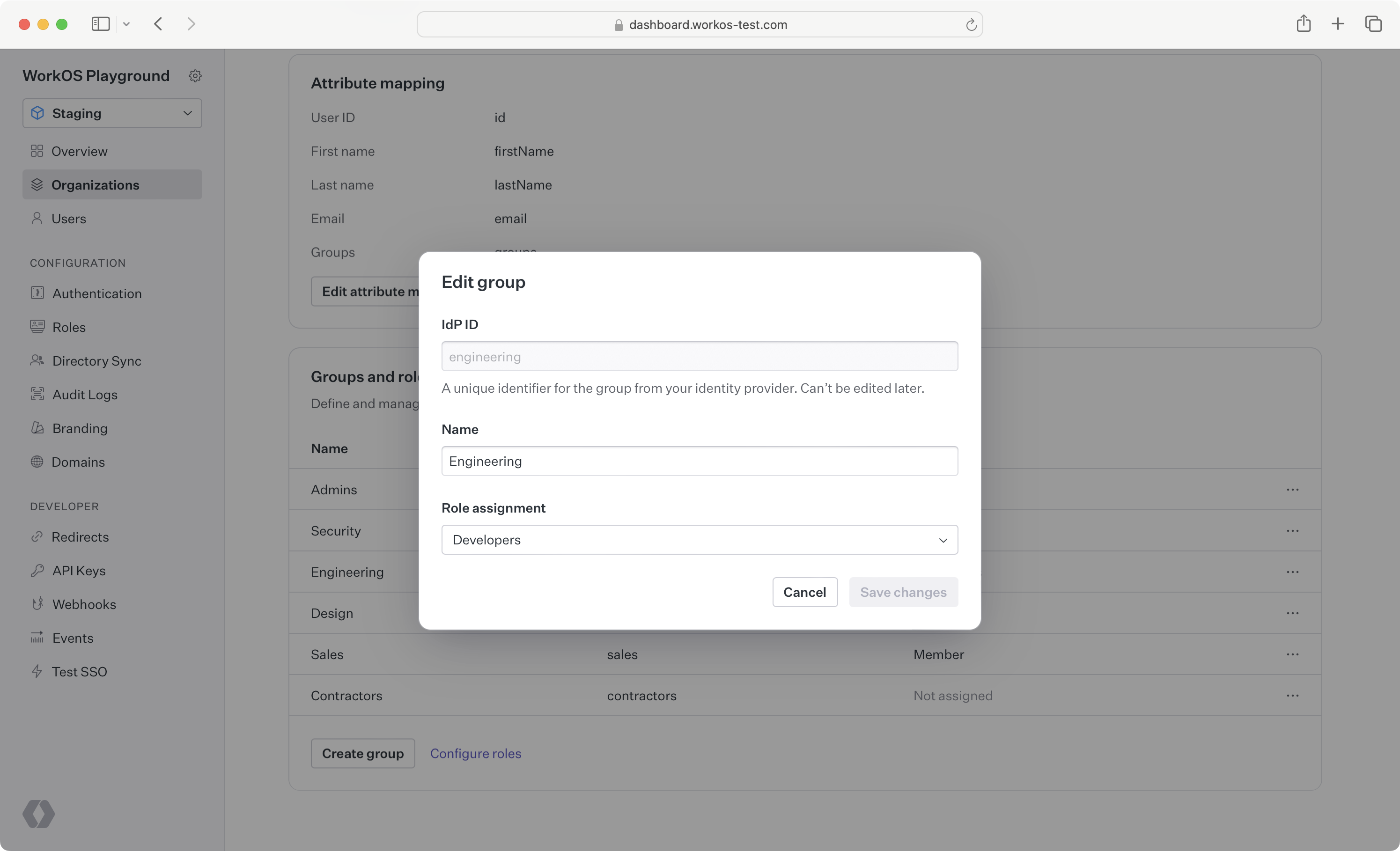
From this point on, whenever a user in the “Engineering” group authenticates via SSO, they will be granted the “Engineer” role for that session from the WorkOS API. The role will be returned in the profile response.
{ "object": "profile", "id": "prof_01DMC79VCBZ0NY2099737PSVF1", "connection_id": "conn_01E4ZCR3C56J083X43JQXF3JK5", "connection_type": "OktaSAML", "organization_id": "org_01EHWNCE74X7JSDV0X3SZ3KJNY", "email": "todd@example.com", "first_name": "Todd", "last_name": "Rundgren", "idp_id": "00u1a0ufowBJlzPlk357", "role": { "slug": "engineer" }, "roles": [ { "slug": "engineer" } ] }
When multiple roles is enabled, a user can be assigned multiple roles from their identity provider group memberships. If a user belongs to multiple mapped groups, they will receive all corresponding roles in their SSO profile.
For example, if a user is a member of both “Engineering” and “Design” groups, and both groups are mapped to roles, the user will receive both the “Engineer” and “Designer” roles. If a user is not a member of any groups with explicit mappings, they will receive the default role.
Use cases
By default, multiple roles is disabled and users can only have a single role per entity. It’s recommended to start with a single-role setup for simplicity, where it’s easier to maintain consistent and correct access patterns.
You might want to enable multiple roles when you need:
- Cross-department collaboration: e.g., designers who need some engineering permissions.
- Additive, disjoint permissions: independent permission sets that should stack.
- Temporary access: grant time-bound extra capabilities without creating hybrid roles.
Once roles are configured for your application, enable SSO group role assignment in Admin Portal to allow IT admins to assign roles to groups during SSO connection setup. If enabled, all Admin Portal sessions for SSO connections will have the ability to configure and assign roles to groups.
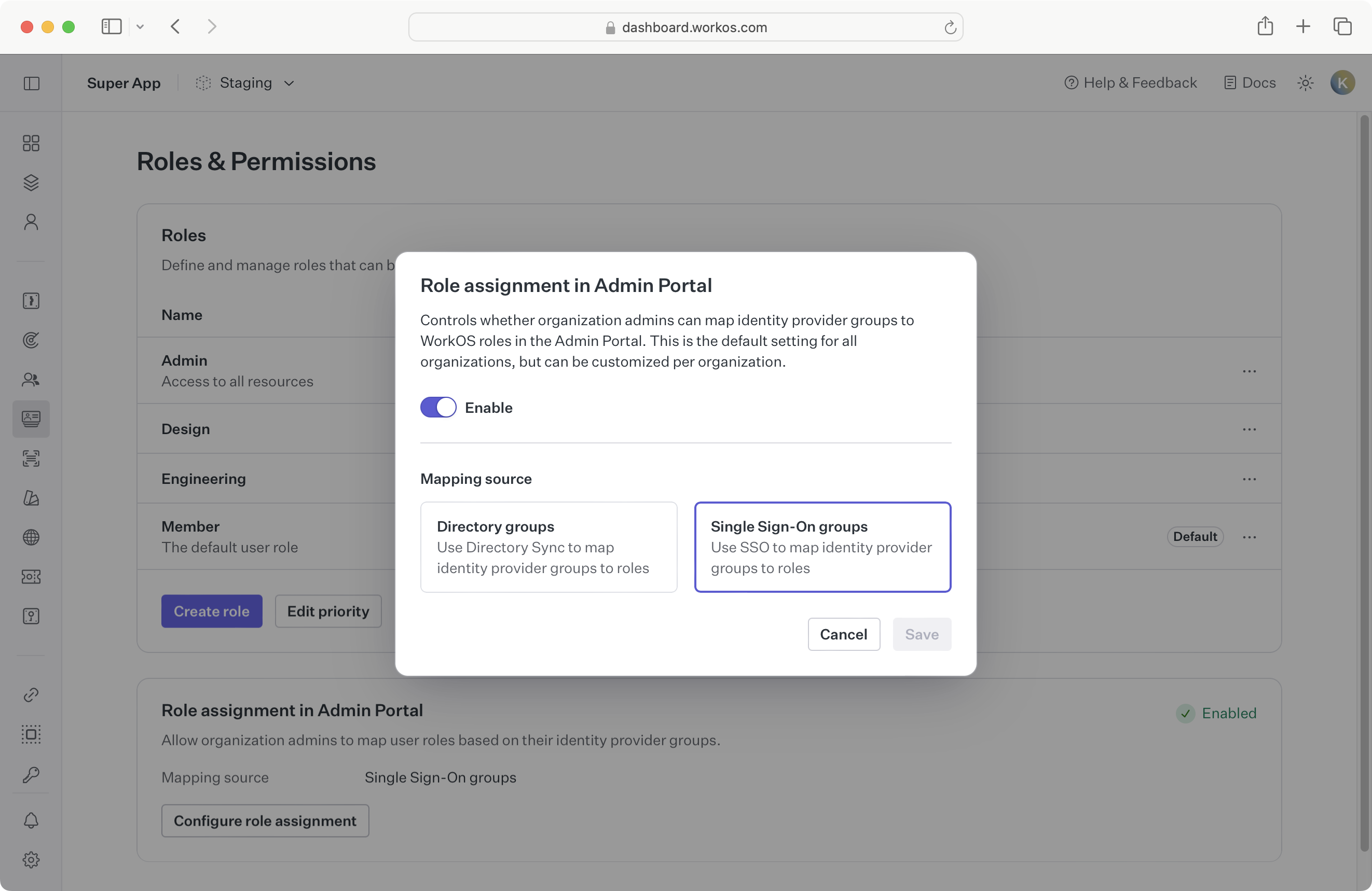
This is an environment-level setting, but can be configured per organization via the Roles tab under an organization in the WorkOS Dashboard.
Your customers will store role information in different forms, depending on their preferred provisioning workflow. WorkOS allows for flexibility in how you source role data. However, there are some considerations to keep in mind when using SSO-based connection groups for role assignment.
Strictly assigning roles during JIT user provisioning has a few caveats:
- Your customer must explicitly map the SAML
groupsattribute in the SSO setup so that you can retrieve that attribute in the SSO profile. - SSO groups need to be manually defined.
- Your app will receive updates to this user’s group data only once they sign-in with SSO again. This delay can allow unauthorized users to access resources using a stale role.
Directory Sync supports group-based role assignment and avoids the pitfalls mentioned above. For organizations with a directory, this method of group-based role assignment is preferred.
It’s recommended to use only one method of role assignment – either from a Directory or an SSO Connection – to avoid overlap.