Rippling SAML
Learn how to configure a connection to Rippling via SAML.
Each SSO Identity Provider requires specific information to create and configure a new Connection. Often, the information required to create a Connection will differ by Identity Provider.
To create a Rippling SAML Connection, you’ll need the Identity Provider metadata that is available from creating an app within the Rippling instance.
Start by logging in to your WorkOS dashboard and browse to the “Organizations” tab on the left hand navigation bar.
Select the organization you wish to configure a Rippling SAML Connection for, and select “Manually Configure Connection” under “Identity Provider”.
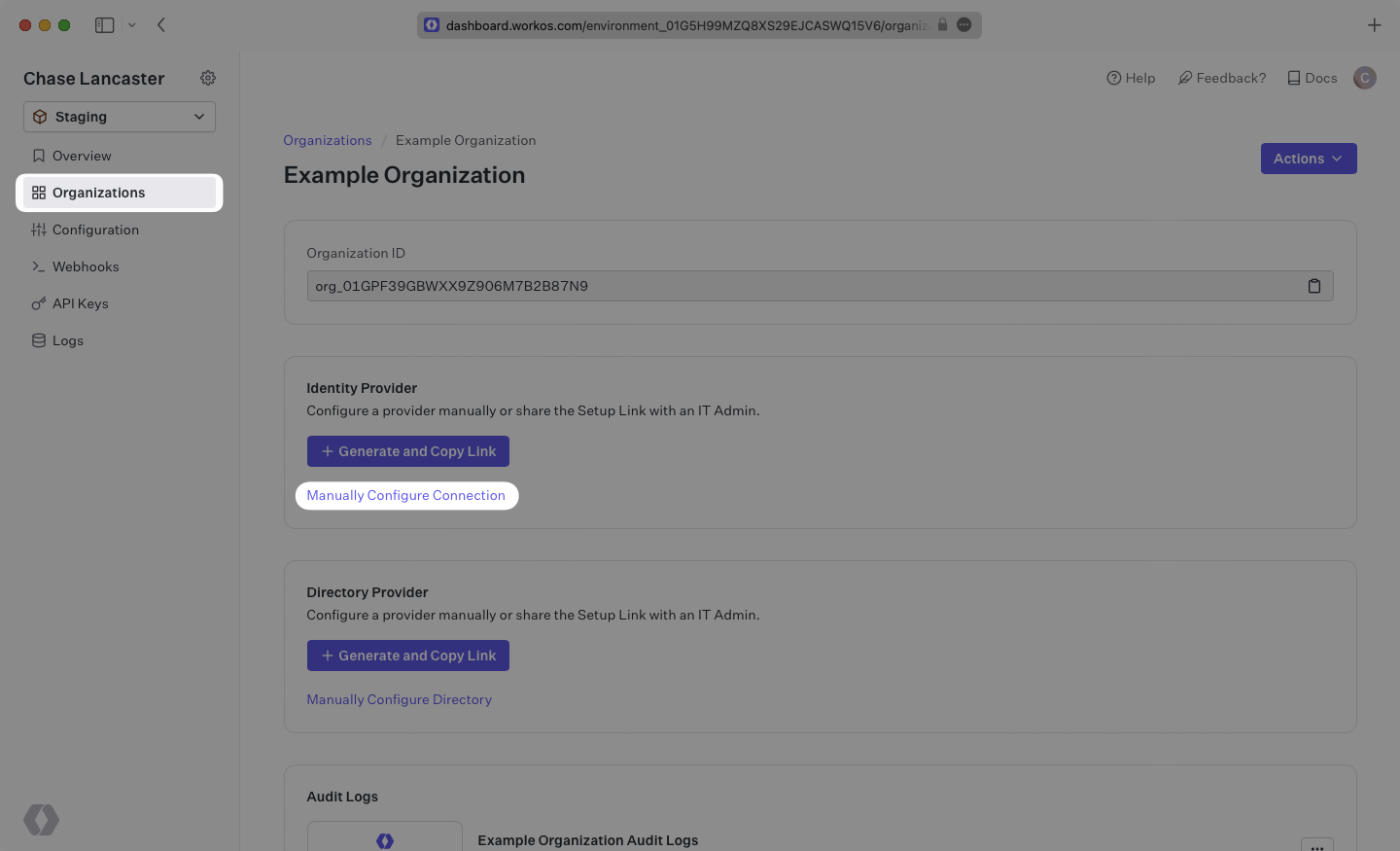
Select “Rippling SAML” from the Identity Provider dropdown, enter a descriptive name for the connection, and then select the “Create Connection” button.
WorkOS provides the ACS URL and SP Entity ID. They’re readily available in your Connection Settings in the WorkOS Dashboard
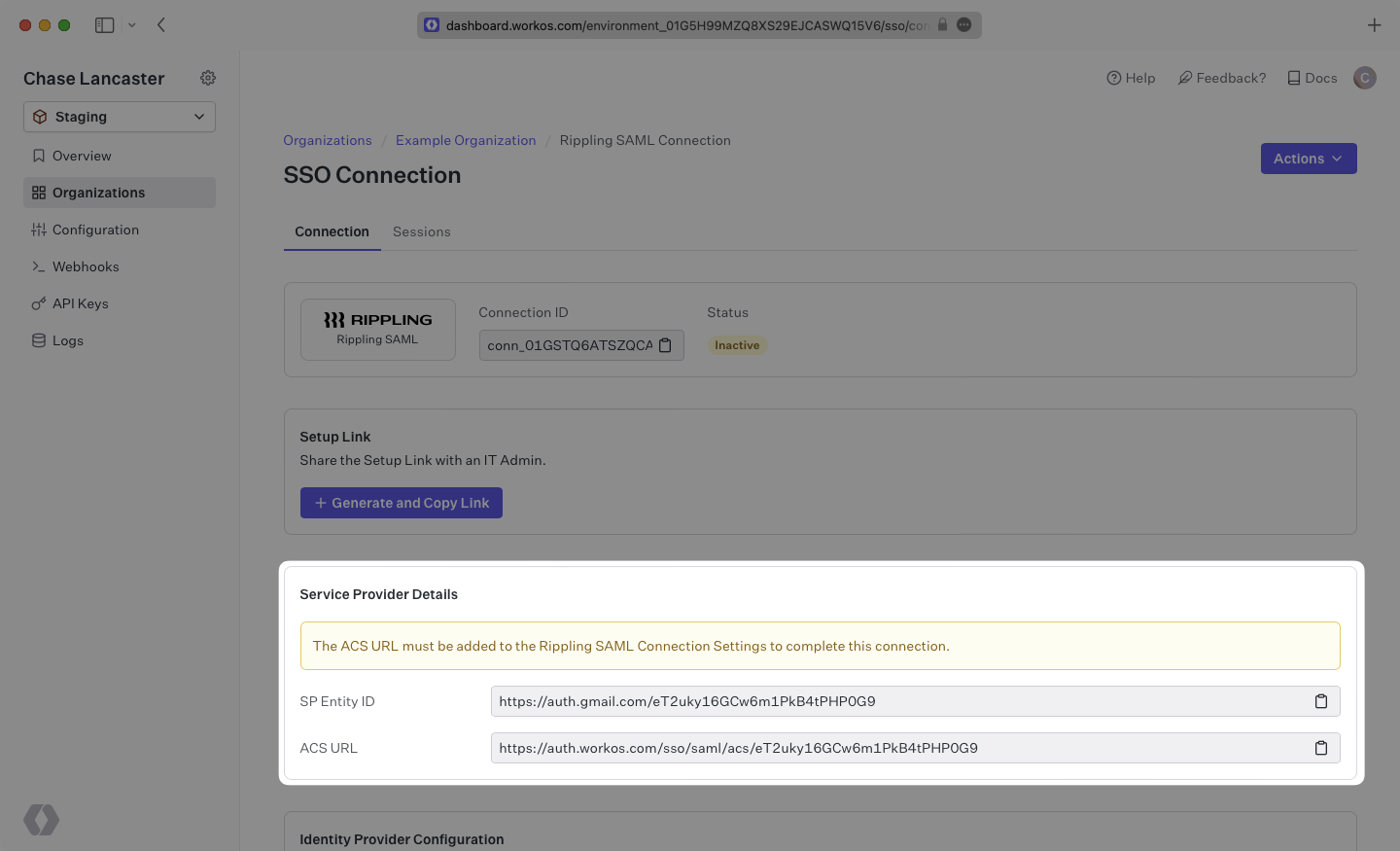
The ACS URL is the location an Identity Provider redirects its authentication response to.
The Entity ID is a URI used to identify the issuer of a SAML request, response, or assertion. In this case, the Entity ID is used to communicate that WorkOS will be the party performing SAML requests to the organization’s Rippling instance.
In order to integrate you’ll need the Rippling IdP metadata.
Normally, this information will come from the organization’s IT Management team when they set up your application’s Rippling configuration. But, should that not be the case during your setup, here’s how to obtain them.
Log in to Rippling as an administrator and select “IT Management” then “Custom App” from the left-side navigation bar.
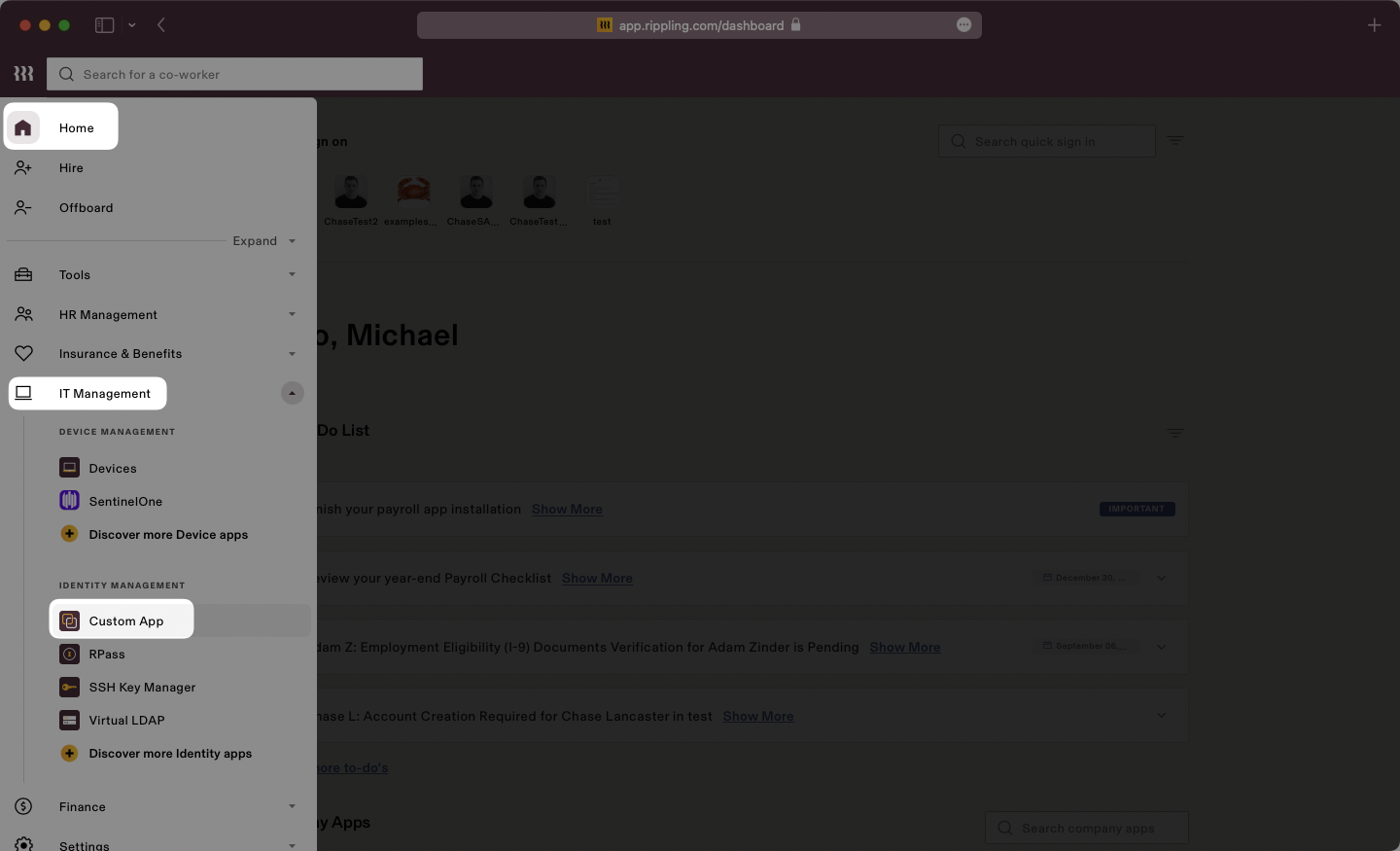
Select “Create New App” to begin creating a new SAML application.
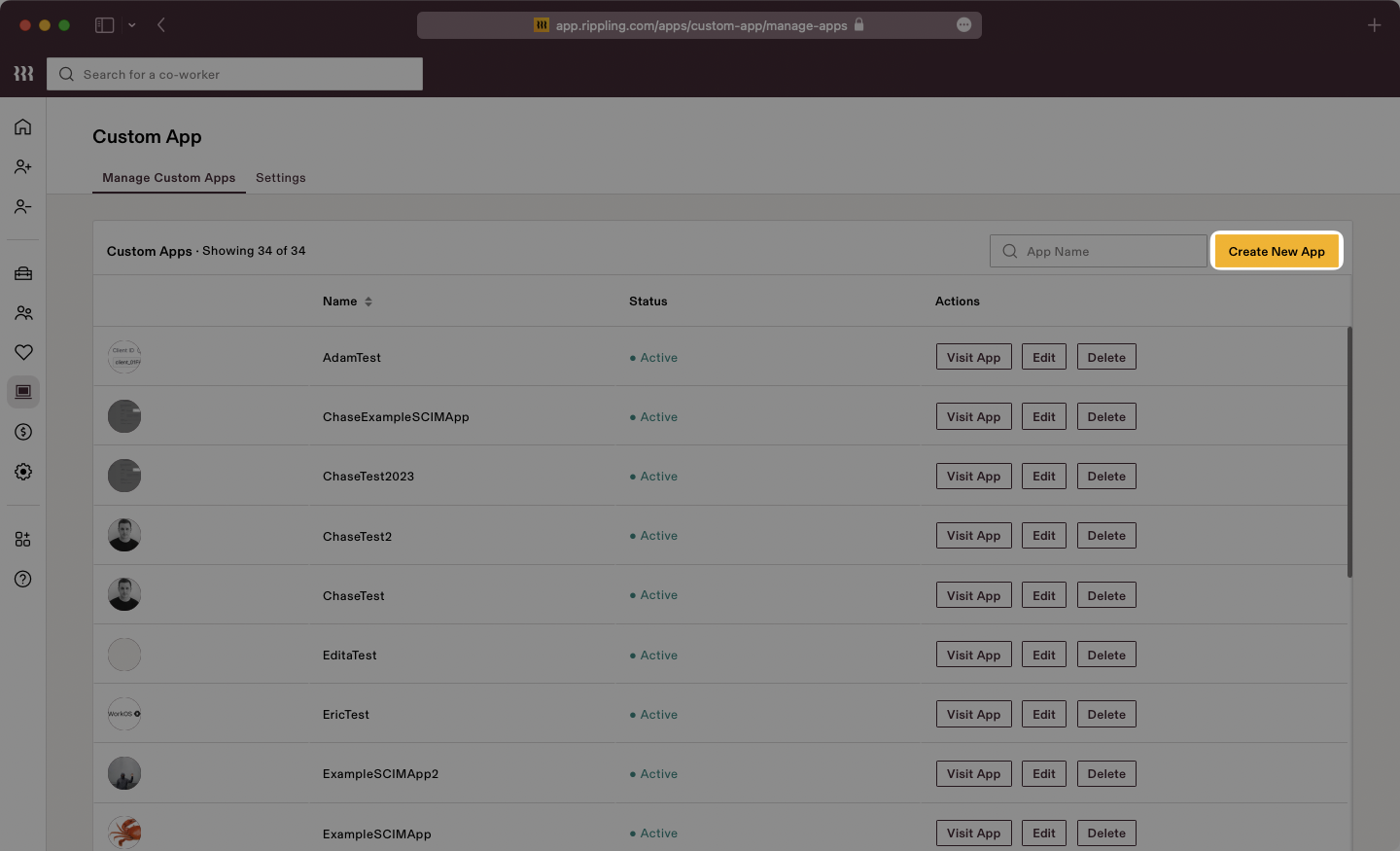
Give the app a descriptive name, select a category, and upload a logo file. Make sure to check the box for “Single Sign-On (SAML)”, then click “Continue”.
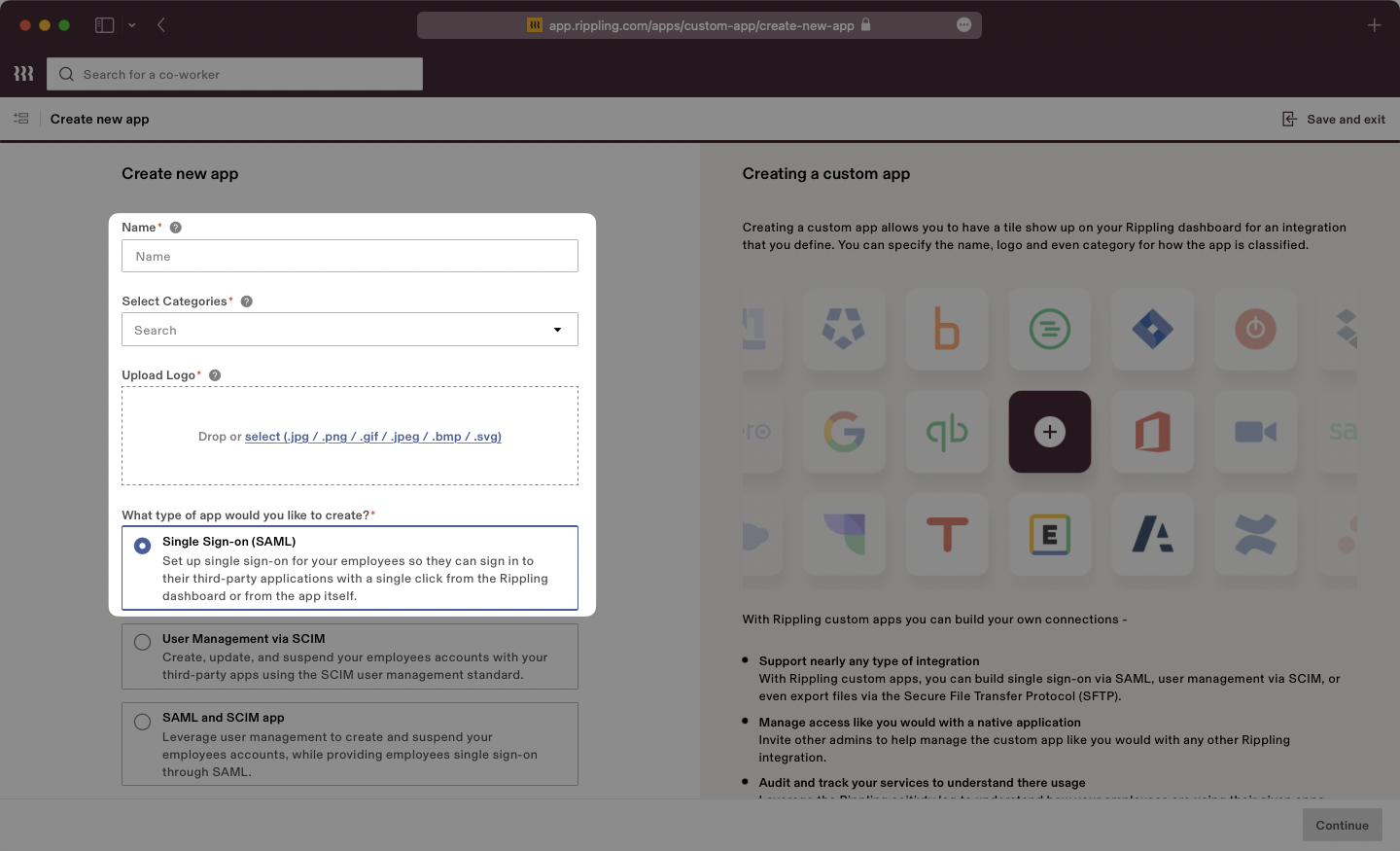
Select the option confirming that you are the Application Admin. Rippling will display a new page with “SSO Setup Instructions” we will use in the next step.
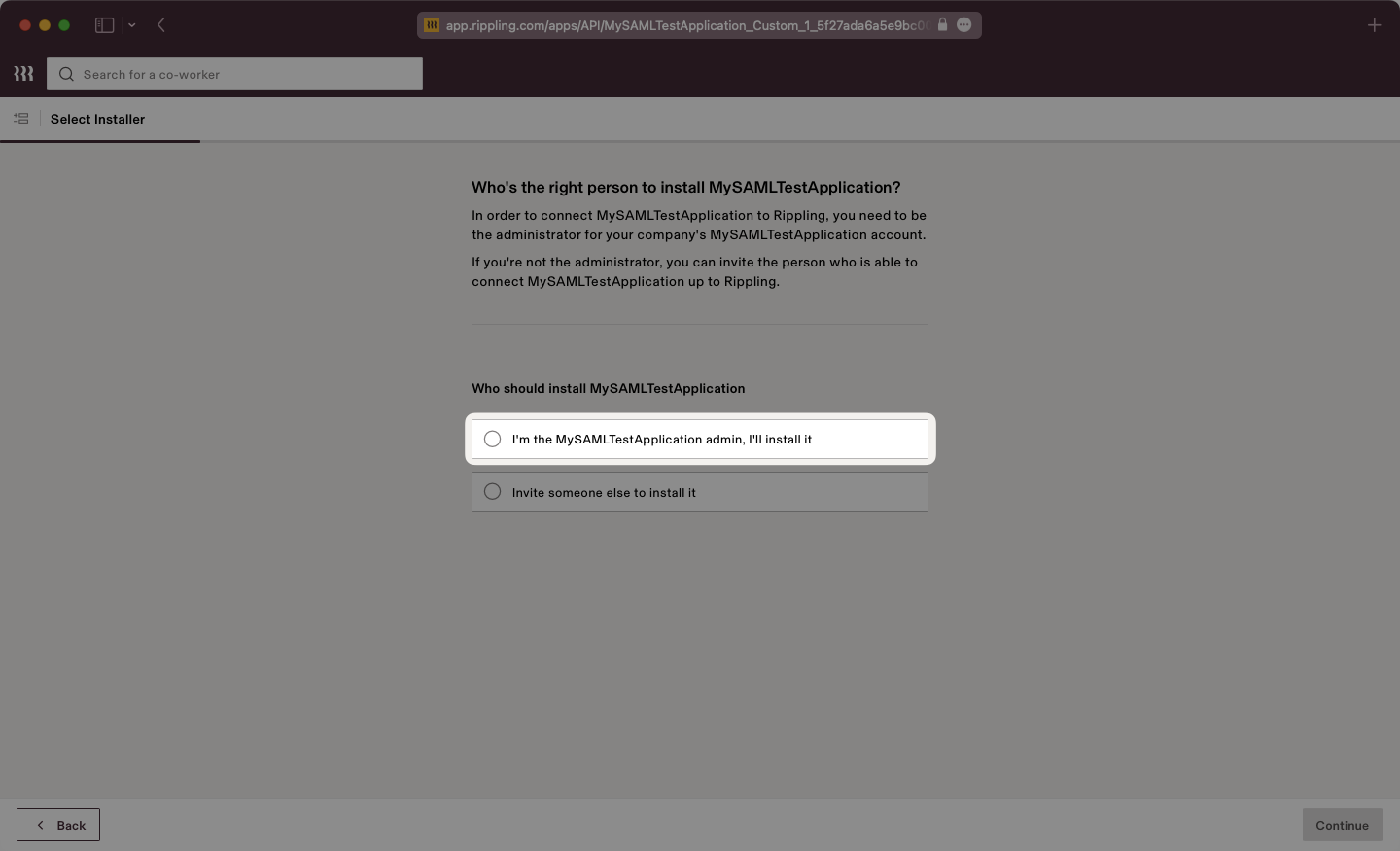
Rippling will present the SSO Setup instructions which will include the IdP Metadata XML file. Click to download the file from Rippling.
Save this file in a memorable place, as we will upload it to the WorkOS dashboard in a later step.
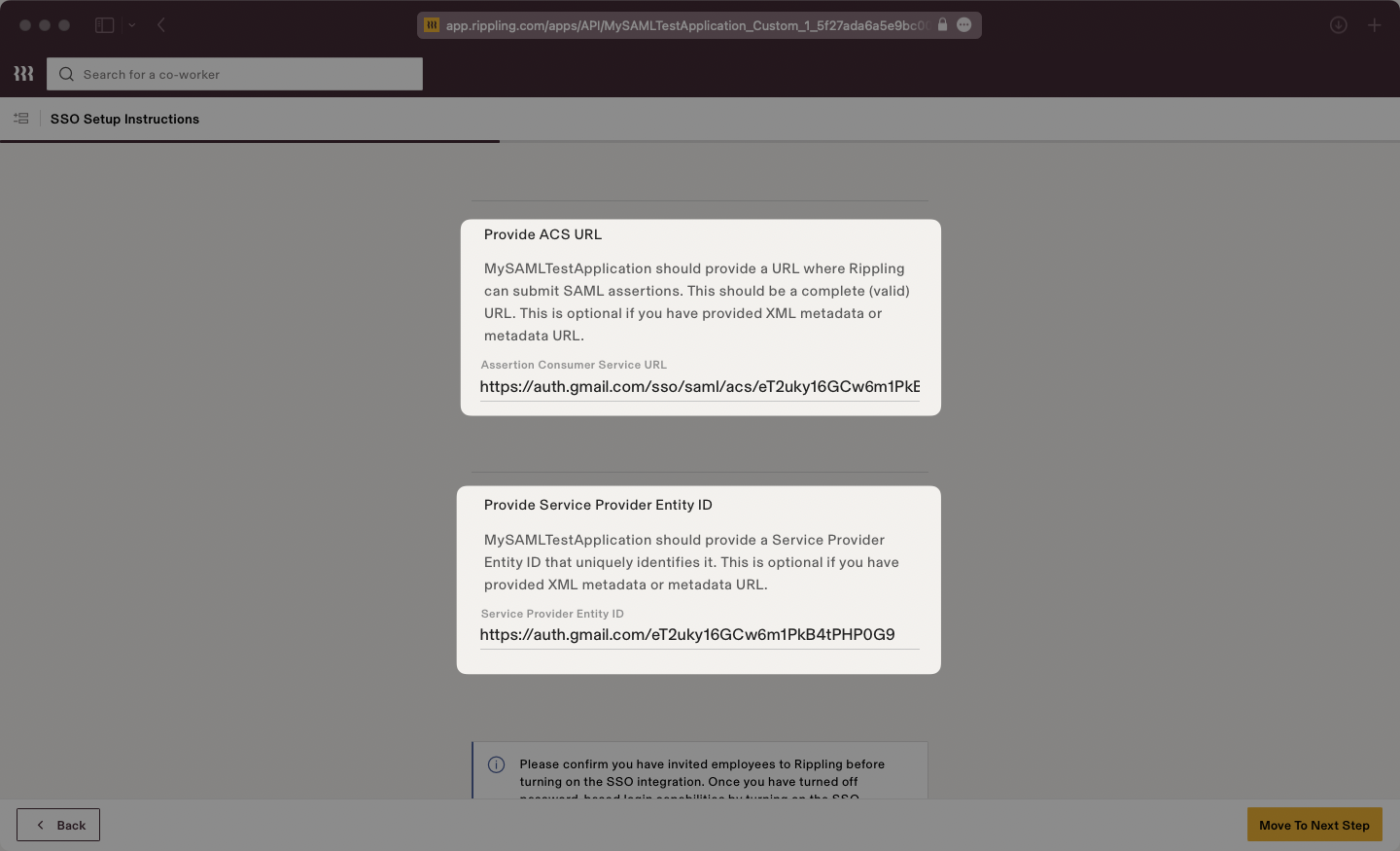
Scrolling down on the SSO Setup Instructions, Rippling will request the ACS URL and Service Provider Entity ID.
Input the ACS URL and SP Entity ID from the WorkOS dashboard into the respective fields.
Once complete, click the “Move to Next Step Button”.
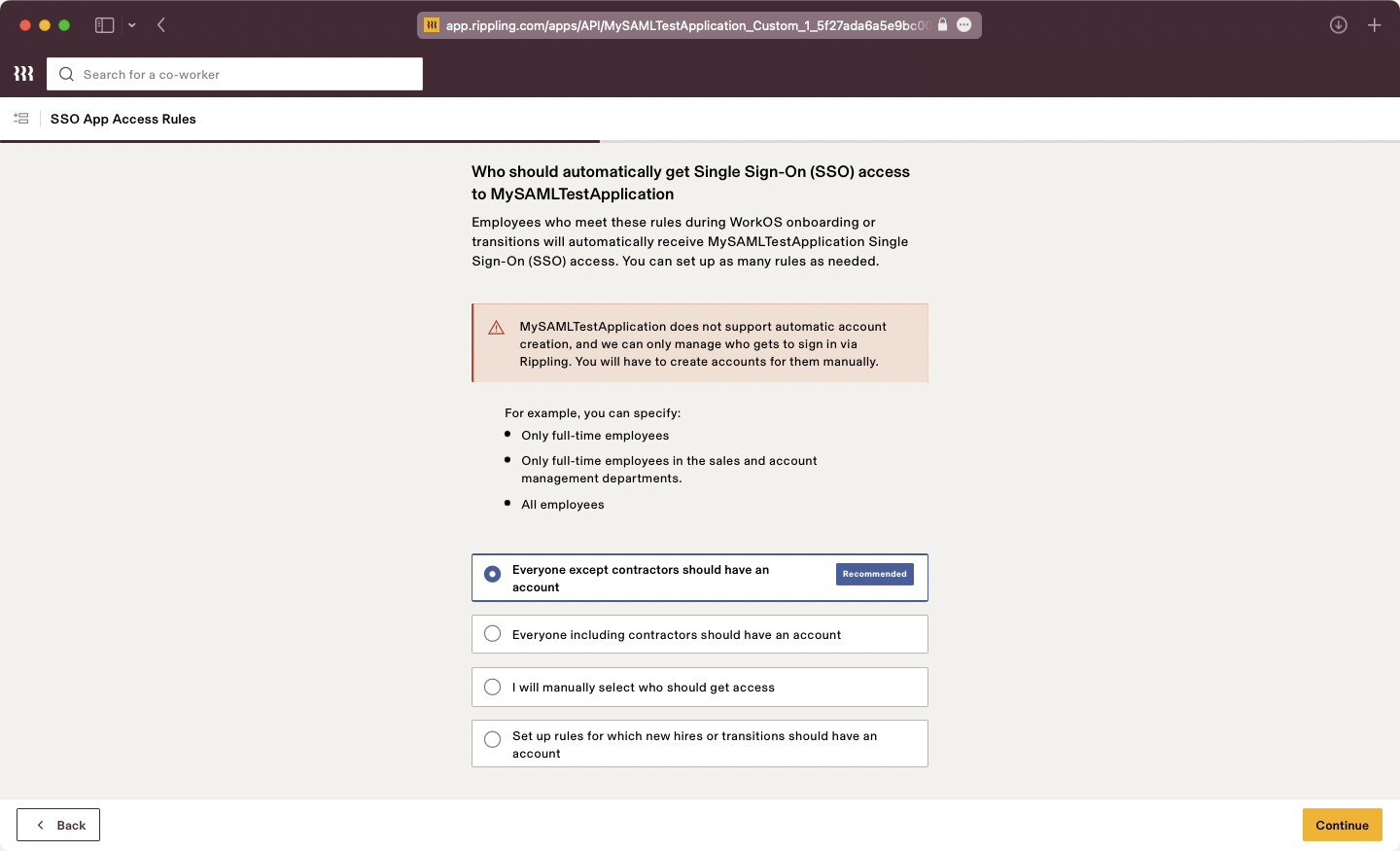
Select your desired Access Rules.
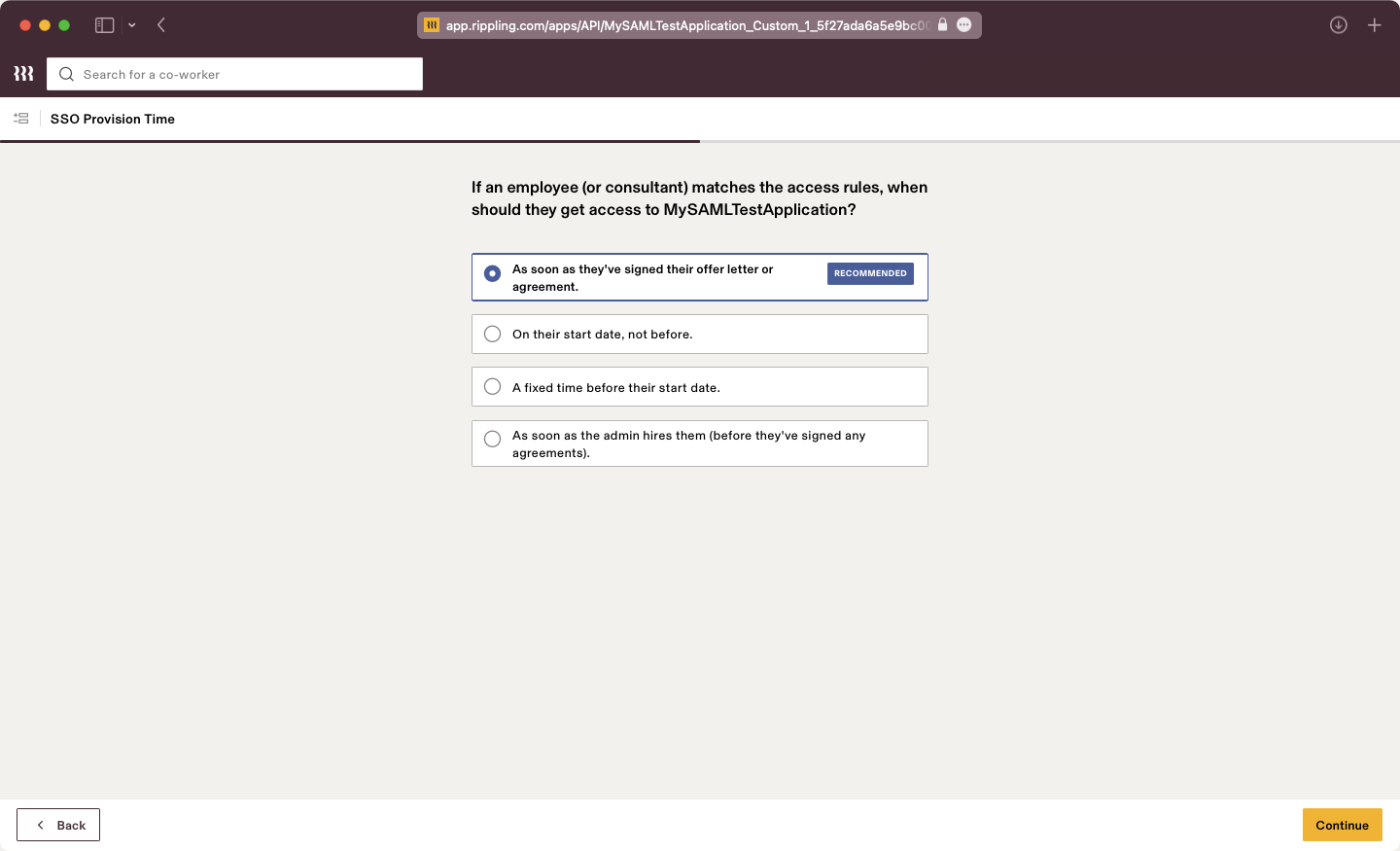
Select your desired Provision Time.
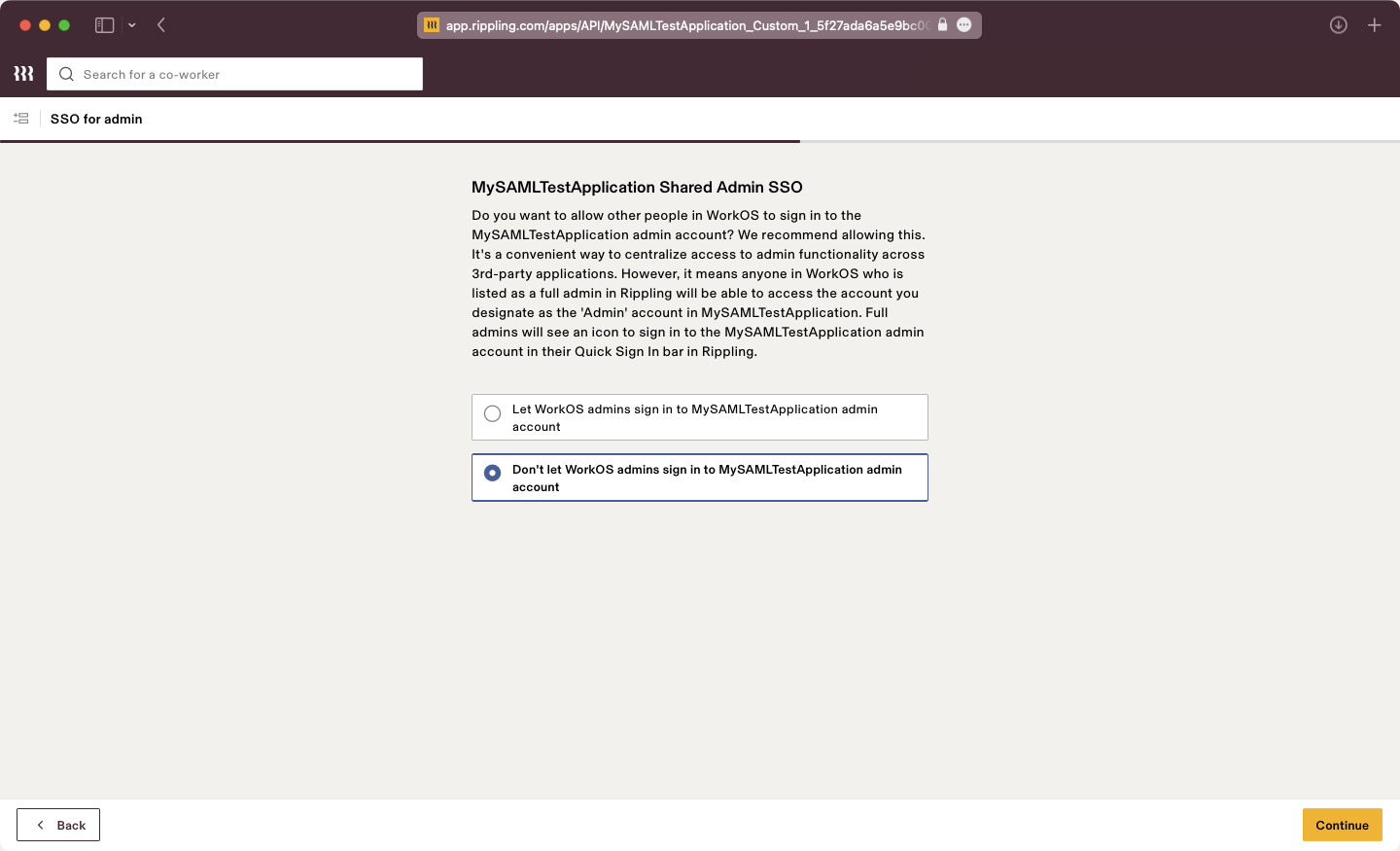
Configure SSO for Admins if necessary.
Configure Group Attributes if necessary.
Verify your SSO integration if you want to test the connection.
Click “Visit the app”. The application settings will be presented, here we will configure the SAML attribute mapping in the next step.
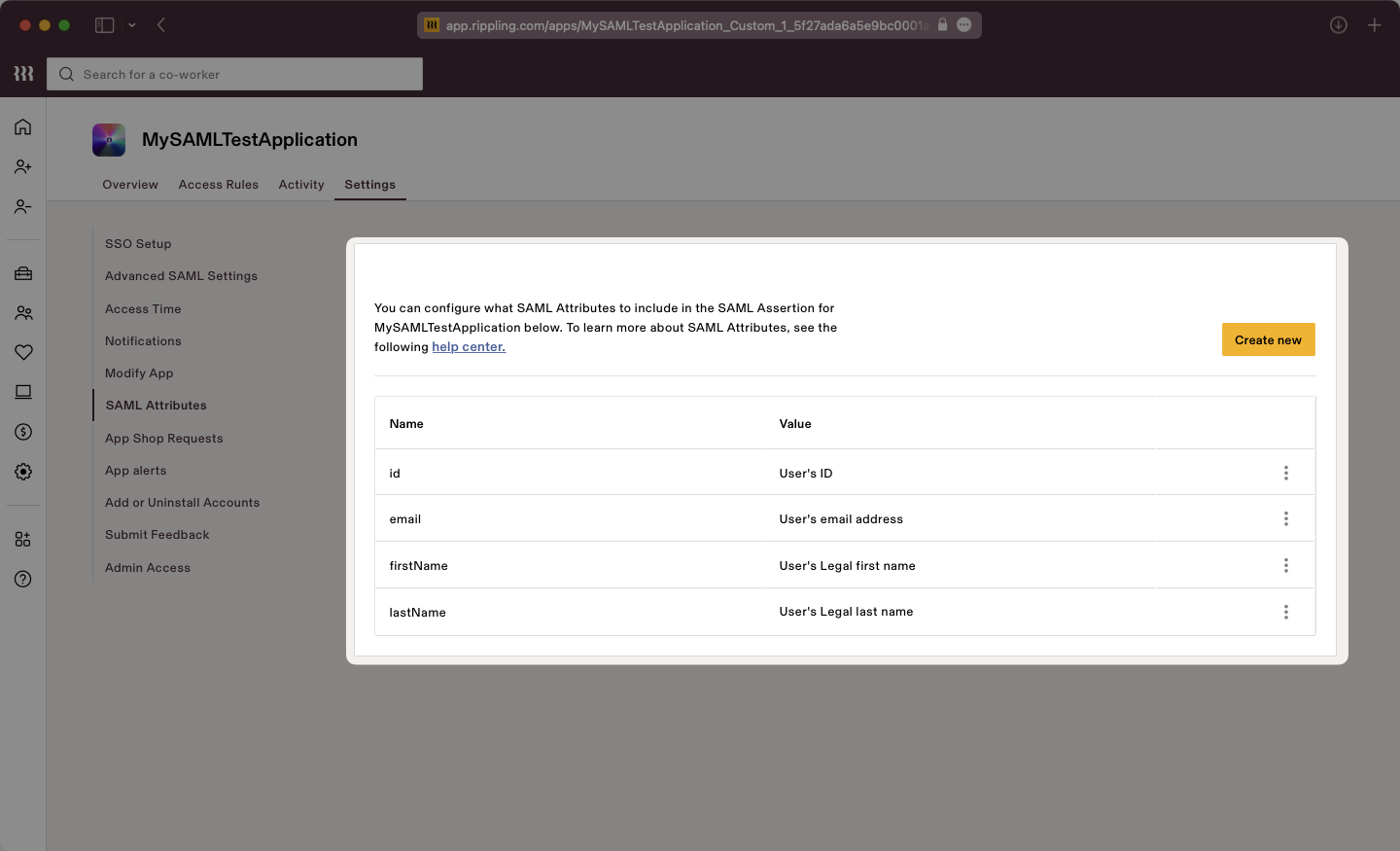
Select the “Settings” tab then on the left navigation select “SAML Attributes” and use the “Create new” button. Add attributes as “Global attributes”.
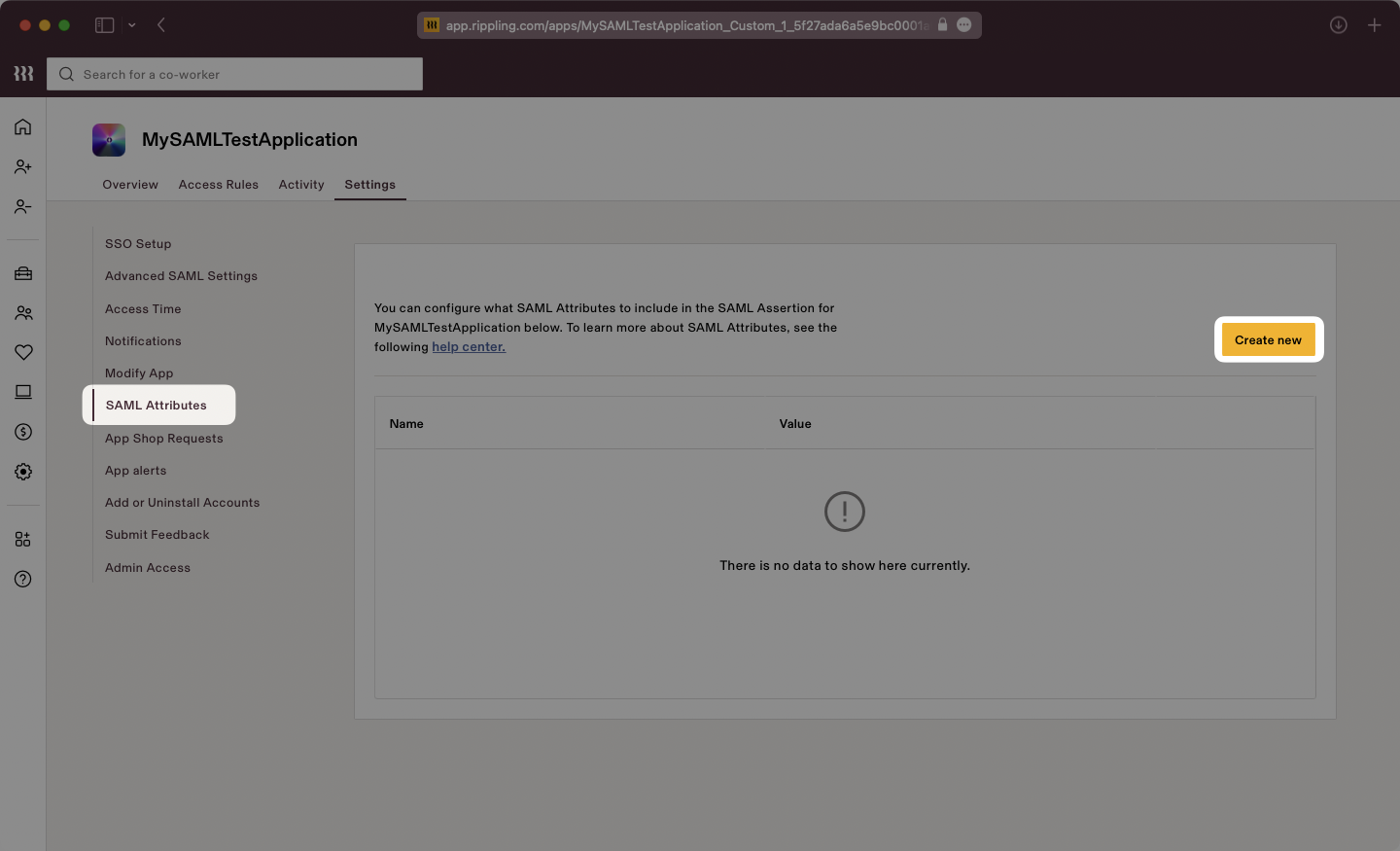
Input the attributes as follows:
id→User’s IDemail→User’s email addressfirstName→User’s Legal first namelastName→User’s Legal last name
Here is a screenshot showing the proper final configuration:
With identity provider role assignment, users can receive roles within your application based on their group memberships. To return this information in the attribute statement, follow the guidance below.
Create a new SAML attribute and select the “Group attribute” type. Click “Continue”.
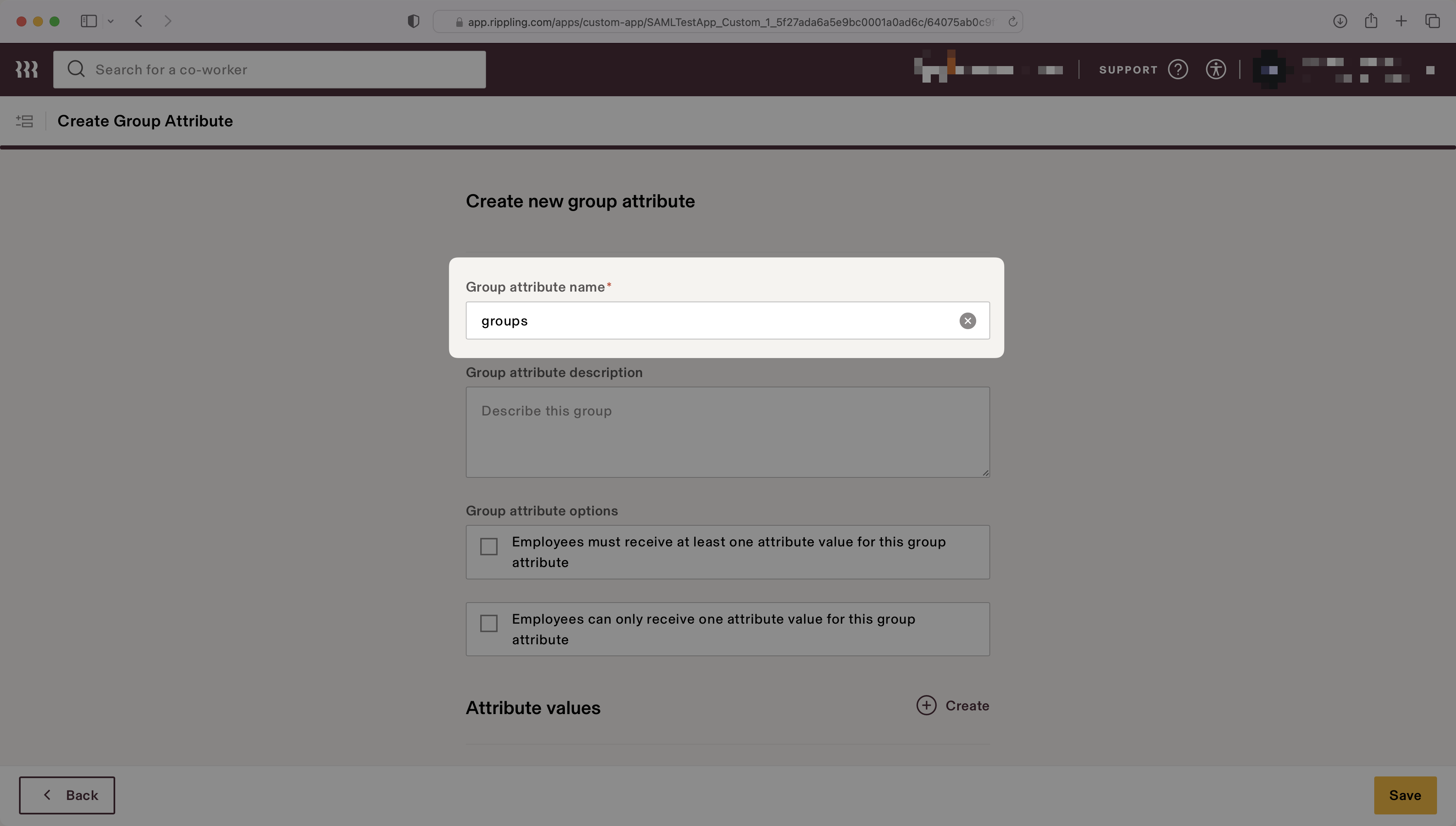
Enter groups for the “Group attribute name”.
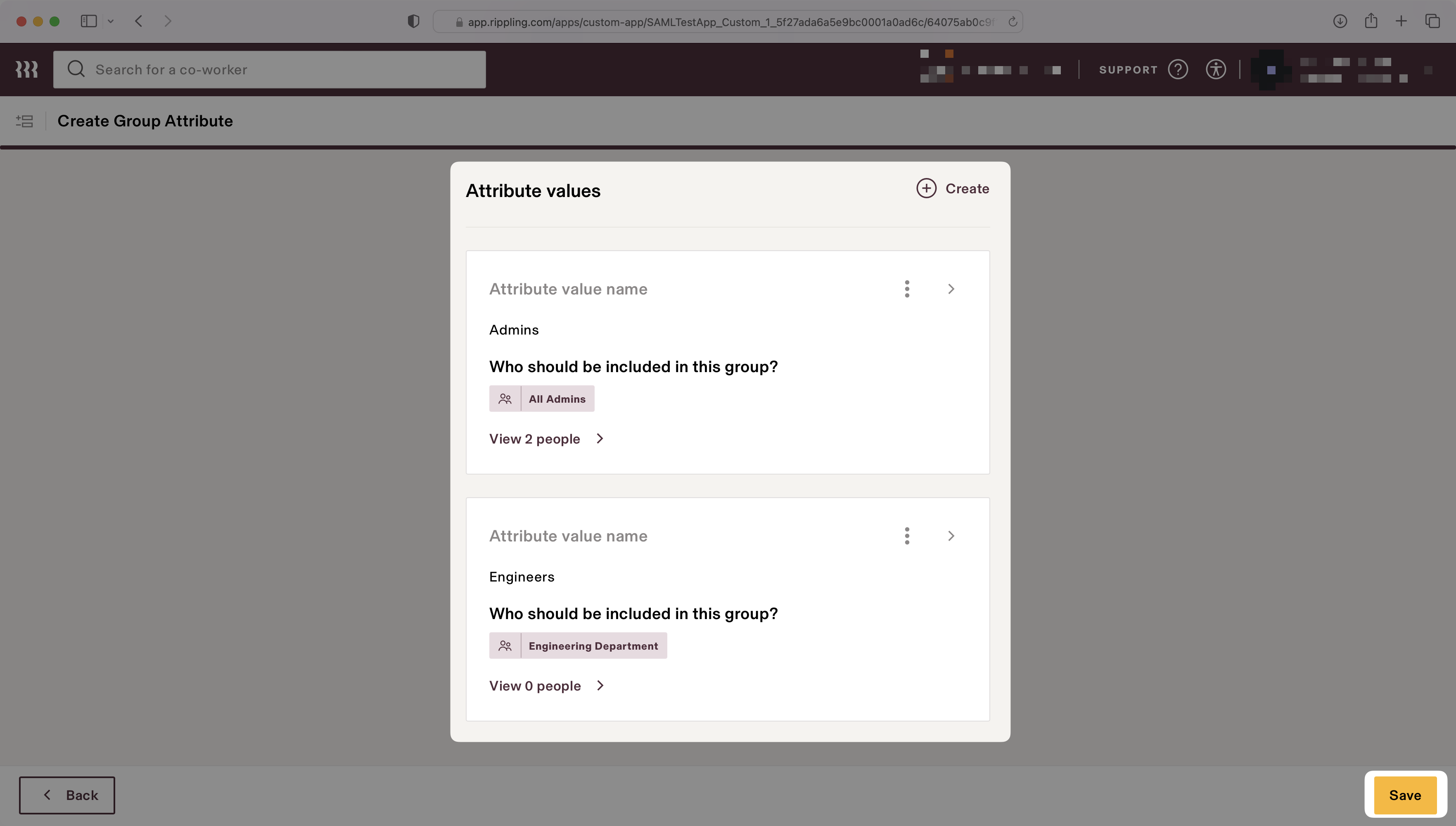
Select the attribute values to map to the group attribute. The example below shows two values, “Admins” and “Engineers”, that map to the “All Admins” user group and the “Engineering Department” user group, respectively.
Finish role assignment set-up by navigating to the SSO connection page in the Organization section of the WorkOS Dashboard. Create SSO groups by referencing the group IdP ID. Then, assign roles to these SSO groups so group members are automatically granted roles within your application.
In the “Settings” tab, on the left navigation select “Advanced SAML Settings” and use the “Edit” button to set “Disable ‘InResponseTo’ field in assertions for IdP initiated SSO” to true by checking the box to enable the setting.
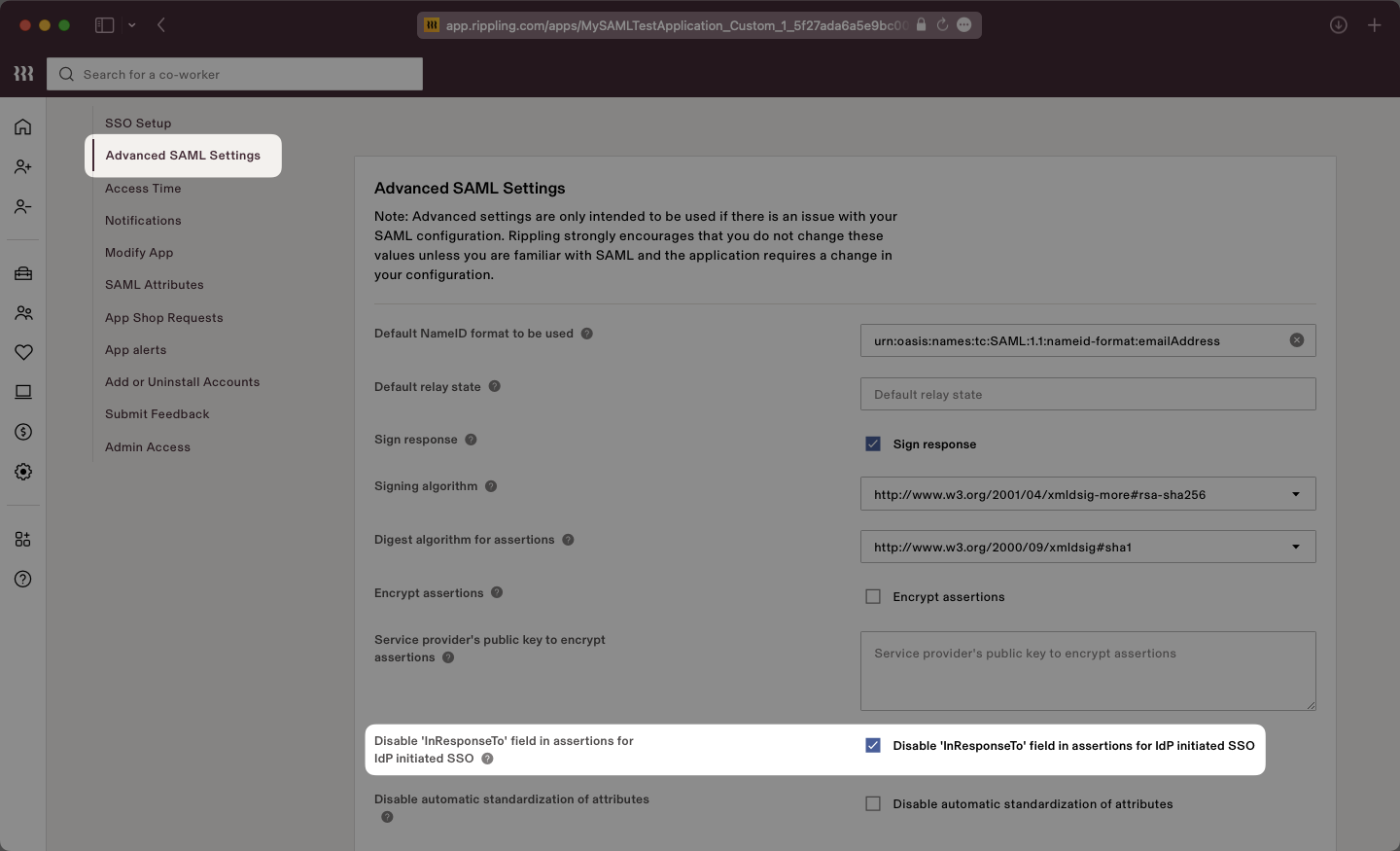
The ‘InResponseTo’ field is primarily used for IdP-initiated SSO and enabling this setting allows WorkOS to accept both SP and IdP initiated SSO from Rippling.
Click the “Save” button to save this setting. In the next step, we will complete the integration by uploading the Metadata XML file to the WorkOS Dashboard.

