API Keys vs M2M Applications: Differences, use cases, and how to decide
A practical guide to choosing the right machine authentication model for your SaaS product.
Modern SaaS platforms often need to let their customers automate workflows, sync data, or integrate with external systems. To support these use cases, developers need a way to issue machine based credentials to their customers. In the WorkOS ecosystem, there are two ways to do this: API Keys and M2M (Machine to Machine) Applications.
Both options provide organization-scoped secrets, but they solve problems in different ways. This article explains how each model works, how they differ, and how to choose the right one for your product.
What problem are we solving?
Your customers’ customers often need a way to authenticate programmatically with your API. That might be a data exporter, a backend service, or a script that pulls usage metrics every hour. In all cases, they need credentials.
WorkOS provides two ways to issue organization-scoped credentials:
- API Keys: A simple, opaque, long-lived secret generated via a built-in widget.
- M2M Applications: A standard OAuth 2.0 flow that issues short-lived JWTs using the client credentials flow.
Both are secure options. The choice comes down to developer experience, operational concerns, and how your customers expect to authenticate.
Let’s see how each one works and when you should use each.
API Keys: Simple, opaque, long-lived tokens
API keys provide a secure way for your application’s users to authenticate with your API. They are designed to be the simplest possible way to issue organization-scoped credentials.
- You drop the API Keys widget into your app.
- Your customers create keys directly in the widget. Each key they create will be scoped to the organization they belong to. So if one of your customers is Cursor and another OpenAI, these two will create and own different secrets. Your customers can assign to new keys the permissions that you configure in the WorkOS dashboard.
- These keys are then used as bearer tokens when calling your API.
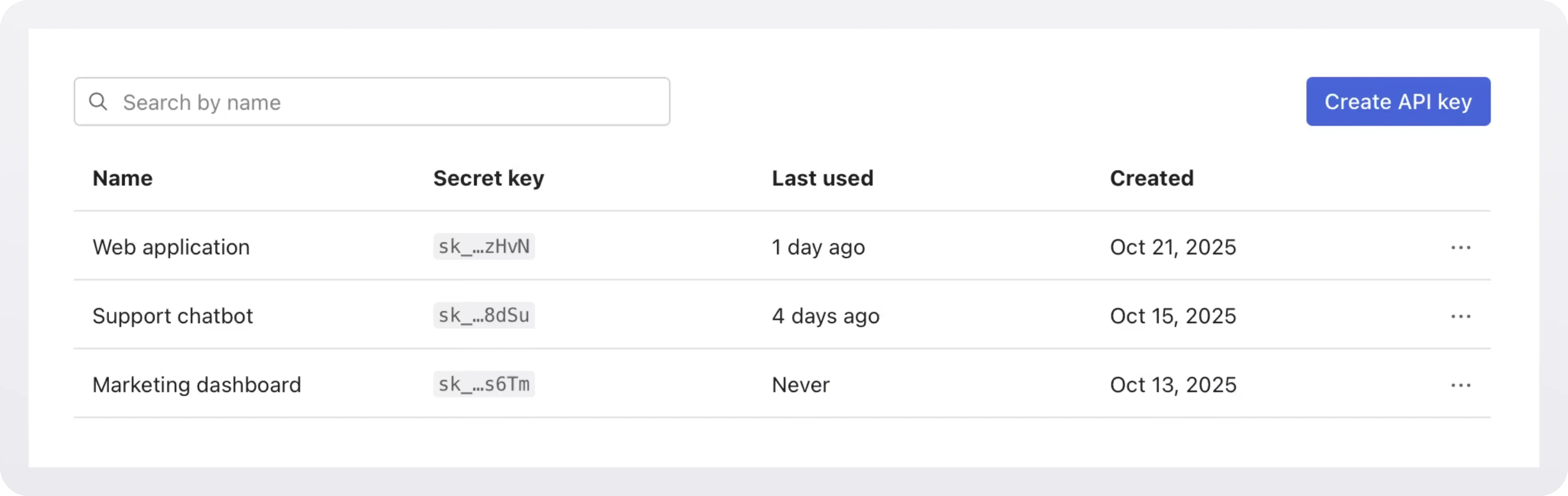
Once your users have created API keys through the widget, your application needs to validate these keys when they’re used to authenticate API requests (typically in the Authorization header), to ensure it’s legitimate and retrieve the associated permissions. You can do that using the WorkOS API . You can also use the WorkOS Node or Next.js SDKs.
When API Keys are a good fit
Choose API Keys if you want:
- Simple, long-lived tokens.
- A UI widget for managing keys without building one themselves.
- Are fine with making a request to the WorkOS API to validate the token.
These characteristics make API Keys ideal for developer experiences where ease of use matters.
Learn more:
- API keys documentation
- API keys widget documentation
- WorkOS API keys: Let your customers build integrations without building the infrastructure
- ERC demo
M2M applications: OAuth-based, short-lived, JWTs
Machine-to-machine (M2M) applications are designed for use-cases where clients are other services, such as one of your customer’s applications, and they use the OAuth 2.0 client credentials flow. Instead of having a static long-lived secret, your customer uses their client ID and client secret to request short-lived access tokens (JWTs) from WorkOS.
Your app can use the Token Endpoint to get an access token which them your customers can use to access your API. Each access token will contain an org_id claim which represents the third-party you are granting access to via the M2M application (i.e., the Id of the Organization that represents your customer in WorkOS).
Whenever your customer uses this JWT to call your API, you need to validate it using the JWKS for your environment. Alternatively, you can use the Token Introspection API to synchronously check whether a token is still valid.
When M2M applications are a good fit
Choose M2M Applications if you:
- Want short-lived tokens in requests.
- Prefer JWTs, where validation could avoid a request to the WorkOS API if the application has a cached JWKS.
- Have some requirement to use the OAuth client credentials flow.
This model works well for backend-to-backend integrations, enterprise workflows, and high-scale environments.
Learn more about M2M applications:
Similarities and differences
API keys and M2M applications are similar in the following ways:
- Both authenticate machine clients such as backend services or scripts.
- Both are scoped to an Organization in WorkOS.
The differ in the following ways:
- Format
- API Key values are opaque strings.
- M2M issues JWT access tokens.
- Lifespan
- API Keys are long lived until revoked.
- M2M access tokens are short lived, although the client secret used to obtain them is long lived.
- Creation flow
- API Keys are created only by end users through the API Keys Widget.
- M2M Applications are created in the WorkOS Dashboard.
What should you choose?
Here is a quick way to decide which option fits your product.
In practice, many teams support both so customers can choose what fits their environment.
Putting it all together
If you want to offer a simple, frictionless way for your customers to generate organization scoped secrets, API Keys are the right choice. They integrate cleanly through the widget, offer configurable permissions, and remove the need for customers to build their own UI.
If your customers prefer OAuth or have requirements around short lived tokens, auditing, or JWT validation, M2M Applications will feel more familiar and more powerful.
Both provide secure, organization scoped machine authentication. Choose the model that best aligns with your customers’ tooling and security expectations.