Creating stronger passwords with AuthKit
A technical deep dive on how AuthKit ensures strong user passwords including best practices and security tips.
While companies are moving towards more secure authentication options like magic links or single sign-on (SSO), passwords still remain essential for verifying the user identity.
AuthKit strengthens the password creation process by offering real-time feedback and customizable policies, helping users balance security with ease of use.
Read on to learn:
- Elements of strong passwords
- How to create strong passwords with AuthKit
- Best practices for enterprise-level password security.
Let’s start by explaining what a strong password is.
What is a strong password and why does it matter?
A strong password is difficult for others to guess (especially automated systems) yet easy for the user to remember. It’s designed to resist various types of attacks, such as brute force or dictionary attacks.
For individual users, a strong password keeps personal information safe. For enterprises, the stakes are significantly higher. A weak password can expose entire systems, compromise sensitive client data, and lead to costly regulatory penalties, risking both financial losses and reputational damage.
What elements do secure passwords contain?
Creating a secure password requires a combination of different elements to ensure it can withstand various types of attacks.
Here’s what makes a strong password:
- Length: A minimum of 12 characters is typically recommended, with 16 characters being ideal for enterprise-level security.
- Complexity: Use a mix of uppercase and lowercase letters, numbers, and special symbols (like !@#).
- Avoid common patterns: Steer clear of sequential numbers (1234) or keyboard patterns (qwerty). These are easy targets for attackers.
- Unique phrases: Combine random words or phrases that aren’t easily guessable. For example, “Blue$Sunflower!92” is far more secure than “Password123.”
- No personal information: Avoid using easily accessible information like names, birthdays, or addresses, as these can be easily guessed or found through social engineering.
How AuthKit simplifies the creation of strong passwords
Here’s how it helps:
Automatic password validation
AuthKit uses the zxcvbn-ts library to evaluate the strength of passwords in real time. It provides feedback based on several factors:
- Entropy calculation: It estimates the number of guesses needed to crack the password by calculating its entropy, a measure of randomness and unpredictability.
- Pattern recognition: It identifies common elements in passwords, such as dates, repeated characters, sequences, and keyboard patterns.
- Dictionary checks: It compares passwords against a database of common words and phrases.
- Attack-time estimation: It provides an estimate of how long it would take an attacker to crack the password under different conditions.
In practise, AuthKit only has 6 types of password validation errors, as demonstrated here:
Customizable password policies
Through the WorkOS Dashboard, you can define specific password requirements, such as minimum length, character variety, or restrictions on reused passwords. This flexibility allows you to set policies that meet your specific security needs.
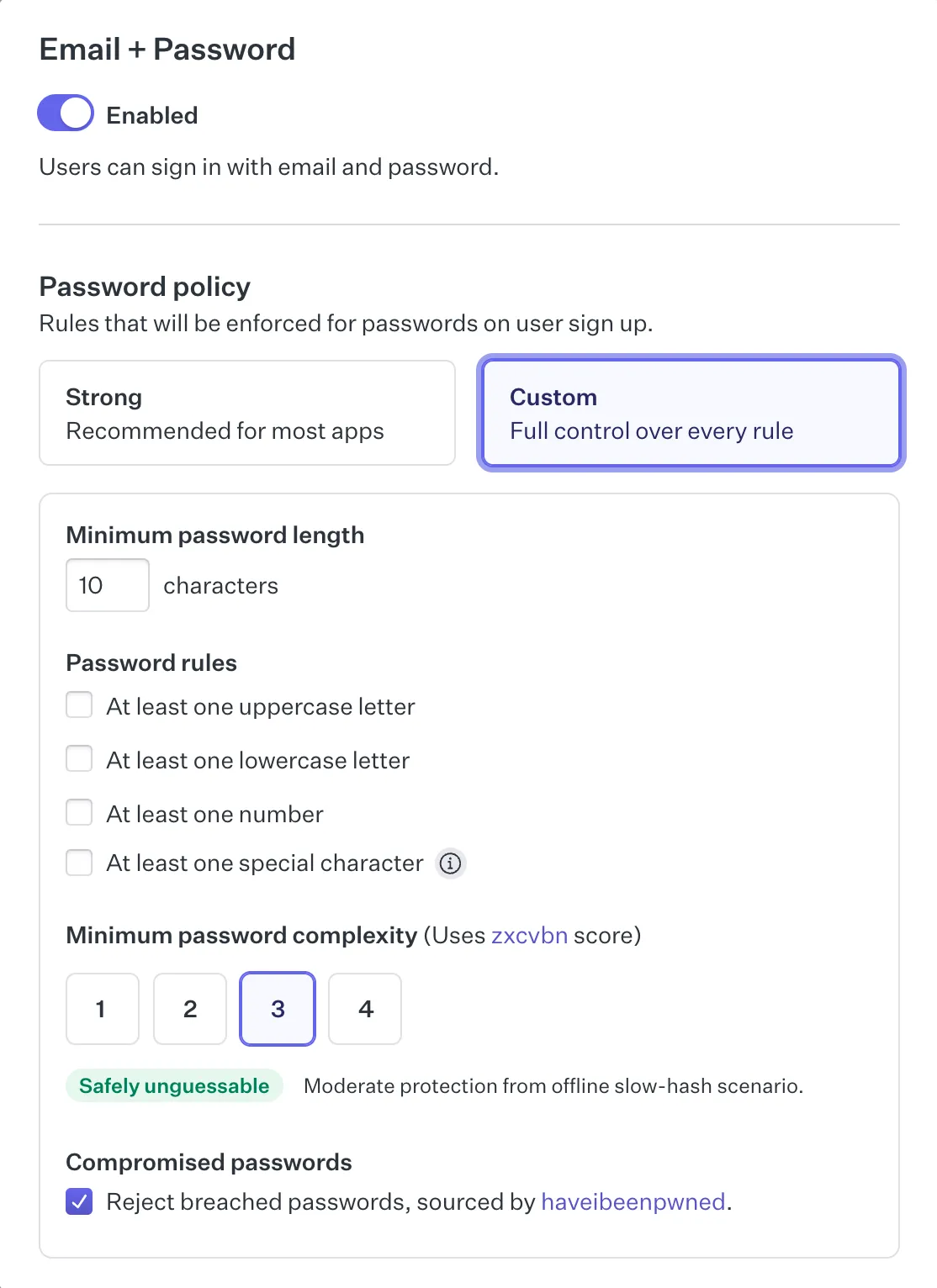
Real-time feedback
Instead of forcing users to submit a form only to find out their password is weak, AuthKit provides immediate, user-friendly feedback. This is possible because the validation happens entirely client side. Users need to click the “Continue” button to start the validation, as validating while still typing is annoying. On page load, the password configuration set from the WorkOS dashboard is retrieved and zxcvbn-ts is ready to validate passwords without requiring a server roundtrip.
This approach improves user experience and encourages users to create stronger passwords without the frustration of repeated trial and error.
Checks for compromised passwords
AuthKit queries the 'haveibeenpwned' API to identify passwords that have been exposed in previous data breaches and exactly how many times that particular password has been seen before.
The function below takes the password, hashes it, and based on the prefix of the hash queries the haveibeenpwned API to find how many times the password has been found in recorded breaches. WorkOS only passes the hash prefix to ensure that the full password isn’t leaked to any external services.
This extra bit of information goes a long way to educate your app users on the dangers of insecure passwords.
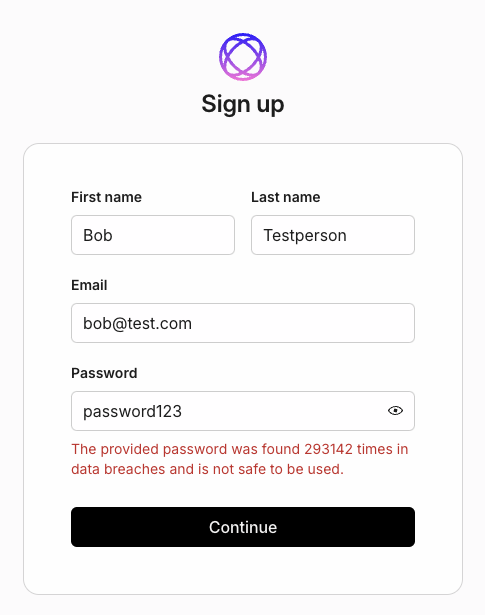
It’s one thing to know your password was found in a breach, and it’s another to find out that it’s potentially been found hundreds or thousands of times.
Easy-to-understand messaging
If a password is insecure, AuthKit will use easy-to-understand language to explain why. For example, here’s the message displayed when a password contains the email address the user is trying to sign up with:
Support for multi-language feedback
For businesses with a global user base, AuthKit offers feedback messages in multiple languages, making it easier for users worldwide to understand why their password choices need improvement.
How to create strong, unique passwords with AuthKit
You can use the default password policy for AuthKit or craft your own in the WorkOS dashboard.
Here’s a guide to creating strong, unique passwords using AuthKit if you decide to customize the policy:
- Start with a long password: AuthKit allows you to set minimum password lengths through the WorkOS Dashboard. A password should be at least 12 characters long, but 16 characters is ideal for enterprise-level security.
- Mix character types: A mix of uppercase and lowercase letters, numbers, and special characters is required to increase password complexity. AuthKit’s validation will flag passwords that don’t include a variety of character types, prompting users to add more complexity. Example: StRoNg#88*WiNDs.
- Set a strong password complexity value: AuthKit uses the zxcvbn score to determine password complexity. Scores range from one to four — a score of one means a password could be cracked in seconds, while a score of four means it would be significantly more difficult to crack. Set the score to 3 or 4 to ensure passwords are safely unguessable.
- Reject breached passwords: Enable the reject breached passwords option. If a password has been part of a breach, users are instantly notified and prompted to choose a more secure alternative.
Password security best practices for enterprises
Here are some best practices that help ensure strong password security:
- Implement multi-factor authentication (MFA)
You can combine strong passwords with other SaaS authentication methods like MFA to add a second layer of security. MFA requires users to provide two or more verification factors — like a password and a code from an authenticator app. Even if a password is compromised, the extra step makes unauthorized access much harder, especially against credential-stuffing attacks.
- Ensure SOC 2 compliance
SOC 2 is a set of compliance standards that ensure your organization securely manages data to protect the privacy and interests of your clients. Achieving this certification demonstrates a commitment to data security, including how passwords are managed.
- Use strong, unique passwords across all internal systems
A strong password policy requires passwords to be long, include a mix of character types, and avoid common words or easily guessable patterns. Additionally, each system and user account should have a unique password to prevent a breach from compromising multiple systems. Consider using a password manager to ensure these practices are maintained consistently.
- Regularly rotate passwords and review access logs
Regularly update passwords (e.g., every 90 days) and review access logs to monitor user activity. This will help minimize the risk of compromised credentials and quickly detect unauthorized access.
Final thoughts: Strengthening passwords with AuthKit
Developers have to walk a tight line of enforcing strict security rules while also making sure users do not adopt bad habits, like using the same password everywhere or coming up with easily guessable passwords.
Knowing how to create strong passwords is crucial for protecting both user data and enterprise systems.
AuthKit makes this easier with a ready-made, customizable authentication UI that handles password validation for you. The best part is that it can be integrated with minimal code, making it developer-friendly.
To further enhance your app’s security, consider leveraging other essential tools like:
- Audit Logs for tracking user activities and monitoring password changes.
- Directory Sync to ensure all user directories are updated and secure across platforms.
- User Management systems to help control access and enforce strong password policies.
- Admin Portal for centralized management of user authentication and security settings.