EKM vs KMS: An introduction to key management
Keeping your data safe by encrypting them is crucial, but how do you keep the encryption keys safe? Read what EKM and KMS are and how they work together to do exactly that.
In an interconnected world where threats and malicious actors are everywhere, safeguarding sensitive information is more important than ever. And for that, you need encryption. Without encryption, data is vulnerable to data breaches.
Encryption keys are needed for data encryption, and manually managing them can be difficult and error-prone, especially in large organizations with complex IT infrastructures. That’s when EKM and KMS come into play. Encryption keys protect your data from unauthorized access, and EKM and KMS protect the keys from compromise or theft.
Both Enterprise Key Management (EKM) and Key Management Service (KMS) play essential roles in securing data through encryption, offering organizations the tools they need to manage cryptographic keys at scale. Although the terms EKM and KMS are often used interchangeably, they refer to distinct concepts in the broader field of key management.
In this article, we’ll explore EKM and KMS, how they work, and the benefits they provide to organizations seeking to protect their sensitive data.
What is Enterprise Key Management (EKM)?
Enterprise Key Management (EKM) refers to an organization’s processes, tools, and strategies to securely create, store, manage, and distribute encryption keys across its enterprise. EKM is designed to help organizations maintain control over encryption keys for the encryption of sensitive data, ensuring that these keys are kept secure and that only authorized users or systems can access or manage them.
An EKM system manages keys across an organization’s environment, handling their entire lifecycle. An EKM system is responsible for:
- Key provisioning: EKM doesn’t actually generate or store encryption keys (the KMS does this, as we will see in the next section), but it does track which keys are being used for what types of data across an organization’s systems. An organization might want to provision a new key for each enterprise customer or tenant, or provision separate keys based on data type (e.g., a key for credit card numbers and a separate key for PII). This way, you end up with a lot of keys, and EKM is the system responsible for tracking and managing which key is being used for what (which tenant, which data type).
- Key distribution: This involves securely distributing encryption keys to the systems and applications that need them while ensuring that only authorized entities can access them.
- Key rotation and expiration: Regularly rotating keys is essential to maintaining security. EKM helps automate this process, ensuring that old keys are replaced with new ones to minimize the risk of a security breach.
- Key auditing and compliance: EKM systems help track and monitor key usage for compliance with data protection regulations such as GDPR, HIPAA, and PCI-DSS. This involves maintaining detailed logs of key access, creation, and deletion.
- Key destruction: Once encryption keys are no longer needed or have reached the end of their lifecycle, they must be securely destroyed to prevent any future access to encrypted data.
What is Key Management Service (KMS)?
Key Management Service (KMS) is a centralized platform for generating and storing encryption keys. It simplifies and automates the process of creating, storing, and managing encryption keys used to secure data in an organization’s IT infrastructure.
KMS typically provides organizations with a set of tools to control key creation and storage, often integrating with other security services and applications. KMS can be part of a broader security infrastructure, ensuring that sensitive data is always encrypted and that keys are managed securely.
The key features of KMS are:
- Key creation and management: KMS allows organizations to create and manage keys for encrypting data, often supporting various types of keys such as symmetric (AES) and asymmetric (RSA) encryption.
- Key storage: Secure storage is crucial to prevent unauthorized access to keys. EKM solutions often use hardware security modules (HSMs) or software-based encryption to store keys securely. HSMs are designed to resist physical and logical tampering. These modules provide key generation and storage functionality and are often certified to comply with rigorous standards like FIPS 140-2 or Common Criteria. HSMs also ensure that even if attackers gain physical access to the device, they cannot extract the keys.
- Key durability: Losing encryption keys is bad, and KMS systems do their best to ensure this never happens due to hardware failure. This involves a combination of physical security (via HSMs), data redundancy (use multiple copies of keys spread across geographically distributed locations or fault-tolerant storage systems), encryption, backup and recovery strategies, and strong access controls.
- Integration with cloud services: Cloud-based KMS solutions integrate with various cloud services (e.g., AWS, Google Cloud, Microsoft Azure) to provide seamless encryption and key management for applications hosted on these platforms.
- Access control: KMS platforms offer robust access control mechanisms, allowing organizations to define who can create, access, or manage specific keys based on roles or permissions.
- Automated key rotation: KMS platforms support automatic key rotation, ensuring that keys are changed regularly without manual intervention. This helps maintain security and meet compliance standards.
- Audit logging: Most KMS platforms include detailed logging features that track who accessed or used a key, providing an audit trail for compliance and security monitoring.
- Scalability and flexibility: KMS solutions are designed to handle the needs of both small and large organizations, providing scalable solutions for managing hundreds or thousands of keys in diverse environments.
What’s the difference between EKM and KMS?
While EKM and KMS are closely related, they differ in scope and implementation:
- EKM is a comprehensive approach to managing encryption keys across an entire enterprise. It includes not just the tools and technologies for key management but also the policies, processes, and controls that govern key usage, storage, and rotation.
- KMS is the tool or service that enables the implementation of these key management practices. It provides the infrastructure and capabilities for key creation, storage, access control, and auditing. KMS solutions are always part of an enterprise-wide EKM strategy, specifically supporting the technical aspects of key management.
In essence, EKM is the broader strategy and framework, while KMS is the specific tool or service used to implement that strategy.
How EKM systems work?
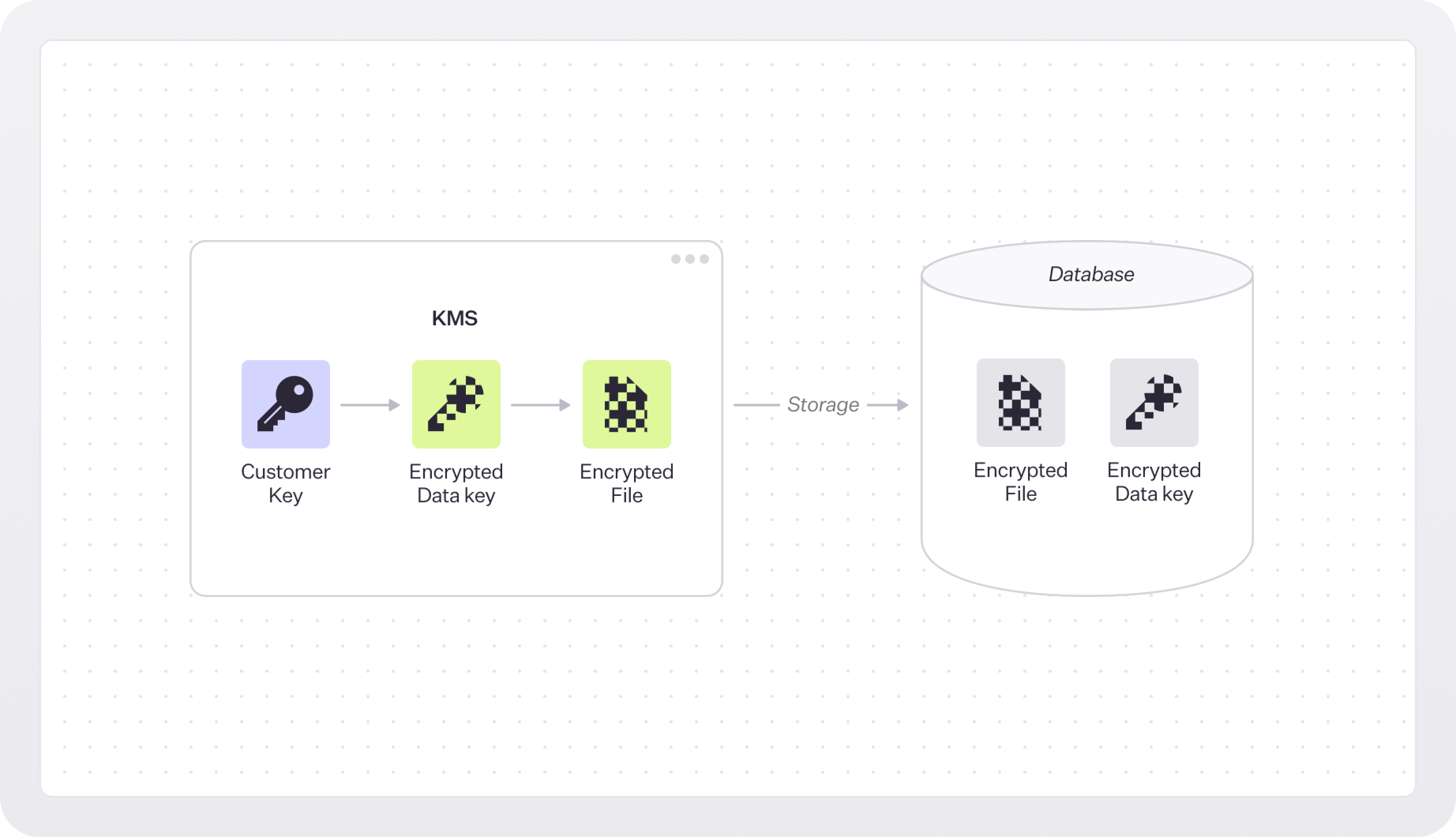
An EKM system uses two types of keys: customer managed keys and data keys.
The customer managed key is used to encrypt the data key, and then that encrypted data key is used to encrypt the data. This process is called key wrapping. The encrypted data key is stored alongside the data and, therefore, cannot be lost.
Here’s the process, step by step:
- A customer managed key is generated by the KMS. The customer has full control over the key (hence the “customer managed” part) and can use it to encrypt and decrypt data via an API that the KMS provides. There are actually multiple keys generated, not only one. Usually, there is a key for a specific data set or group of data objects (e.g., files or records). Time-based keys are also common.
- Then, data keys are generated. These keys are used to encrypt or decrypt sensitive data.
- The customer managed key is used to encrypt the data key.
- The encrypted data key is used to encrypt the data and is then stored alongside the data (in what is called an encrypted envelope). This keeps the data very portable, even if the data moves the key will move with them.
- When the data needs to be accessed, the customer managed key is used to unwrap (decrypt) the wrapped data key. Once the data key is decrypted, it can be used to decrypt the actual data.
There are several benefits to using this approach:
- Security: By encrypting the data keys with a customer managed key, you're ensuring that even if an attacker gains access to the data and the encrypted data key, they won't be able to decrypt the data unless they also have access to the customer managed key. Data keys are never stored in plain text, reducing the chances of exposure.
- Separation of duties: This approach also separates the management of data and encryption keys. The data key can be specific to a dataset or application, while the customer managed key is typically a higher-level key, making it easier to rotate and manage at a more strategic level. This enables efficient key lifecycle management.
- Key rotation: Key rotation becomes easier and more secure. If you need to rotate the customer managed key, you can simply encrypt new data keys with the updated customer key, without needing to decrypt the data itself. This reduces the complexity and risk of needing to re-encrypt large datasets every time a key is rotated.
For more details on how EKM systems work see this video.
Benefits of EKM and KMS
- Enhanced data security: Both EKM and KMS help organizations ensure that sensitive data is encrypted and protected from unauthorized access by managing the encryption keys.
- Compliance with regulations: Many industries are subject to stringent data protection laws, such as GDPR, HIPAA, and PCI-DSS. EKM and KMS help organizations meet these regulatory requirements by ensuring proper key management practices, including auditing, key rotation, and access control.
- Scalability: As organizations grow and handle more data, managing encryption keys manually becomes impractical. Both EKM and KMS provide scalable solutions to manage large volumes of encryption keys efficiently.
- Operational efficiency: Automating key management tasks, such as key rotation and expiration, reduces the administrative burden on IT teams and ensures that security practices are followed consistently.
- Risk reduction: By centralizing key management, EKM and KMS help reduce the risk of human error, which could lead to accidental exposure or loss of encryption keys.
- Simplified integration: Cloud-based KMS solutions integrate seamlessly with other security tools and services, making implementing encryption across cloud platforms and applications easier.
Conclusion
Both Enterprise Key Management (EKM) and Key Management Service (KMS) are crucial for ensuring that encryption keys are managed securely and efficiently.
EKM is a broader strategy that encompasses the processes and policies for managing encryption keys across an enterprise, while KMS refers to the specific service or platform used to implement those practices.
Together, they help organizations safeguard sensitive data, maintain compliance with regulations, and reduce the risks associated with key management in today’s increasingly digital world.