MCP.shop Demo: How WorkOS Powers Identity and Auth for AI Agents
Tobin South demonstrates that enterprise-grade identity and authentication for AI agents isn't a future problem—it's solved today, with WorkOS AuthKit.
This post is part of our Enterprise Ready Conference 2025 series, highlighting the key demonstrations and announcements from the event. Check out our full event recap to see how enterprise AI infrastructure is evolving.
The Demo That Proved AI Identity Is Already Here
Early in the Enterprise Ready Conference program, Tobin South from WorkOS's AI Agents team took the stage with a deceptively simple demonstration.
He showed the audience MCP.shop—a working e-commerce application where users could browse and purchase WorkOS merchandise entirely through a conversational interface powered by ChatGPT's Apps SDK.
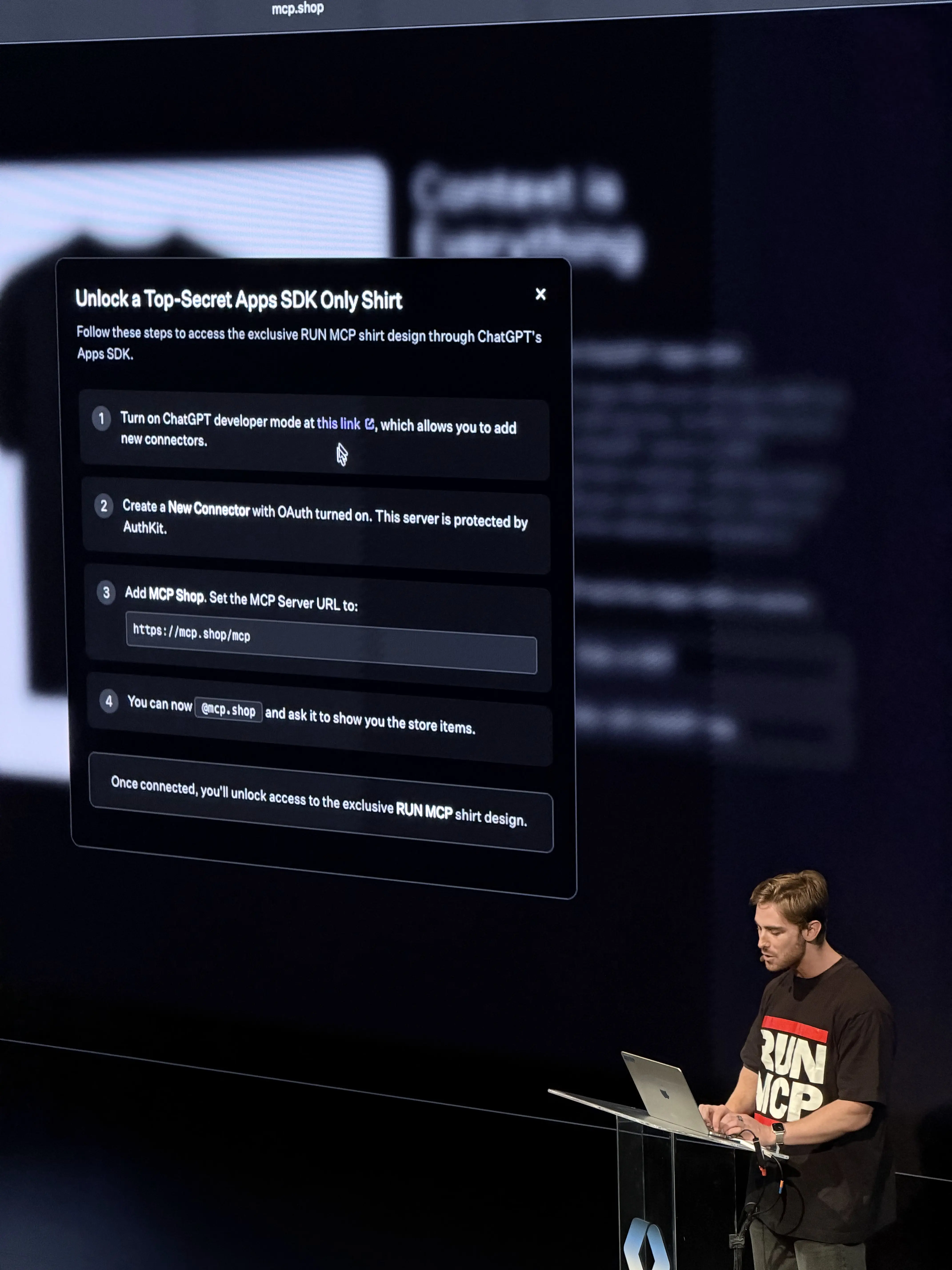
What made the demo remarkable wasn't the shopping experience itself. It was what was happening behind the scenes: WorkOS AuthKit providing full enterprise-grade identity and authentication for an AI-powered application.
Tobin's demonstration walked through the complete user flow of ordering a t-shirt through a chat interface.
The key insight: AI agents need the same identity and access control infrastructure that traditional applications require. When an AI assistant places an order on your behalf, it needs to know who "you" are, what you're authorized to do, and leave an audit trail of what actions were taken.
Why Identity Matters for AI Applications
Most conversations about AI applications focus on model capabilities, prompt engineering, or agent orchestration. But when it comes to deploying AI into enterprise environments, identity becomes the foundational layer that everything else depends on.
Consider what happens when a user interacts with an AI-powered application:
Authentication: The system needs to verify who the user is before granting access to any functionality or data.
Authorization: Once authenticated, the AI agent needs to understand what permissions this specific user has—what data they can access, what actions they can take, which systems they can interact with.
Audit Trail: Every action the AI takes on behalf of the user needs to be logged with proper attribution. When an agent makes a purchase, updates a database, or sends a message, there needs to be a clear record of who authorized that action.
Session Management: AI interactions often span multiple exchanges over time. The system needs to maintain identity context across these interactions without requiring users to constantly re-authenticate.
Traditional web applications solve these challenges with well-established patterns: OAuth flows, session tokens, JWTs, and role-based access control. The question Tobin's demo answered is whether these same patterns work for AI-powered applications.
The answer is yes—with the right infrastructure.
How WorkOS Powers AI Application Identity
MCP.shop demonstrated the complete integration between WorkOS AuthKit and OpenAI's ChatGPT Apps SDK. The architecture showed how enterprise identity features work seamlessly with conversational AI interfaces:
Universal Authentication: Users authenticate once with WorkOS, and that identity carries through all their interactions with the AI application. Whether they're browsing products, placing orders, or checking order status, the system always knows who they are.
Scoped Permissions: WorkOS's authorization system ensures that AI agents only take actions the user is permitted to perform. If a user doesn't have permission to make purchases above a certain amount or access specific product categories, the AI respects those boundaries.
Token Management: Behind the scenes, WorkOS handles the complex token lifecycle—issuing, refreshing, and revoking access tokens as needed. Developers don't need to build their own OAuth flows or manage credential storage.
Compliance-Ready Logging: Every interaction generates audit logs that meet enterprise compliance requirements. When an AI makes a purchase on a user's behalf, there's a clear trail showing who initiated the action, when it occurred, and what permissions were in play.
Building on ChatGPT Apps SDK
Tobin's demonstration showed how WorkOS integrates with OpenAI's Apps SDK specifically, but the architectural pattern applies broadly. The Apps SDK provides the framework for building custom applications that integrate with ChatGPT, and WorkOS AuthKit plugs in as the identity layer.
This combination lets developers focus on building their AI application's unique functionality rather than implementing authentication and authorization from scratch. Instead of spending weeks building OAuth flows, session management, and audit logging, developers can integrate WorkOS and get enterprise-grade identity in hours.
The Apps SDK handles the conversational interface and LLM integration, while WorkOS handles the security-critical identity infrastructure. It's a clean separation of concerns that accelerates development while maintaining enterprise security standards.
The Identity Challenge Most AI Companies Face
One of the recurring themes throughout Enterprise Ready Conference was that AI companies face a paradox: their core technology moves faster than any software category in history, but the surrounding infrastructure needs to be rock-solid before enterprise customers will deploy it.
Identity sits at the heart of this challenge. Building a compelling AI demo is relatively straightforward—you can prototype impressive capabilities in days. But building the authentication, authorization, and audit infrastructure that enterprises require takes months of careful engineering.
Most AI startups would prefer to spend their time improving their model's capabilities, refining their agent orchestration, or building differentiated features. They don't want to become experts in OAuth flows, SAML federation, or RBAC implementation—but enterprise customers won't deploy applications without these capabilities.
Tobin's demo proved that this doesn't have to be a blocker. With WorkOS, the identity infrastructure already exists, battle-tested by thousands of applications and trusted by enterprise security teams.
Connection to Tobin's Later Session
The MCP.shop demo served as a preview for Tobin's comprehensive session later in the conference on identity for AI agents.
The message was consistent across both presentations: enterprise-grade identity for AI applications isn't a future challenge waiting to be solved. It's available now, and companies building AI products can ship with confidence knowing their identity layer meets enterprise security requirements.
Getting Started with WorkOS for AI Applications
For teams building AI-powered applications and wondering how to handle identity, WorkOS provides a clear path forward:
- AuthKit handles authentication with support for email/password, SSO, magic links, and social auth
- Directory Sync keeps user directories synchronized across identity providers
- Admin Portal gives customers self-service management of their organization's users
- Audit Logs provide compliance-ready records of all authentication events
- Fine-Grained Authorization (FGA) enables complex permission models for multi-tenant applications
The same infrastructure works whether you're building traditional web applications or conversational AI interfaces—the identity challenges are fundamentally the same.
The MCP.shop demo at Enterprise Ready Conference showed that the gap between building impressive AI prototypes and shipping enterprise-ready AI products isn't about model capabilities or agent architectures. It's about infrastructure—and that infrastructure already exists.
Watch more demonstrations and sessions from Enterprise Ready Conference 2025 in our full event recap.