Scaling up: How to launch your product with an Enterprise Plan
Think you're ready for enterprise? This guide breaks down the capabilities you need to launch a true Enterprise Plan—and how WorkOS can help you get there.
Launching an Enterprise Plan is a significant milestone for any product.
It signals that your product is ready to meet the demanding expectations of large organizations, with all the bells and whistles they require: ironclad security, meticulous administration, and scalable architecture.
But this leap isn’t just about ticking off features—it’s about delivering trust at scale.
At WorkOS, we’ve helped customers like Anthropic, Perplexity, Vanta, OpenAI, and Webflow unlock enterprise readiness by providing the building blocks they need to launch confidently.
Here's how.
What it means to be Enterprise Ready
Being Enterprise Ready means your product can operate reliably, securely, and flexibly within complex organizational ecosystems.
It’s about meeting the checklists of procurement, IT, legal, and security teams—while offering a seamless experience to end users.
To launch a successful Enterprise Plan, you need to support:
- Enterprise-grade authentication
- Fine-grained user access controls
- Compliance logging
- Automated user lifecycle management
- Self-service administration
- And many more
It also requires scalable infrastructure, sophisticated authorization models, and strong observability.
In short, enterprise readiness is about aligning your product with the operational maturity of your biggest potential customers.
The first building block: Centralized and secure authentication
Enterprise customers demand authentication experiences that are both seamless for users and secure for IT teams.
Single Sign-On (SSO) is often the first requirement in enterprise contracts. It eliminates password fatigue and strengthens security by allowing employees to log in through a centralized identity provider, like Okta or Microsoft Entra ID, reducing risk and simplifying compliance.
Domain capture complements this by automatically routing users to the right workspace based on their email domain, preventing account sprawl and ensuring consistent user management.
These capabilities are often non-negotiable for enterprise deals, serving as the gateway to adoption.
Anthropic leverages WorkOS SSO and domain capture to ensure secure workspace access while maintaining centralized provisioning and management.
Perplexity integrates SSO into its Enterprise Pro plan, enabling quick and secure logins for its customers.
Webflow uses SSO to trigger JIT (just-in-time) provisioning, automatically creating accounts when users authenticate via their IdP.
Controlling who can do what
Once inside the platform, enterprise users need precise control over what each team member can do.
Role-Based Access Controls (RBAC) is often the first step toward enforcing access policies within your application. It allows teams to assign users predefined roles—like admin, viewer, or editor—and restrict access accordingly. For early-stage products or SMB-focused plans, RBAC is sometimes sufficient.
However, when your goal is selling to enterprises, you'll eventually find that RBAC simply doesn’t suffice. Enterprise customers demand highly granular, dynamic permissioning that can adapt to their organizational complexity. That’s where fine-grained authorization comes in.
Fine-Grained Authorization (FGA) helps you move beyond static roles to rich access models that mirror how enterprises actually function. With FGA, you can define policies at the object level—down to individual documents, projects, or teams—and dynamically enforce access rules based on user relationships, roles, or group memberships.
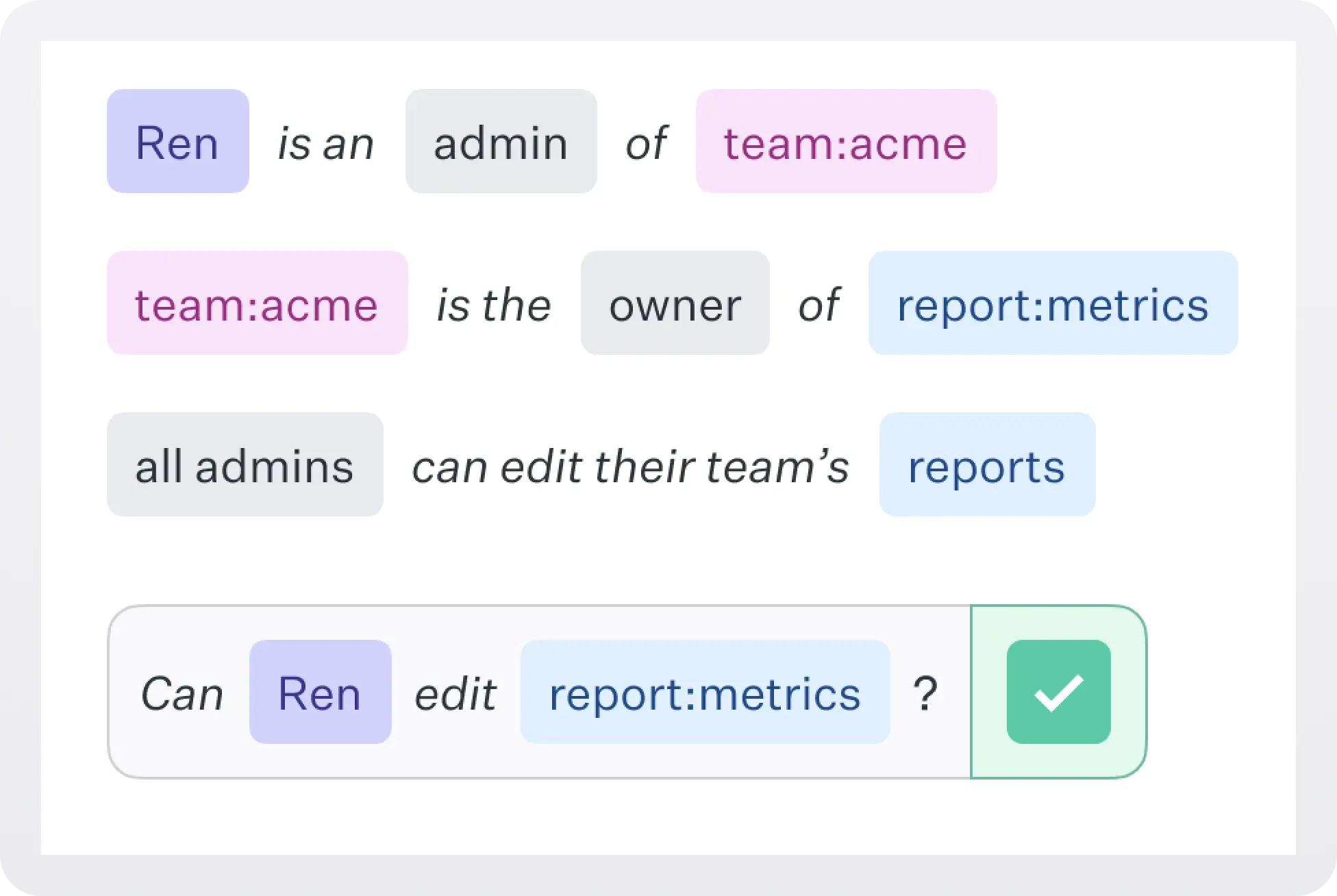
This capability is critical for companies operating in regulated environments or serving customers with strict security requirements. FGA provides the fine-tuned control needed to meet these demands while maintaining scalability and flexibility.
!!Read more: Scaling up: Why Fine-Grained Authorization is key as your product moves upmarket!!
Anthropic, for example, uses these capabilities to ensure workspace owners can tightly manage information flow and access boundaries within their platform.
Automating user onboarding and offboarding
The System for Cross-domain Identity Management (SCIM) is a critical piece of infrastructure when selling into the enterprise. At its core, SCIM enables automatic provisioning and deprovisioning of users, meaning that as soon as an employee joins or leaves a company, their access to your platform is granted or revoked without manual intervention.
This automation reduces administrative overhead, eliminates human error, and significantly strengthens security posture. IT departments no longer have to manually manage user lists or track who should have access to what—everything is handled through their existing identity provider (IdP). This centralization ensures consistency across systems and closes security gaps created by outdated or orphaned accounts.
.webp)
SCIM also enhances the onboarding experience and drives adoption. Employees can gain immediate access to the tools they need on Day 1, pre-configured with the appropriate permissions. On the flip side, offboarding becomes automatic and foolproof—critical for industries where access control is tightly audited.
!!Read more: SCIM: The hidden growth engine behind tools like Slack and Figma!!
More than a convenience, SCIM is often a prerequisite for enterprise adoption. Without it, your platform becomes an outlier in an ecosystem where every other tool is automated and identity-driven. Modern enterprises expect SCIM not only for efficiency but as part of their risk mitigation strategy.
ChatGPT Enterprise rolled out SCIM support to sync employee directories with their workspace, supporting major IdPs like Okta, Microsoft Entra ID, Google Workspace, and Ping.
Webflow uses SCIM for both automated provisioning and deprovisioning, ensuring timely access and removal from workspaces.
Vanta’s Scale plan offers seamless and secure user management across hundreds of cloud apps through SCIM.
Anthropic and Perplexity also use SCIM to simplify access control and enhance operational efficiency.
Tracking activity for compliance and security
Visibility is non-negotiable when it comes to enterprise security. Large organizations must be able to track who did what, when, and where—across every layer of their systems.
Audit Logs are the backbone of this accountability. They provide a tamper-proof, chronological record of system events, user actions, and administrative changes, giving enterprises the transparency they need to meet internal and external compliance standards.
.webp)
These logs are not just helpful for security reviews—they are essential for passing audits, conducting forensic investigations, and ensuring that incident response teams have the necessary context to act quickly. In sectors like finance, healthcare, and SaaS infrastructure, auditability is often a contractual requirement.
Exporting logs into a centralized observability platform or SIEM system enables holistic monitoring, while satisfying IT compliance teams that your product won't be a blind spot in their stack.
Anthropic rolled out audit logs soon to enhance transparency and meet enterprise-grade compliance requirements. These logs will enable their customers to trace activities across their platform for both internal audits and external regulatory standards.
Empowering IT with self-service administration
When selling to enterprises, one of the most overlooked requirements is enabling IT teams to manage your product without relying on engineering. That’s where a purpose-built admin interface becomes essential.
An Admin Portal is an out-of-the-box UI that gives IT administrators a centralized place to verify domains, configure SSO and SCIM connections, and more—all without having to file a support ticket or read through API docs.
Enterprise IT teams are used to having real-time, hands-on control over the software in their stack. If your product doesn't offer a straightforward way for them to manage identity and access configurations, it's likely to stall in security reviews or get rejected outright.
.webp)
Being enterprise-ready means delivering not just capabilities but control—transparently, reliably, and without friction. A self-service admin experience shows that your product respects enterprise workflows and is ready to operate at their scale and expectations.
This turnkey solution empowers enterprise customers to self-serve common admin tasks, reducing the burden on internal engineering and support teams. By integrating the Admin Portal, WorkOS customers improve the admin experience while accelerating time-to-value for enterprise buyers.
Protecting sensitive data
When you're building for enterprises, it's not just about protecting user data—it's about safeguarding every layer of your system, including the secrets that power it. Sensitive configuration data such as API keys, signing secrets, tokens, and database credentials can become high-value targets for attackers if not properly stored and managed.
Enterprise customers will expect you to follow best practices for secret management from day one. Hardcoded secrets or environment variables scattered across services may pass in early-stage environments, but they don't fly in security audits. Enterprises need assurance that any sensitive values are encrypted, access-controlled, and auditable.
!!Read more: When database security is not enough: How the cloud makes application-level encryption a must!!
Having a centralized, secure way to manage these secrets—one that aligns with your broader access policies—is essential to being enterprise-ready. It not only protects your infrastructure from accidental leaks or breaches, but also shows your customers that your internal operations meet their compliance standards.
Expect this to come up in questionnaires during procurement and security reviews—particularly if you're pursuing SOC 2, ISO 27001, or working in industries with strict data handling rules. Without a trusted solution in place, your team could be forced to scramble late in the sales cycle to build stopgap measures. Having secure credential storage from the outset saves time, builds trust, and lays the groundwork for enterprise-scale operations.
Vault is WorkOS’s secure credential storage solution, enabling sensitive configuration values to be encrypted and safely stored. By integrating Vault, companies can isolate and protect sensitive data while maintaining compliance with enterprise security practices. It’s an essential layer for any team preparing for SOC 2, ISO 27001, or similar audits.
Defending against identity threats and abuse
Being enterprise-ready doesn’t stop at knowing who has access—it’s about protecting that access in real time. Enterprises face a constant threat from bots, fraudsters, and malicious actors trying to exploit identity systems. Without automated defenses, your product becomes an easy target.
Real-time protection against identity-based abuse is critical. You need systems that can analyze login behavior as it happens—detecting suspicious spikes in traffic, impossible travel scenarios, credential stuffing attempts, and patterns that indicate fraud or abuse. And more importantly, you need to be able to act on those signals immediately.
This isn’t just about security threats. Abuse can also come in the form of free trial exploitation—when individuals or bots create multiple accounts to continuously access paid features without paying. It can drain resources, skew your analytics, and erode the value of your paid tiers. If left unaddressed, it undermines your business model and raises red flags for enterprise buyers.
!!Read more: What is free trial abuse — and how can you stop it?!!
To meet enterprise expectations, your product should be able to detect and respond to this kind of activity—ideally with out-of-the-box policies and one-click preventions that allow teams to quickly apply protections without building a custom pipeline.
If you're not providing this kind of security posture, you’re asking enterprise security teams to take on more risk than they're comfortable with. And when trust is the product, risk is the fastest deal-killer.
WorkOS Radar protects your app from bots, fraud, and abuse. It can detect, verify, and block harmful behavior in real time. And it helped a prominent AI startup fight the free trial abuse problem they had.
.webp)
How WorkOS can help
If you want to launch your Enteprise Plan, WorkOS offers a complete suite of products and tools to help you ship the exact capabilities discussed above—without reinventing the wheel:
- Single Sign-On (SSO): Securely authenticate users via their identity provider, simplifying access and reducing security risks. Offer SSO for any identity provider that uses SAML or Open ID Connect protocols, with only one integration, and all in a standard OAuth2 connection wrapper.
- Domain Capture: Automatically route users to the correct workspace based on their email domain, avoiding account sprawl.
- SCIM: Automate user and group provisioning and deprovisioning based on your customers’ internal directories. Quickly enable SCIM provisioning from all major corporate directory providers with a single integration.
- Admin Portal: Provide IT teams with a self-service interface to manage SSO, SCIM, domains, and more—no code required.
- Role-Based Access Control (RBAC): Implement structured roles like admin, editor, and viewer to enforce basic access policies.
- Fine-Grained Authorization (FGA): Enable object-level access control that maps to complex enterprise structures. Get a centralized, single source of truth for your permissions that scales with your growth.
- Audit Logs: Capture and export security-grade logs for compliance, incident response, and centralized monitoring.
- Vault: Store and encrypt sensitive data and secrets like API keys and tokens in a secure, access-controlled environment. Integrate directly with major providers like AWS KMS, GCP KMs, Azure Key Vault, and HashiCorp Vault.
- Radar: Detect and prevent identity threats, fraud, and free trial abuse with real-time intelligence and built-in protections.
Each of these tools helps reduce integration time, eliminate security gaps, and deliver the features enterprise customers expect—out of the box.
Conclusion
Launching an Enterprise Plan requires more than just ambition—it demands a solid technical foundation that supports scale, security, and control.
At WorkOS, we provide the infrastructure to help products cross the enterprise chasm.
From SSO and SCIM to audit logs and admin tooling, our platform has powered the growth of leading companies like Anthropic, Vanta, ChatGPT, Webflow, and Perplexity. Whether you're just beginning your enterprise journey or scaling to new heights, WorkOS gives you everything you need to launch with confidence.
Want to make your product enterprise-ready?