August Updates
New this month: Standalone OAuth for MCP, Feature Flags API, BYOK in Vault, disposable email blocking, & more
Standalone OAuth for MCP
Developers building MCP servers are caught between two difficult choices. They can either build a custom authentication system from scratch—spending weeks implementing OAuth flows, token management, and security best practices—or they can rely on basic authentication methods that aren't suitable for production use cases involving real user data.
WorkOS Connect offers a third path that eliminates this complexity entirely. Rather than forcing you to choose between building everything yourself or compromising on security, WorkOS Connect acts as an OAuth bridge that handles all the authentication complexity while letting you focus on what matters most: building your MCP server's core functionality.
Add enterprise auth to your MCP server →
Feature Flags API
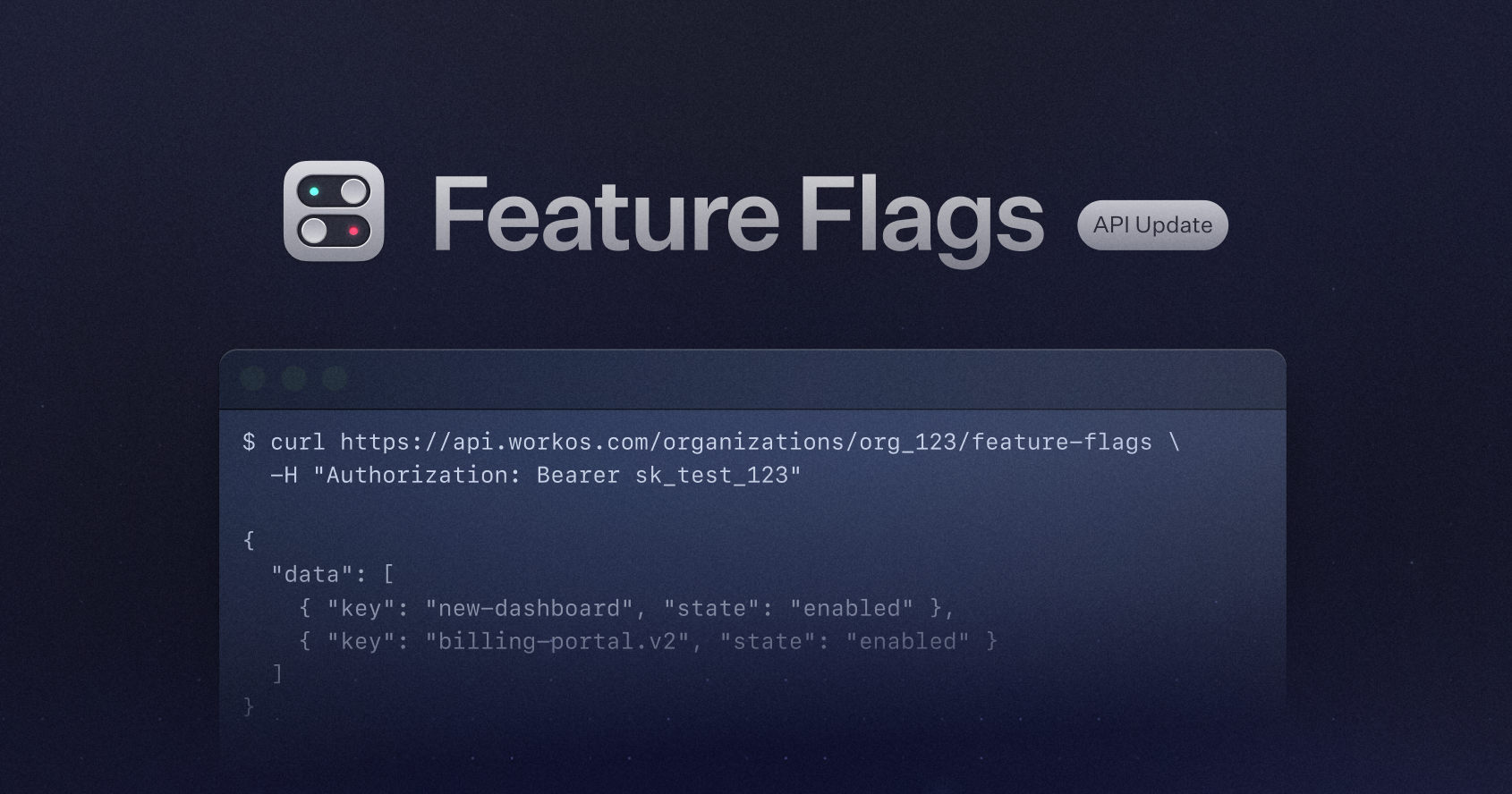
Feature flags allow teams to control the rollout of features in real time. You can now list all enabled feature flags for an organization via the API. This let’s you use feature flags where you may not have the user JWT to reference.
Learn how to fetch feature flags via API →
Enterprises can bring their own key to WorkOS Vault

WorkOS Vault now supports bring your own key (BYOK) for key encryption. Enterprises IT admins can connect their AWS Key Management Service (KMS) instance and use their own customer-managed keys (CMK) to wrap Vault data keys. This enables auditing usage of keys and disabling access via key revocation. Setup is self-serve through the Admin Portal to ensure easy onboarding.
Disposable email blocking in WorkOS Radar
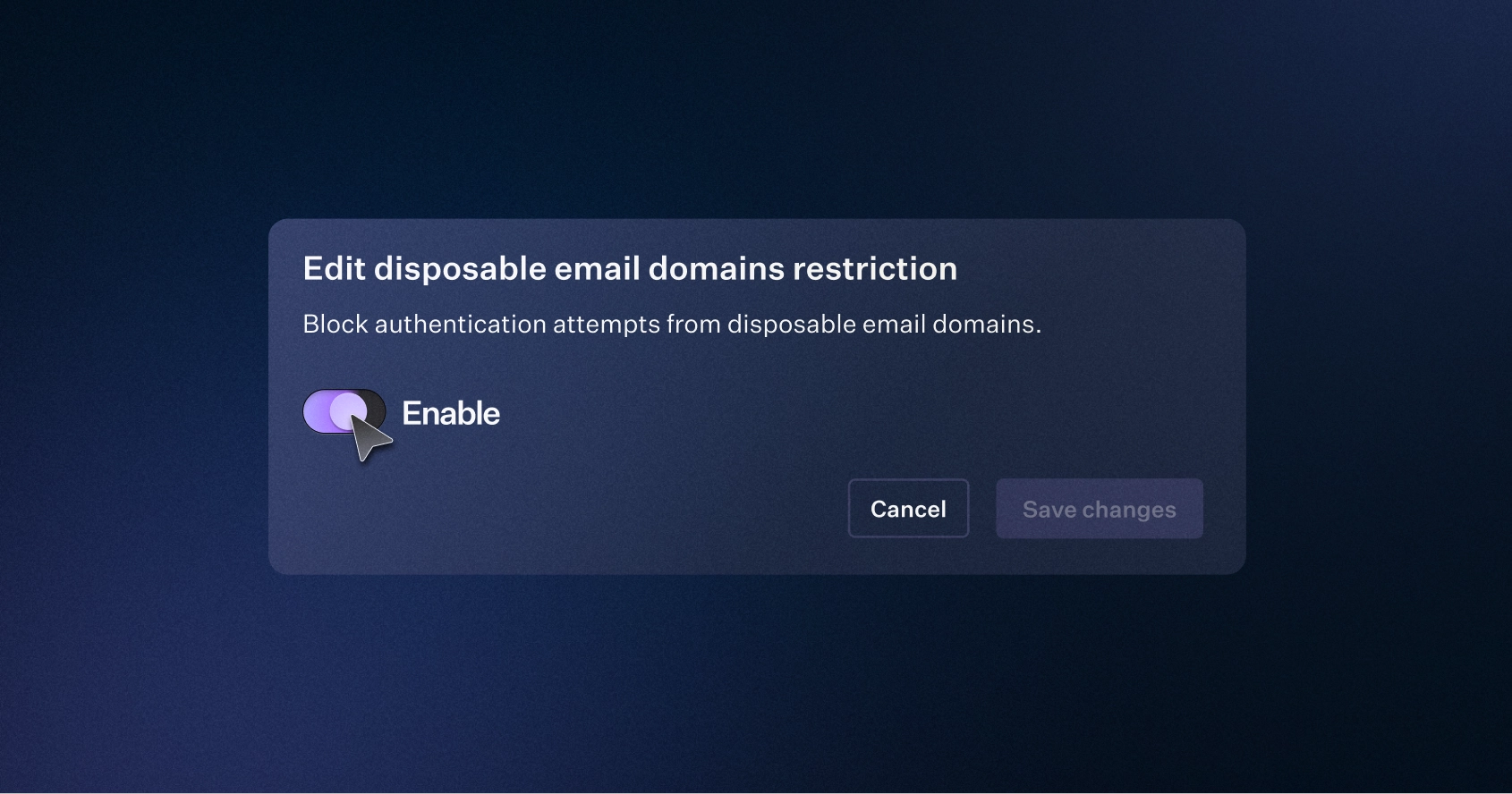
Radar can now block users from signing up with disposable email services. WorkOS Radar maintains an up to date list of disposable email domains that you can subscribe to. Any sign-ups matching those domains will be blocked preventing misuse of your product particularly for free trials and free tiers.
Learn more about disposable email blocking →
OIDC Attributes
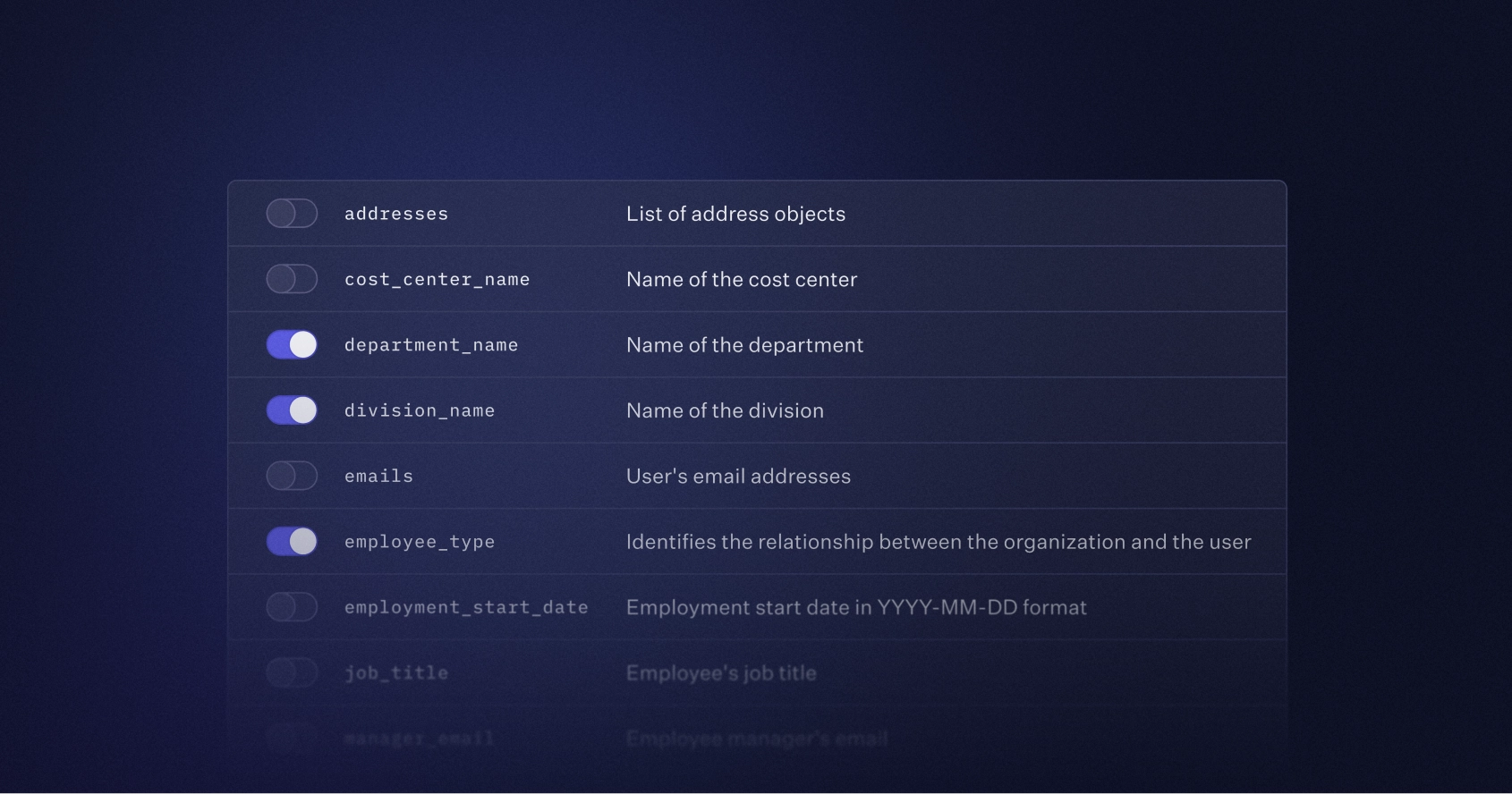
You can now customize how identity provider claims map to both standard and custom user profile attributes. Standard fields like email, idp_id, first_name, and last_name are supported out of the box, with flexibility to define additional custom attributes as needed. This makes it easier to handle non-standard OIDC responses and enrich user profiles.
See how to configure custom attributes →
More featured content
- Enterprise Ready Conf is back October 22 in San Francisco. Join product and engineering leaders shaping the future of Enterprise AI at this flagship, full-day event.
- Weren’t able to make it to MCP Night 2.0? Catch up on what happened in the blog or watch the keynote.
- Learn how Mux implemented OAuth in their MCP server with WorkOS Connect.
- New invitation events make it easier to track the invitation lifecycle.
- Learn about the impact of bad sign-ups on your app and how to stop them.
- The new session API allows for listing and revoking active user sessions.