How WorkOS solved enterprise auth for MCP servers
Learn how WorkOS acts as an OAuth bridge that removes authentication complexity so you can focus on building your MCP server's core functionality.
The Model Context Protocol (MCP) has opened up exciting possibilities for connecting AI agents with external tools and data sources. But as MCP servers increasingly handle sensitive data, how do you securely authenticate and authorize access to them?
Developers building MCP servers are caught between two difficult choices. They can either build a custom authentication system from scratch—spending weeks implementing OAuth flows, token management, and security best practices—or they can rely on basic authentication methods that aren't suitable for production use cases involving real user data.
WorkOS Connect offers a third path that eliminates this complexity entirely. Rather than forcing you to choose between building everything yourself or compromising on security, Connect acts as an OAuth bridge that handles all the authentication complexity while letting you focus on what matters most: building your MCP server's core functionality. For those looking to get started you can follow these docs. In this post, we will break down the challenges developers face with MCP auth, how WorkOS solves them, and how Mux, the video API for developers, solved their MCP auth problems with WorkOS.
The MCP authentication challenge
MCP servers often need to access your APIs and services on behalf of users. Whether you're building an MCP server that fetches basic user information or allows users to manage your entire product surface, you need a way to securely obtain and manage access tokens.
Most MCP servers, around 60%, require you to provide an API key that gets passed through on every request. This requires exposing a secret to the MCP client and underlying LLM in use. In addition, it is a bad user experience as the user needs to find where to create an API key and be responsible for managing its permissions and lifetime. This introduces potential security vulnerabilities and maintenance overhead.
OAuth has been adopted in MCP as the preferred method for securing MCP servers. The challenge comes from needing to implement OAuth into your existing app. Even if your app supports OAuth for social login with providers like Google or Github, it is a completely separate set of work to authorize your users to interact with your MCP server. Lesser-known parts of OAuth like dynamic client registration are not well covered in open source libraries and mistakes here can lead to serious security vulnerabilities.
How WorkOS Connect simplifies MCP authentication
WorkOS transforms this complex authentication landscape into a simple integration. WorkOS provides two paths for developers to solve their MCP auth issues.
For those building new apps or looking to migrate to a modern, enterprise ready authentication solution, WorkOS AuthKit provides a complete identity management solution with support for OAuth in MCP. When doing MCP Authentication with AuthKit, minimal setup is required, just point your MCP server to AuthKit and WorkOS takes care of the rest including authenticating the user, gathering consent, and securely generating tokens. You can find more details on setting up MCP auth with AuthKit in the docs.
For those with existing applications that want to quickly ship an MCP server and need OAuth support, WorkOS Connect provides an OAuth bridge that connects your MCP server to your existing authentication system while WorkOS abstracts away all the OAuth functionality. When using the OAuth bridge via Connect, WorkOS directs users to your application to log in. Once authenticated WorkOS takes care of the OAuth consent flow along with token issuance and security. Your MCP server only needs to point clients to WorkOS as the OAuth authorization server and verify tokens that WorkOS has issued. You can find the step-by-step setup in our docs.
Real-world MCP auth: Mux's MCP server
Mux, the video API for developers, just launched their own MCP server that showcases exactly why authentication complexity matters for production MCP implementations. The Mux MCP server exposes their complete video and data APIs through a self-documenting interface, allowing AI agents to upload videos, create live streams, generate thumbnails, add captions, manage playback policies, and analyze engagement data. For example, an AI agent can analyze a video asset to provide content summaries and generate descriptions to use elsewhere.
As an established platform, Mux had an existing home-grown authentication platform, but did not have the OAuth support necessary to quickly launch an MCP server. By partnering with WorkOS, they were able to focus on building their MCP server logic and offload the OAuth logic to WorkOS which was able to connect their existing authentication system with their MCP server. This meant they didn’t need to think about complicated OAuth concepts like: dynamic client registration (DCR), grant types, or consent flows. WorkOS provided this out of the box along with the customization necessary to make it work for their application’s needs.
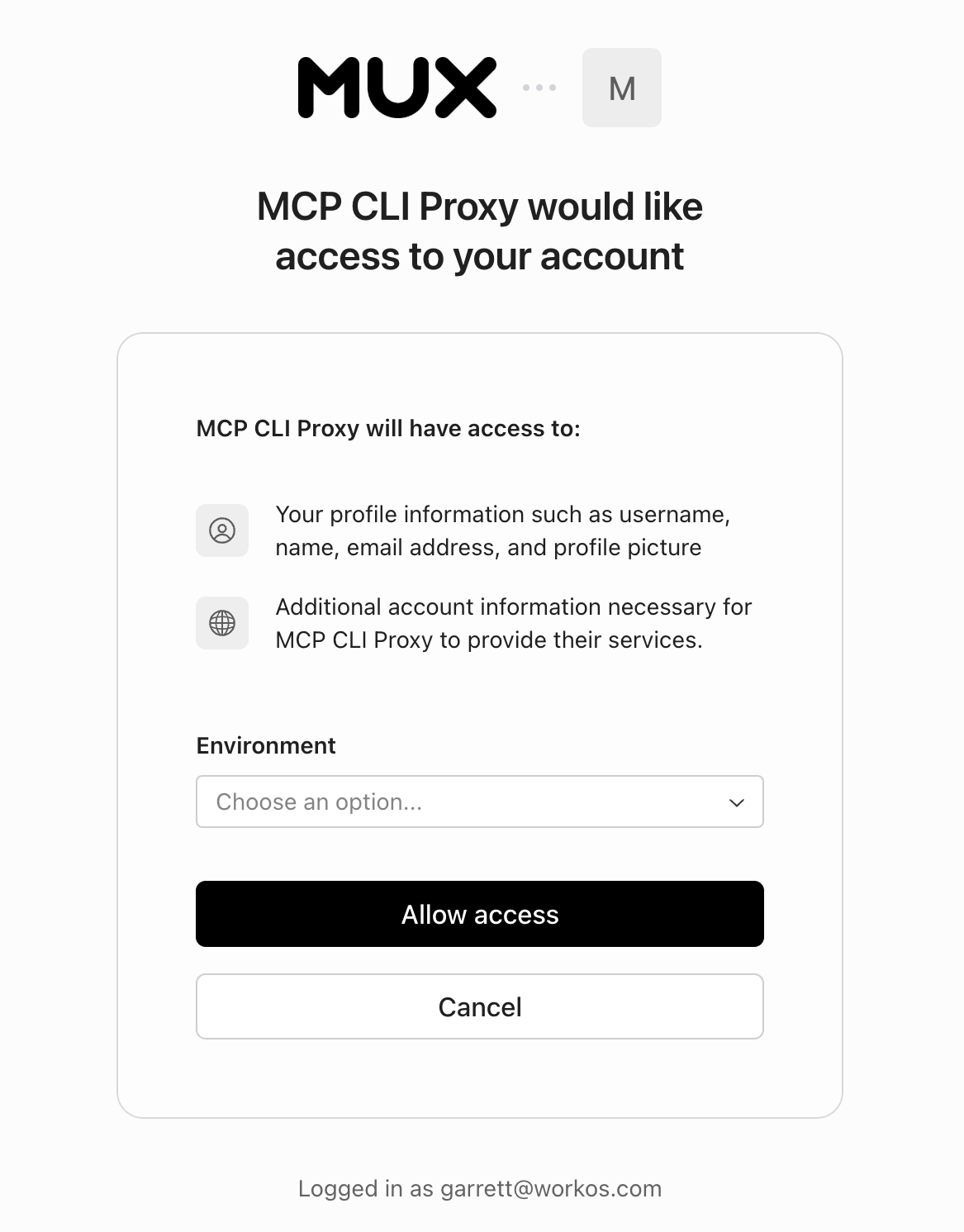
Mux’s co-founder Matt McClure had this to say about integrating with WorkOS while building their MCP server:
We wanted to ship an MCP server quickly, but we knew adding OAuth to our application was going to slow things down. With WorkOS, we were able to integrate WorkOS in a matter of days to handle everything related to OAuth. This let us focus on building the best MCP server we could for our customers.
Instead of building custom authentication systems that need to handle user permissions, token refresh, and security policies, MCP server developers can focus on what Mux focused on: creating the best possible integration for connecting AI to their product.
Get started today
WorkOS removes the authentication complexity that often becomes a bottleneck in MCP server development. By handling complex OAuth spec requirements, consent management, and token validation, WorkOS lets you focus on building the unique functionality that makes your MCP server valuable.
The integration process is straightforward, with comprehensive documentation for MCP auth with WorkOS’ AuthKit user management solution or when using WorkOS as an OAuth bridge to your existing authentication system that helps you get up and running quickly. Whether you're building your first MCP server or adding authentication to an existing one, WorkOS provides the secure, scalable foundation you need.