How to Make Your Lovable App Enterprise Ready
Transform your AI-generated prototype into a secure, scalable solution that enterprise customers will actually buy. Learn the essential steps to bridge the gap between Lovable's rapid development and true enterprise readiness.
Here's how to transform Lovable apps into secure, scalable solutions that can handle enterprise requirements like SSO, compliance, audit logging, and multi-tenant architecture.
Lovable.dev has democratized app development in ways we couldn't have imagined just a few years ago. With 500,000 users building over 25,000 applications daily, Lovable enables you to go from idea to working prototype in minutes, complete with frontend, backend, and database—all generated through natural language prompts.
But here's the challenge every successful developer eventually faces: how to secure a Lovable app and make it truly enterprise-ready.
Your app might run perfectly in demo environments and handle your initial users without issue. But when enterprise prospects start asking about SSO integration, compliance certifications, audit logs, and security frameworks, that gap becomes painfully apparent.
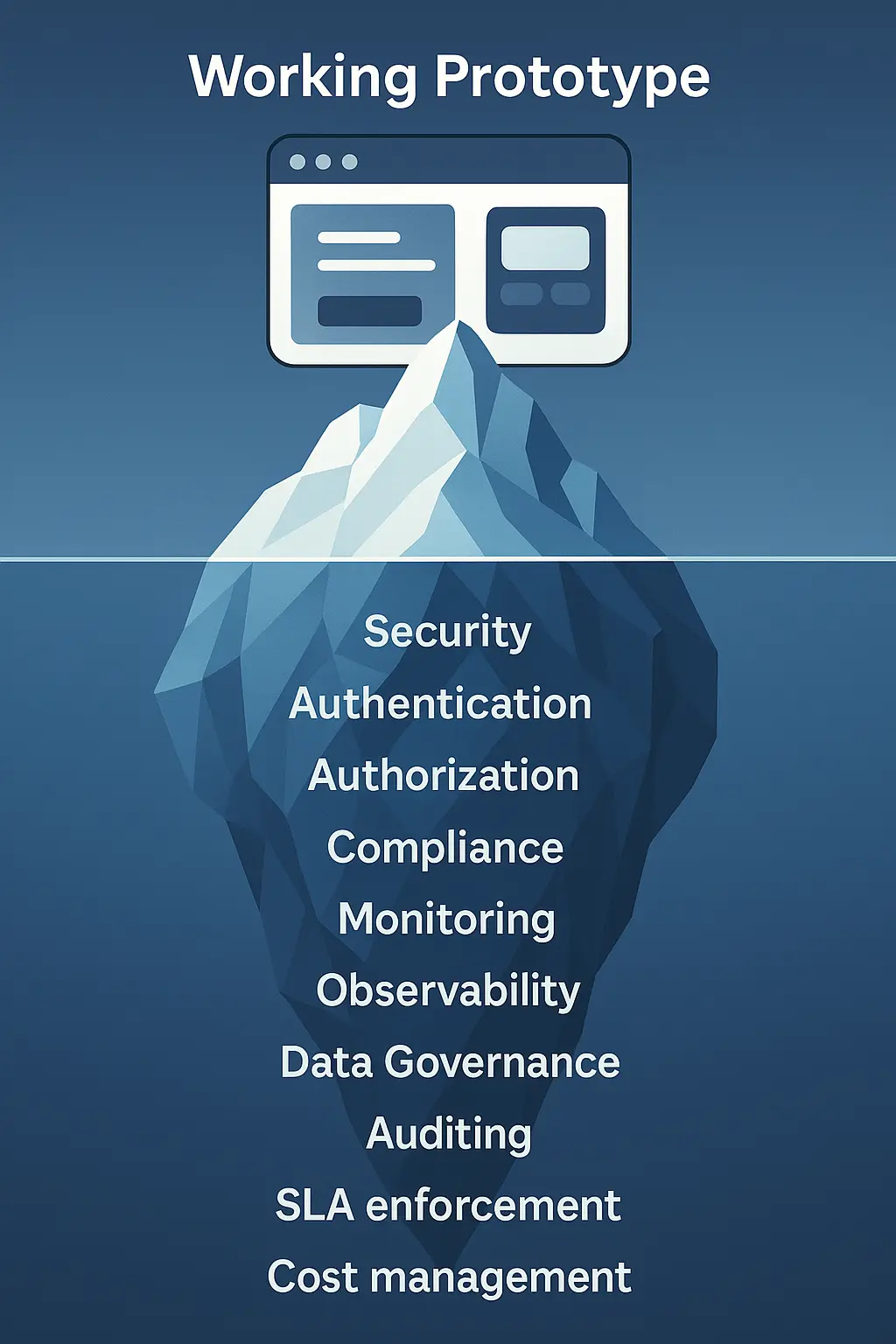
The difference between a working prototype and an enterprise-grade application isn't just technical—it's often the difference between closing deals and watching them slip away.
The Enterprise Readiness Reality Gap
When Lovable markets "production-ready" applications, they're technically correct. The code compiles, the features work, and you can deploy to users. But enterprise buyers operate with a different definition of "ready."
What Lovable Gives You
- Functional frontend and backend code
- Basic user authentication
- Working database schema
- API endpoints that respond correctly
- Deployment-ready applications
What Enterprise Customers Actually Need
- Multi-tenant architecture with proper isolation
- Enterprise identity provider integration (SAML, OIDC)
- Granular role-based access controls
- Comprehensive audit logging
- Security vulnerability assessments
- Compliance framework adherence (SOC 2, GDPR, HIPAA)
- 99.9% uptime SLAs with monitoring
- Data residency and privacy controls
- Advanced threat detection and response
AI-generated code excels at creating functional applications quickly, but enterprise readiness requires layers of security, governance, and operational excellence that extend far beyond basic functionality.
The Hidden Risks of AI-Generated Code
Recent Stanford research reveals a concerning trend: developers using AI code generation tools are more likely to introduce security vulnerabilities compared to those writing code manually. Even more troubling, they're also more likely to rate their insecure code as secure.
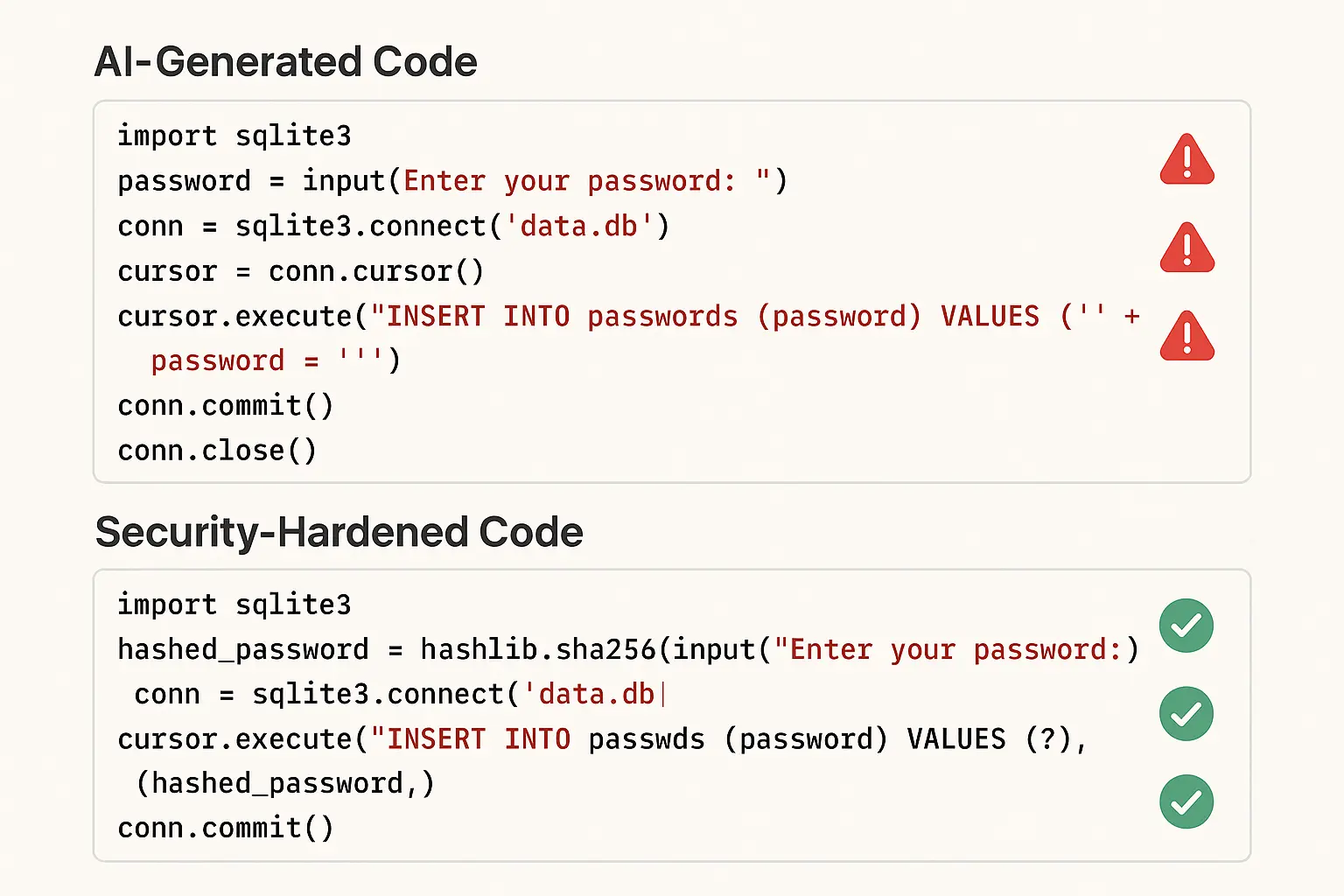
This happens because AI models are trained on massive datasets of public code, much of which was never reviewed for security best practices. When an AI suggests a database query, authentication flow, or data validation routine, it's drawing from patterns that may include insecure implementations that have persisted across countless repositories.
The most common issues include missing or incomplete input validation, outdated dependencies with known vulnerabilities, weak session management, SQL injection risks from improperly constructed queries, verbose error messages that leak system information, and overly permissive default access controls.
The challenge isn't that AI generates intentionally malicious code—it's that security often requires defensive patterns that aren't immediately obvious from functional examples.
Security Hardening: From Prototype to Production
Transforming your Lovable app into an enterprise-ready application starts with comprehensive security hardening. This process involves systematically reviewing and strengthening every component that handles sensitive data or controls access. For developers wondering how to secure Lovable apps for enterprise deployment, this security-first approach is essential.
Code Review and Vulnerability Assessment
Start by conducting a thorough security review of your AI-generated codebase. Don't assume that working code is secure code. Focus on these critical areas:
Authentication and session management deserve special attention. Review how your application handles user authentication, session creation, and token management. Look for common issues like predictable session IDs, insufficient session timeouts, and insecure token storage. Enterprise applications need robust session management that can integrate with corporate identity systems.
Input validation represents another critical vulnerability point. Examine every point where your application accepts user input, including form fields, API parameters, file uploads, and URL parameters. Implement comprehensive input validation that sanitizes data before processing and storage.
Database security requires careful auditing of all database interactions for SQL injection vulnerabilities. Ensure that all queries use parameterized statements or prepared statements rather than string concatenation. Review database permissions to ensure your application operates with minimal necessary privileges.
Error handling often reveals more than intended about system architecture. Check that your error messages don't leak sensitive information about your system architecture, database structure, or internal operations. Implement proper error logging while returning generic error messages to users.
Dependency Management and Supply Chain Security
AI-generated applications often include numerous third-party dependencies, and managing these securely is crucial for enterprise deployment.
Automated vulnerability scanning should be your first line of defense. Implement tools like Snyk or GitHub's Dependabot to continuously monitor your dependencies for known vulnerabilities. Set up automated alerts when new vulnerabilities are discovered in your dependency tree.
Regular updates and patch management require establishing a process for regularly updating dependencies while testing for compatibility issues. Enterprise customers expect rapid response to security vulnerabilities, often requiring patches within specific timeframes.
License compliance becomes critical when serving enterprise customers. Review the licenses of all dependencies to ensure compatibility with enterprise use cases. Some open-source licenses have restrictions that may conflict with commercial enterprise deployments.
Enterprise AI Agent Integration
As enterprises increasingly adopt AI agents for complex workflows, your Lovable app needs to support these integration patterns securely. The Model Context Protocol (MCP) enables agents to securely access tools and data sources, but making MCP servers enterprise-ready requires proper authentication and authorization layers.
For teams getting started with secure agent integrations, WorkOS's MCP documentation server demonstrates how to implement secure tool access patterns. Enterprise teams need robust authorization flows, and MCP authorization in 5 easy OAuth specs provides the framework for implementing enterprise-grade access control.
For teams using Cloudflare infrastructure, WorkOS Cloudflare MCP auth for agentic AI shows how to integrate MCP security with existing enterprise infrastructure. Development teams can quickly secure MCP tools using XMCP + AuthKit, which provides the fastest path to enterprise-ready MCP server security.
Enterprise Authentication and Identity Management
Perhaps no aspect of enterprise readiness is more critical than authentication and identity management. Enterprise customers expect seamless integration with their existing identity infrastructure, not another set of usernames and passwords to manage.
Since Lovable generates Next.js applications, adding enterprise authentication is straightforward with WorkOS AuthKit. Here's how to transform your AI-generated app into an enterprise-ready system:
Step 1: Install Enterprise Authentication
First, add WorkOS AuthKit to your Lovable-generated Next.js app. This replaces the basic authentication that Lovable provides with enterprise-grade identity management:
# Add WorkOS to your Lovable app
npm install @workos-inc/authkit-nextjsConfigure your environment variables to connect with WorkOS services:
# .env.local
WORKOS_API_KEY='sk_example_123456789'
WORKOS_CLIENT_ID='client_123456789'
WORKOS_COOKIE_PASSWORD="your-32-char-secure-password"
NEXT_PUBLIC_WORKOS_REDIRECT_URI="http://localhost:3000/callback"Step 2: Wrap Your Lovable App Layout
AuthKit requires wrapping your entire application to handle authentication state. This preserves all your Lovable-generated components while adding enterprise authentication:
// app/layout.tsx (modify your Lovable app's root layout)
import { AuthKitProvider } from '@workos-inc/authkit-nextjs/components';
export default function RootLayout({ children }) {
return (
<html lang="en">
<body>
<AuthKitProvider>
{children} {/* Your existing Lovable components */}
</AuthKitProvider>
</body>
</html>
);
}Step 3: Add Authentication Middleware
Middleware automatically protects your application routes, ensuring only authenticated users can access sensitive areas while keeping public pages accessible:
// middleware.ts (add to your Lovable app root)
import { authkitMiddleware } from '@workos-inc/authkit-nextjs';
export default authkitMiddleware({
middlewareAuth: {
enabled: true,
unauthenticatedPaths: ['/', '/pricing', '/about'], // public pages
},
});
export const config = {
matcher: ['/', '/dashboard/:path*', '/settings/:path*'] // protect app areas
};
Step 4: Create Authentication Routes
These routes handle the OAuth flow between your app and enterprise identity providers. The callback route processes successful authentication and redirects users to your main application:
// app/login/route.ts
import { getSignInUrl } from '@workos-inc/authkit-nextjs';
import { redirect } from 'next/navigation';
export const GET = async () => {
const signInUrl = await getSignInUrl();
return redirect(signInUrl);
};
// app/callback/route.ts
import { handleAuth } from '@workos-inc/authkit-nextjs';
// Redirect to dashboard after successful authentication
export const GET = handleAuth({ returnPathname: '/dashboard' });Step 5: Update Your Landing Page
Modify your Lovable-generated home page to handle both authenticated and unauthenticated users. This preserves your AI-generated design while adding proper authentication flows:
// app/page.tsx (modify your Lovable app's landing page)
import Link from 'next/link';
import { getSignUpUrl, withAuth } from '@workos-inc/authkit-nextjs';
export default async function HomePage() {
const { user } = await withAuth();
const signUpUrl = await getSignUpUrl();
if (!user) {
return (
<div className="min-h-screen flex items-center justify-center">
{/* Your existing Lovable design here */}
<div className="text-center">
<h1 className="text-4xl font-bold mb-8">Welcome to Your Lovable App</h1>
<div className="space-x-4">
<Link href="/login" className="btn-primary">Sign In</Link>
<Link href={signUpUrl} className="btn-secondary">Get Started</Link>
</div>
</div>
</div>
);
}
// User is authenticated - show personalized content
return (
<div className="min-h-screen p-8">
<nav className="flex justify-between items-center mb-8">
<h1 className="text-2xl font-bold">Your Lovable App</h1>
<Link href="/dashboard" className="btn-primary">Go to Dashboard</Link>
</nav>
<p>Welcome back, {user.firstName || user.email}!</p>
</div>
);
}Step 6: Protect Your Main Application
Your Lovable-generated dashboard and core functionality should require authentication. The ensureSignedIn option automatically redirects unauthenticated users to the login flow:
// app/dashboard/page.tsx (your main Lovable app interface)
import { withAuth, signOut } from '@workos-inc/authkit-nextjs';
export default async function Dashboard() {
// Automatically redirect to login if not authenticated
const { user } = await withAuth({ ensureSignedIn: true });
return (
<div className="min-h-screen p-8">
<header className="flex justify-between items-center mb-8">
<div>
<h1 className="text-3xl font-bold">Dashboard</h1>
<p className="text-gray-600">Welcome back, {user.firstName || user.email}</p>
</div>
<form action={async () => {
'use server';
await signOut();
}}>
<button type="submit" className="btn-danger">Sign Out</button>
</form>
</header>
{/* Your existing Lovable-generated interface components */}
<div className="grid grid-cols-1 md:grid-cols-3 gap-6">
{/* Lovable components go here unchanged */}
</div>
</div>
);
}Single Sign-On (SSO) Integration
With AuthKit in place, your Lovable app automatically supports enterprise SSO. SAML 2.0 remains the gold standard for enterprise SSO, but implementing it correctly requires handling XML signatures, encryption, and complex attribute mapping. WorkOS handles all of this complexity, providing battle-tested implementations that work with any enterprise identity provider.
OpenID Connect (OIDC) offers a more modern approach to SSO, built on OAuth 2.0. It's often easier to implement than SAML but requires careful attention to security considerations like token validation and secure redirect handling.
Just-in-Time (JIT) provisioning represents a critical enterprise requirement. Enterprise customers expect users to be automatically created in your application when they first sign in through SSO. WorkOS handles this automatically, mapping identity provider attributes to your application's user model.
Conclusion: From Prototype to Enterprise Success
Your Lovable app represents the future of rapid application development—the ability to turn ideas into working software faster than ever before. But to capture the full economic potential of that innovation, you need to bridge the gap between prototype and enterprise readiness.
The companies that succeed in making this transition don't just gain access to larger deal sizes—they build sustainable competitive advantages that compound over time. Enterprise customers bring not just revenue, but also product feedback, partnership opportunities, and market credibility that accelerates growth.
Ready to make your Lovable app enterprise-ready? Get started with WorkOS and implement SSO, directory sync, and audit logging in hours, not months.