XMCP + AuthKit: The Fastest Way to Secure MCP Tools and Servers
Learn how to add enterprise-grade OAuth2 authentication to XMCP servers with AuthKit in just a few lines of configuration. Perfect for securing AI tools, multi-tenant platforms, and internal applications.
The Model Context Protocol has fundamentally changed how we think about AI tool integration. APIs are no longer just for humans—tools need to be self-describing, callable by LLMs, and discoverable via protocol, not hardcoded SDKs.
That's the premise behind MCP: a standard for exposing tools that LLMs can find, reason about, and invoke. And XMCP is the quickest way to ship tools that speak MCP.
In this post, we'll show you how to use XMCP and AuthKit to build a secure MCP server that can be deployed globally in minutes. The companion repository for this post is here.
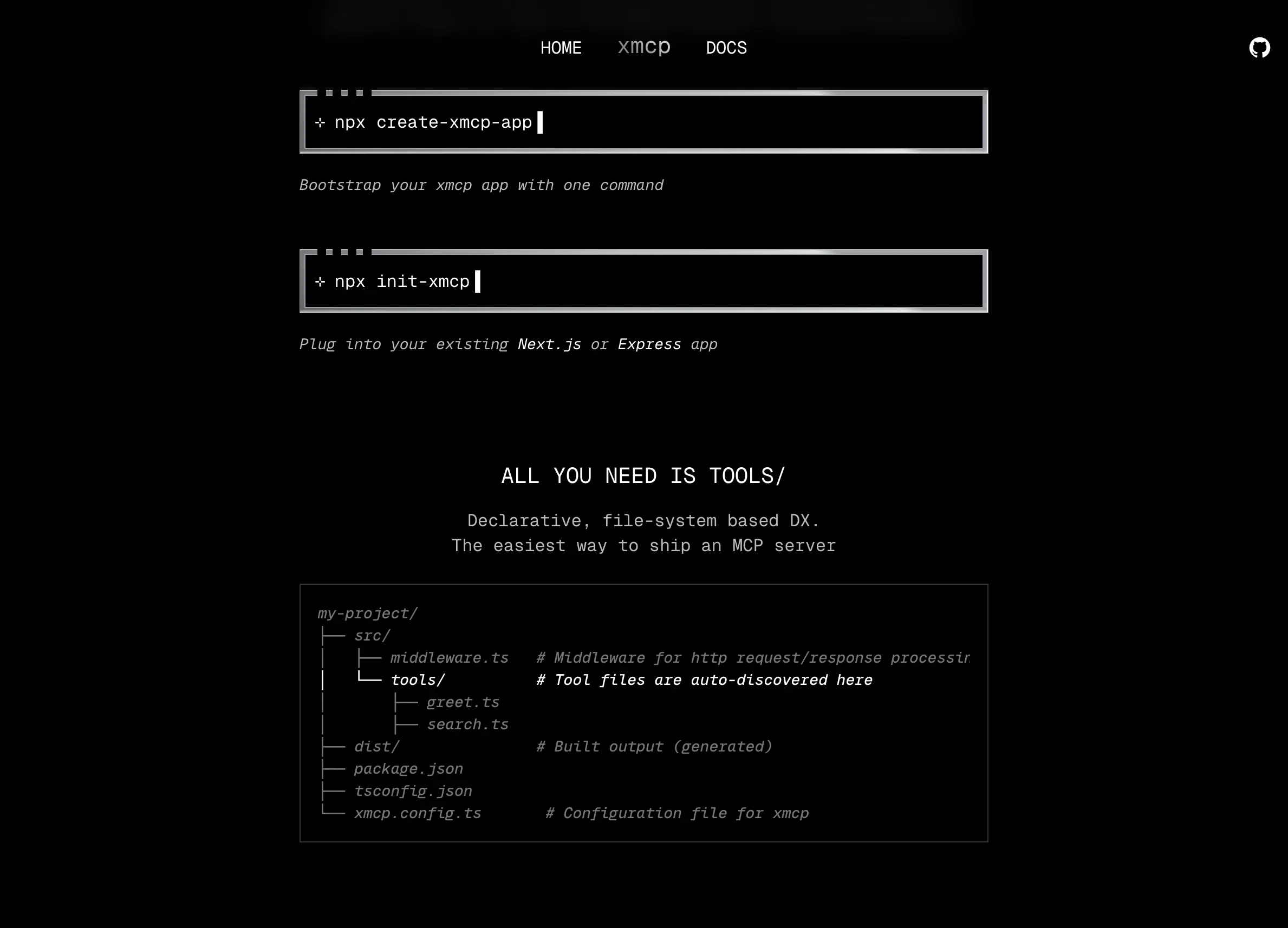
What is the XMCP project for MCP servers?
XMCP gives you a declarative, file-based developer experience that feels more like working with Remix or Next.js than building traditional REST APIs.
You write a tool like src/tools/search.ts, export a function, and XMCP turns it into an MCP-ready resource server—complete with metadata, type signatures, and routing.
Run the following npx command to get started:
npx create-xmcp-app@latestThat's all it takes to spin up a new MCP server. It's fast, minimal, and fun.
But here's what's been missing from most MCP frameworks: secure authentication.
The Authentication Gap
If you're building AI tools for internal users, multi-tenant platforms, or anything that touches sensitive data, you need a way to restrict access and tie requests to identity.
With the June 2025 MCP specification updates specifying that MCP servers are OAuth Resource Servers and NOT Authorization Servers, authentication is no longer optional—it's essential.
Today we're sharing a minimal demo that shows how to bridge this gap by adding AuthKit to your XMCP server in just a few lines of config.
Getting Started with Secure XMCP
Grab the WorkOS demo repository here.
1. Bootstrap Your Project
Start by creating a new XMCP project.
npx create-mcp-app@latestThis sets up the full project structure and gives you a starter tool at src/tools/greet.ts.
import { type XmcpConfig } from "xmcp";
const config: XmcpConfig = {
experimental: {
oauth: {
baseUrl: "http://localhost:3002", // Or your deployed server URL
endpoints: {
authorizationUrl: `${process.env.AUTHKIT_DOMAIN}/oauth2/authorize`,
tokenUrl: `${process.env.AUTHKIT_DOMAIN}/oauth2/token`,
registerUrl: `${process.env.AUTHKIT_DOMAIN}/oauth2/register`,
userInfoUrl: `${process.env.AUTHKIT_DOMAIN}/oauth2/userinfo`,
},
issuerUrl: process.env.AUTHKIT_DOMAIN as string,
defaultScopes: ["openid", "profile", "email"],
},
},
http: {
port: 3002,
},
};
export default config;2. Configure OAuth with AuthKit
Next, wire up authentication by modifying your xmcp.config.ts:
You can either set AUTHKIT_DOMAIN as an environment variable (e.g., in .env.local) or hardcode your domain directly in the config.
3. Configure Your AuthKit Environment
You'll find your AuthKit domain in the WorkOS Dashboard under Applications. Make sure to:
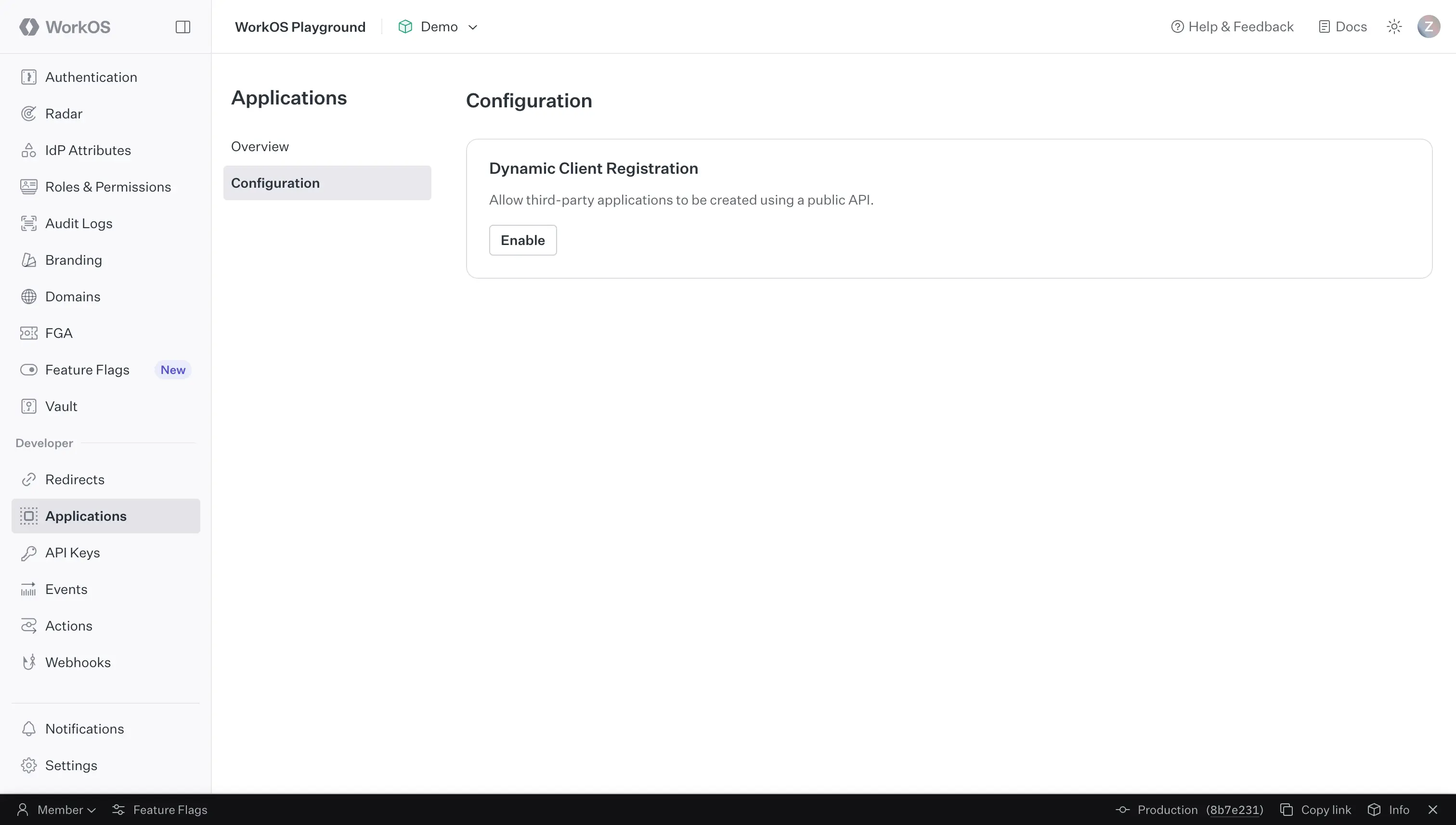
- Enable Dynamic Client Registration under Applications → Configuration (this is the magic spec that powers MCP auto-discovery)
- Add your callback URL (e.g.,
http://localhost:3002/callback) in the Redirects tab
4. Start Your Protected Server
Now run the dev server:
npm run devYour XMCP tools are now protected with OAuth2—powered by AuthKit under the hood.
Accessing User Context in Your Tools
Once a request hits your tool, XMCP passes the Authorization header through to your tool logic. You can extract and verify the JWT from inside any tool file using XMCP's headers utility:
import { headers } from "xmcp/headers";
import { jwtVerify, createRemoteJWKSet } from 'jose';
// Define the schema for tool parameters
export const schema = {};
// Define tool metadata
export const metadata = {
name: "userInfo",
description: "Get the user info",
annotations: {
title: "Get the user info",
}
};
// Tool implementation
export default async function userInfo() {
const header = headers();
const JWKS = createRemoteJWKSet(new URL(process.env.AUTHKIT_DOMAIN + '/oauth2/jwks'));
const token = header.authorization?.split(' ')[1];
if (!token) {
return {
content: [{ type: "text", text: "No bearer token found in the Authorization header." }],
};
}
try {
const { payload } = await jwtVerify(token, JWKS, {
issuer: process.env.AUTHKIT_DOMAIN as string,
});
// Payload now contains user info and claims
console.log(payload);
return {
content: [
{ type: "text", text: "User info: " + JSON.stringify(payload.sub, null, 2) },
],
};
} catch (err) {
return {
content: [{ type: "text", text: `Token verification failed: ${err}` }],
};
}
}This is the full example pattern from the demo repo's src/tools/userInfo.ts.
First we verify the JWT using JSON web keys. If we have a valid token, we can extract the user's information from it, providing critical context directly to the tool, without boilerplate.
For even richer user context—like organization membership, directory information, or MFA status—you can drop in the WorkOS SDK and fetch that data using the user's token.
Why This Combination Works
XMCP provides a lightweight, modern way to build resource servers for AI agents. With AuthKit, you get a clean path to production with enterprise-grade features:
- Scoped identity — Users only access what they're authorized for
- Team-aware permissions — Organization context flows through to your tools
- SSO support — Works with Google, Microsoft, Okta, and hundreds of other providers
- Zero OAuth complexity — AuthKit handles the specification details so you can focus on building
Whether you're building internal tools, securing developer APIs, or creating workflows that connect to private infrastructure, this combination gives you a secure foundation without complexity.
What's Next
The Model Context Protocol ecosystem is evolving rapidly, with security becoming a first-class concern. As AI agents become more capable and integrated into sensitive workflows, frameworks like XMCP paired with robust authentication solutions like AuthKit provide the foundation for production-ready AI tool infrastructure.
Ready to get started? Check out xmcp.dev for more on the framework, and try our demo repository if you want to see AuthKit and XMCP working together today.