Why building SCIM is hard
Why SCIM looks easy on paper but is one of the hardest integrations to build and scale in practice.
Every SaaS vendor eventually reaches the same milestone. A large customer requests SCIM-based automated user provisioning. Engineering teams look at the RFC, see a few endpoints, and assume they can build it in a sprint. Weeks later, reality sets in: while SCIM looks simple on paper (a standardized REST API to create, update, and delete users, how hard is that?), in practice, implementing it is one of the most deceptively difficult challenges in enterprise SaaS.
This article explains why building SCIM is hard, how provider idiosyncrasies multiply complexity, and why many teams choose to adopt a managed solution like WorkOS Directory Sync instead.
Let’s dive right in.
Understanding SCIM’s appeal
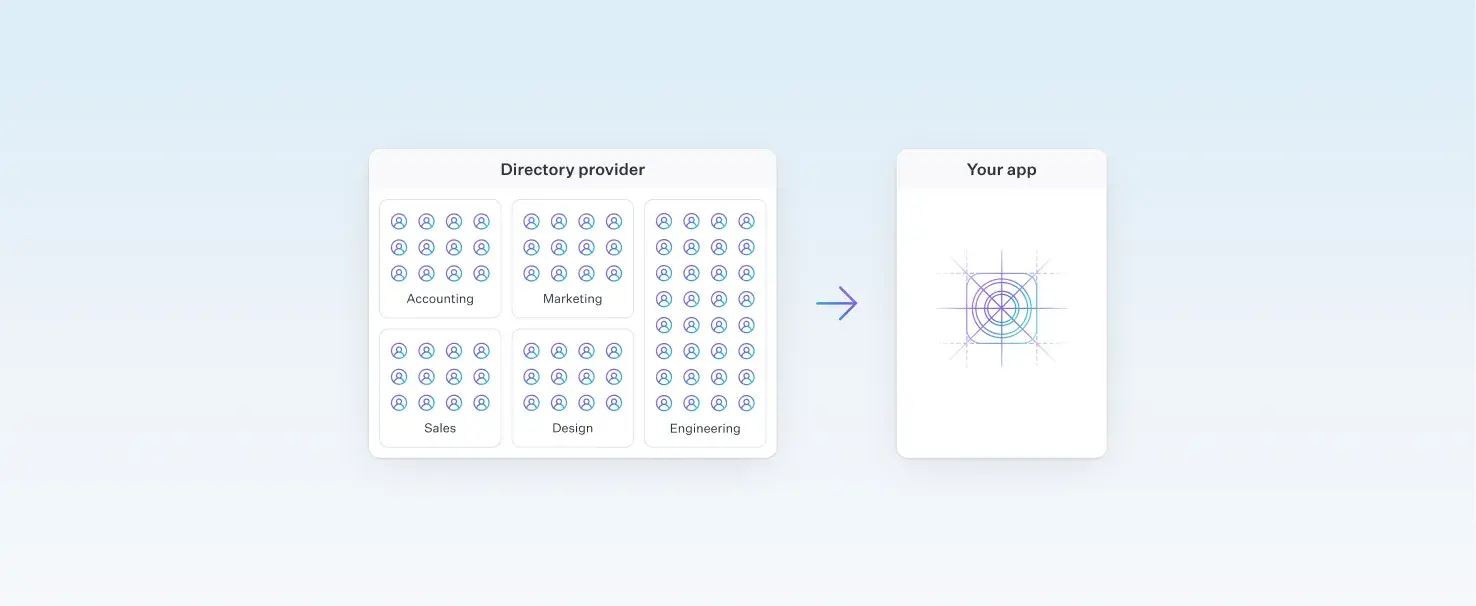
SCIM (System for Cross-domain Identity Management) defines a REST and JSON-based protocol that automates user provisioning and deprovisioning between identity providers (IdPs) and applications.
In simpler words, it eliminates manual user management by syncing accounts automatically from providers like Okta, Entra ID, and Google Workspace. That’s how, when you join a new company, you get access to 100 different systems immediately (and when you leave, you likewise lose access to everything all at once). The admin adds you as an employee to the company’s identity provider (for example, Okta), and then you are automatically created as a user with access to all the apps you need to do your job. This is all SCIM.
For more details on how SCIM works, see:
- SCIM: what it is and how it works: The article discusses the SCIM standard in-depth, how it works, and how you can add SCIM support to your app.
- Unlocking the power of SCIM: Learn what SCIM stands for, how it simplifies provisioning and access control, and why you should support it.
- How SCIM provisioning works: A guide on how SCIM provisioning works, using real-world examples and API calls and responses.
- How SCIM deprovisioning works: Learn what is user deprovisioning and how it works with SCIM.
- The developer’s guide to SCIM: Learn what SCIM is, why you should care, and how to build it into your app using WorkOS Directory Sync.
At this stage, the concept seems straightforward. But complexity arises quickly once you try to implement it across multiple identity systems.
SCIM’s hidden complexity and the realities of working with different providers
Most developers start by reading the SCIM 2.0 RFC. It looks like a simple CRUD interface for Users and Groups. At this stage, the concept seems straightforward. The SCIM protocol looks clean, with just a handful of endpoints and predictable JSON payloads. You create users, update them, delete them, and sync groups, which looks like any standard REST integration. But the simplicity of the spec hides an important reality: no two identity providers behave exactly the same way.
The SCIM RFC is deliberately abstract. Each identity provider interprets and extends it differently. This abstraction is what makes SCIM powerful and widely adoptable, but it’s also what introduces complexity when you try to support multiple providers. You’ll quickly encounter differences in how APIs behave, how attributes are named and validated, and how filtering, pagination, or patching work. The result is that what looked like one integration becomes several overlapping implementations, each with its own quirks.
In other words, the problem is not implementing SCIM once; it’s making it work reliably with every provider your customers use.
Some of the areas where challenges emerge include:
- PATCH semantics: Some providers deviate from the standard, requiring workarounds for multi-valued attributes.
- Filtering and pagination: Implementations of filter parameters and startIndex handling vary widely.
- Bulk operations: Many IdPs claim to support them, but their behavior under load can differ.
- Groups and roles: Membership synchronization is often inconsistent between providers.
Okta, Google, Entra ID, and others all claim to “support SCIM,” but they implement it with unique schemas, filters, and authentication requirements.
For instance:
- Okta enforces strict attribute mappings and often sends unexpected PATCH payloads.
- Entra ID supports only a subset of the SCIM filter syntax.
- Google Workspace may delay deprovisioning calls or throttle large requests.
Even subtle inconsistencies require extensive QA and test infrastructure to handle.
Understanding provider idiosyncrasies is key to reliable provisioning at scale.
For more on this, see SCIM challenges: navigating the idiosyncrasies of different providers.
The build vs. buy decision
Once you’ve seen how unpredictable SCIM implementations can be across identity providers, the next question becomes inevitable: should you build and maintain all of this yourself, or should you use a managed solution?
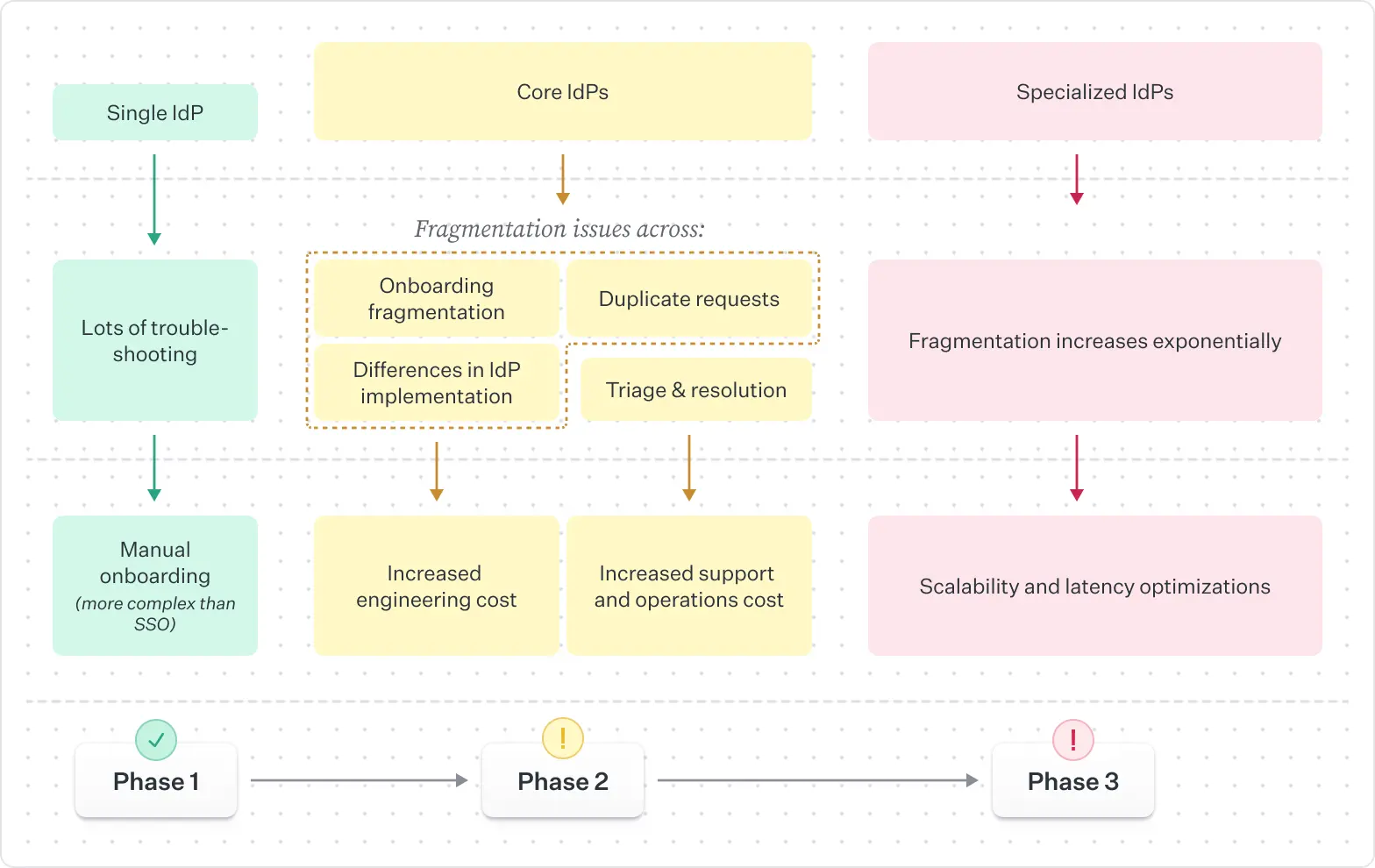
At first, building in-house feels appealing. You already have the RFC open, your API framework in place, and a small test environment ready to go. For one identity provider (maybe two), you can often get something working. The trouble starts when your second or third enterprise customer arrives, using a different IdP with slightly different expectations.
Every new integration adds another layer of conditionals, schema handling, and test coverage. Before long, you’re not maintaining a SCIM API, you’re maintaining a matrix of IdP-specific implementations. Each one requires updates whenever a provider changes behavior, fixes a bug, or introduces a new SCIM extension.
That’s why most teams eventually face a tradeoff:
- Building internally gives you control, but it means carrying the cost of debugging every provider’s quirks, maintaining custom mapping logic, and staying up to date with each IdP’s evolving behavior.
- Buying or adopting a managed solution accelerates time-to-market by abstracting those differences away behind a single, normalized API.
The Implementation challenges of a homegrown SCIM solution article outlines what teams typically run into when they choose to build from scratch:
- Constant debugging of provider differences
- Unclear or shifting IdP documentation
- Support overhead when customers encounter mismatched expectations
- Specialized expertise required to maintain identity and access logic
WorkOS’s Directory Sync exists precisely because of these pain points. It provides a fully hosted SCIM integration that works across Okta, Entra ID, Google Workspace, and more, through one consistent API.
- To understand the broader engineering tradeoffs, Build vs. Buy Part I: Complexities of building SSO and SCIM in-house takes a closer look at the hidden engineering effort of supporting multiple IdPs, custom attribute mappings, and constant maintenance.
- Build vs. Buy Part II: ROI Comparison between homegrown and pre-built solutions quantifies those costs, comparing the long-term ROI of homegrown versus pre-built integrations—both in terms of developer hours and the impact on enterprise deal velocity.
.webp)
- For an overview of how different IdPs compare and where their implementations diverge, see SCIM Providers Comparison and Top SCIM Providers 2025.
Developer experience: Why it’s never “just an API”
Building a compliant SCIM API requires far more than writing endpoints. It demands:
- A robust data model for users, groups, and attributes
- Idempotent handling of repeated calls from IdPs
- Partial updates, PATCH logic, and schema validation
- Secure token-based authentication
- Monitoring and logging for every provisioning event
Developers often underestimate the operational burden. See SCIM Best Practices for some of the things that you will have to implement.
The admin experience: configuration and onboarding challenges
Even after you’ve implemented your SCIM API, there’s another layer of complexity: how your customers’ IT administrators will actually configure it.
When an enterprise wants to enable SCIM, their admin has to connect their identity provider (like Okta, Entra ID, or Google Workspace) to your application. That means entering your SCIM endpoint URL, generating and sharing credentials, mapping attributes, and testing the connection.
If you don’t provide a dedicated interface for this, the process becomes a manual, error-prone exchange between your support team and the customer’s IT staff. You’ll end up sending documentation, debugging screenshots, and rotating tokens by email or ticket, repeatedly, for every customer. It’s not scalable, and it adds friction right where you want simplicity.
WorkOS solves this with the Admin Portal, a hosted setup interface that lets your customers’ administrators self-serve their SCIM and SSO configuration. Through the Admin Portal, admins can securely connect their identity provider, authorize provisioning, and verify the integration, without your team needing to intervene.

This means your engineering team doesn’t need to build or maintain an admin-facing setup UI, and your customer success team no longer has to manually coordinate identity configuration. The Admin Portal eliminates that entire setup workflow, letting enterprises connect their directory to your app in minutes.
In short: while Directory Sync solves the technical complexity of implementing SCIM, the Admin Portal solves the operational complexity of onboarding and configuration.
SCIM in the AI era
As organizations adopt AI-driven tools and autonomous agents, SCIM flows will expand to cover a new class of identities. These agents, whether large language model instances, workflow bots, or specialized assistants, will act on behalf of users and interact with enterprise data. That means they must be provisioned, updated, and deprovisioned just like human accounts.
SCIM flows will need to handle:
- Short-lived lifecycles. Agents may exist only for a session or project, requiring automated provisioning and teardown.
- Delegated ownership. Each agent must be associated with a responsible human or team.
- Dynamic attribute updates. Agents can evolve or gain new capabilities, demanding frequent schema updates and re-syncing.
- Cross-tenant scoping. AI tools embedded in multiple customer tenants will need clear isolation and tenancy-aware provisioning.
These new conditions stretch SCIM’s existing semantics. Systems that once assumed stable, long-lived users now need to manage thousands of ephemeral identities that still require secure onboarding and deactivation.
Furthermore, SCIM implementations will need to integrate with policy engines to automatically enforce context (who owns the agent, what it can access, and when it should expire). Automated deprovisioning becomes even more critical, since agents that persist beyond their intended scope represent potential security risks.
There is already a new SCIM draft out, addressing the changes required for AI agents. For more on this, see SCIM for AI: Inside the new IETF draft for agent and agentic application provisioning.
Simplifying SCIM with WorkOS Directory Sync
WorkOS built Directory Sync so developers never have to reimplement SCIM logic for every customer or provider.
Directory Sync handles:
- SCIM protocol translation for all major IdPs
- User and group lifecycle synchronization
- Real-time webhooks for changes
- Automatic normalization of attributes and payloads
Developers integrate once with the WorkOS API and immediately gain full enterprise provisioning coverage. This abstraction turns a multi-month engineering project into a two-day implementation.
Here are some practical tutorials on how to integrate WorkOS Directory Sync in your app:
- Implementing a Generic SCIM Client: A Practical Guide
- Okta SAML SSO and SCIM Provisioning in Node.js
- How to Sync Users from Okta to Your Python App
- Sync Users from Google Workspace Using Ruby and WorkOS
- Sync Users from Entra ID Using Node and WorkOS
- Directory Sync Quickstart
Conclusion
SCIM is not hard because of the protocol. It is hard because of the fragmented implementations, provider quirks, and real-time reliability expectations enterprises demand.
Every SaaS company eventually faces the same question: do we keep patching a fragile homegrown SCIM service, or do we offload it to a system designed for interoperability?
For enterprise-grade provisioning without the pain of maintaining it, get started with WorkOS Directory Sync.