July Updates
New this month: Convex Integration, Country Blocks, SMS Challenges, Custom Fonts, & More
New this month: Convex Integration, Country Blocks, SMS Challenges, Custom Fonts, & More
Convex now supports WorkOS AuthKit

Convex now has first-class support for WorkOS AuthKit as an authentication provider. Easily authenticate users in your frontend with AuthKit and validate access in your Convex backend using the same session token. No extra wiring or token exchange required.
See the full integration guide in the Convex docs →
Country Blocks with Radar
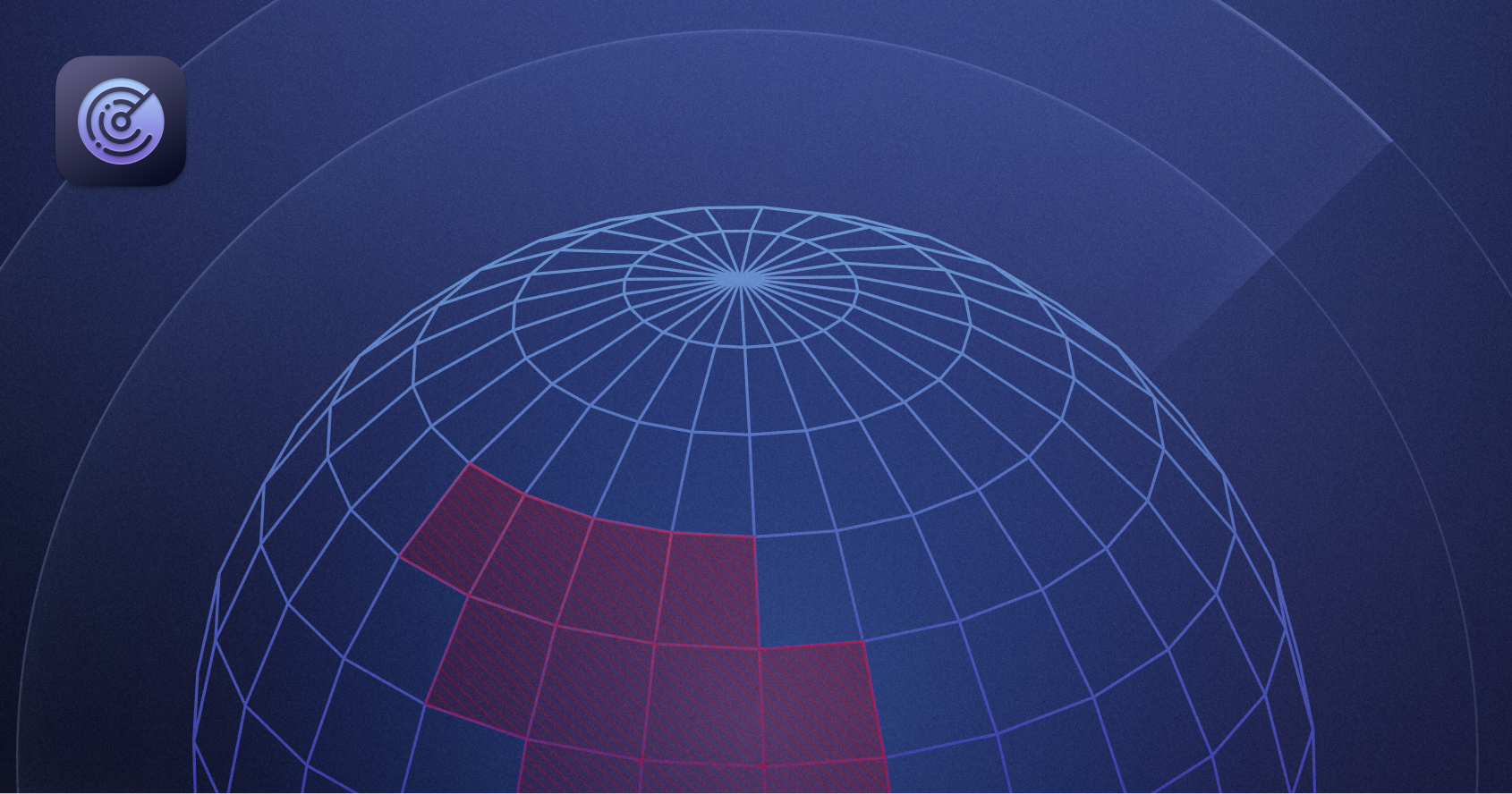
WorkOS Radar now supports blocking traffic based on specific countries and geographic regions. This allows you to block sanctioned countries in your jurisdiction or countries where you don’t do business.Reach out to support via email or Slack to configure a country or region block.
Explore country blocks in Radar →
SMS Challenges with Radar
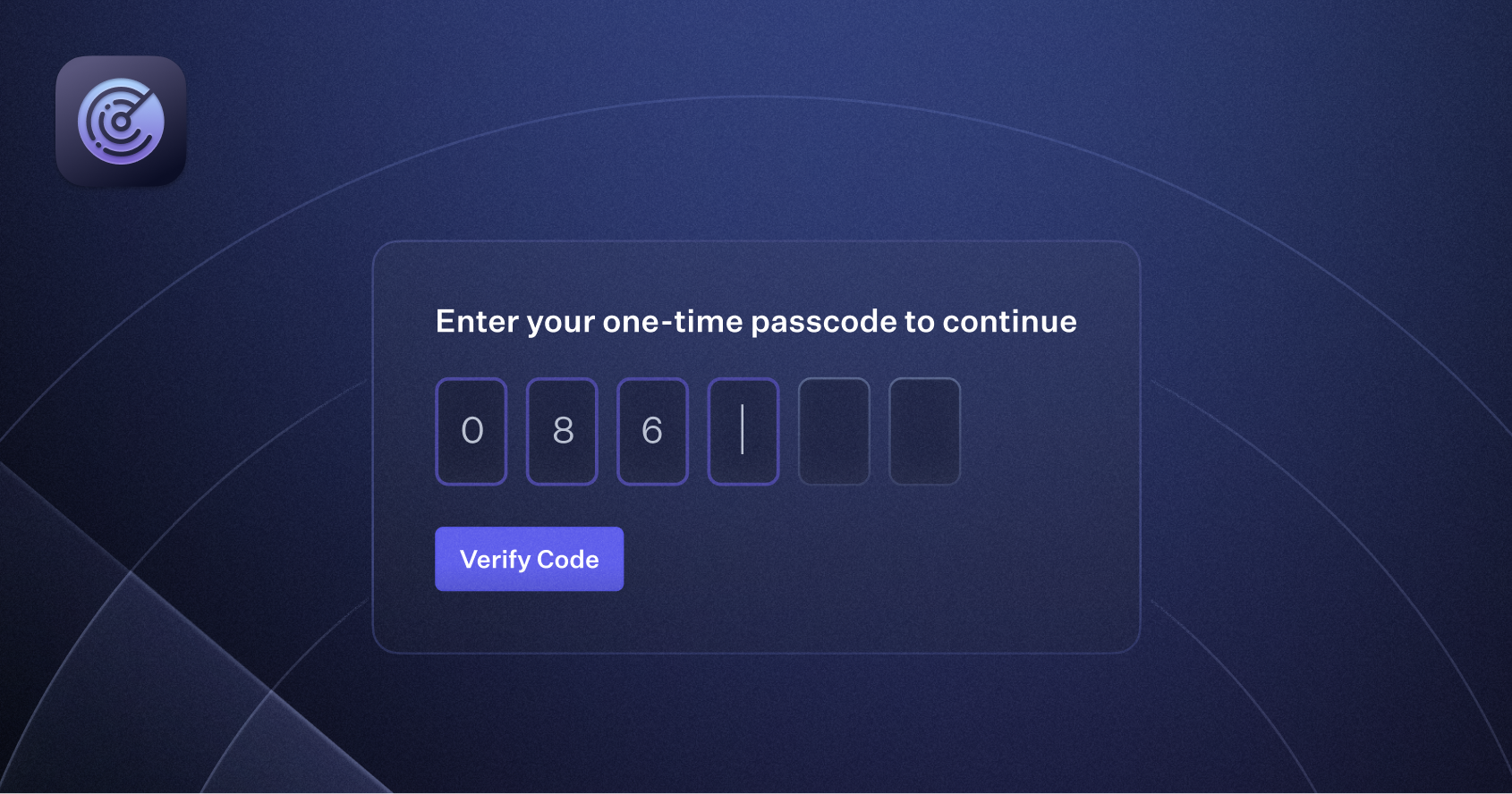
WorkOS Radar can now challenge suspicious sign-ups with an SMS challenge verification step to better combat fraud and abuse. Challenged sign-ups will must provide a valid phone number and enter the code sent to their device. Get in touch via Slack or email support if interested. Additional charges may apply.
Custom Fonts for AuthKit
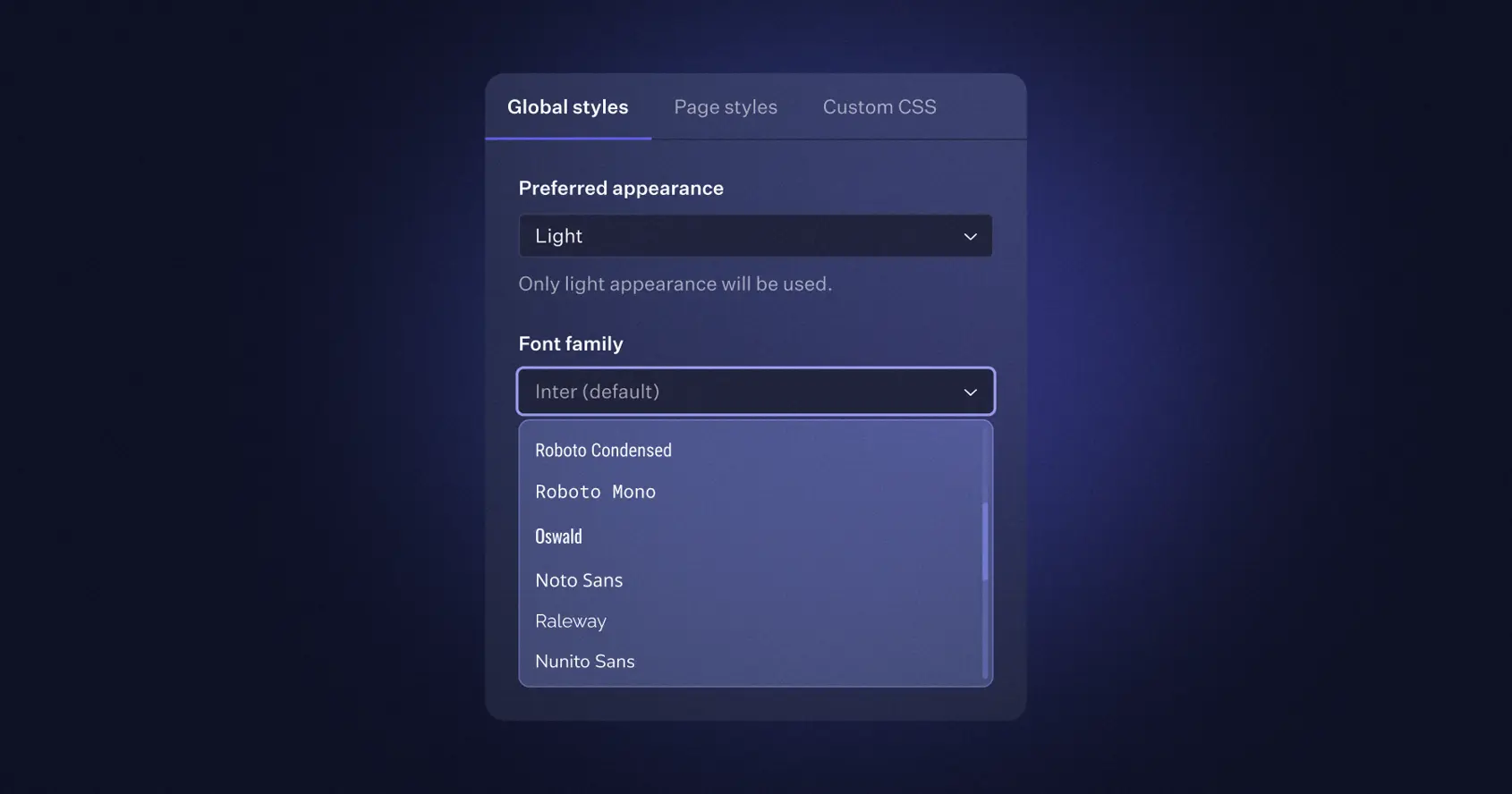
You can now customize the font used by AuthKit in the Branding section of the WorkOS Dashboard. Choose from a selection of Google font families to match your brand.
Learn how to brand AuthKit →
Custom OAuth scopes in the Dashboard
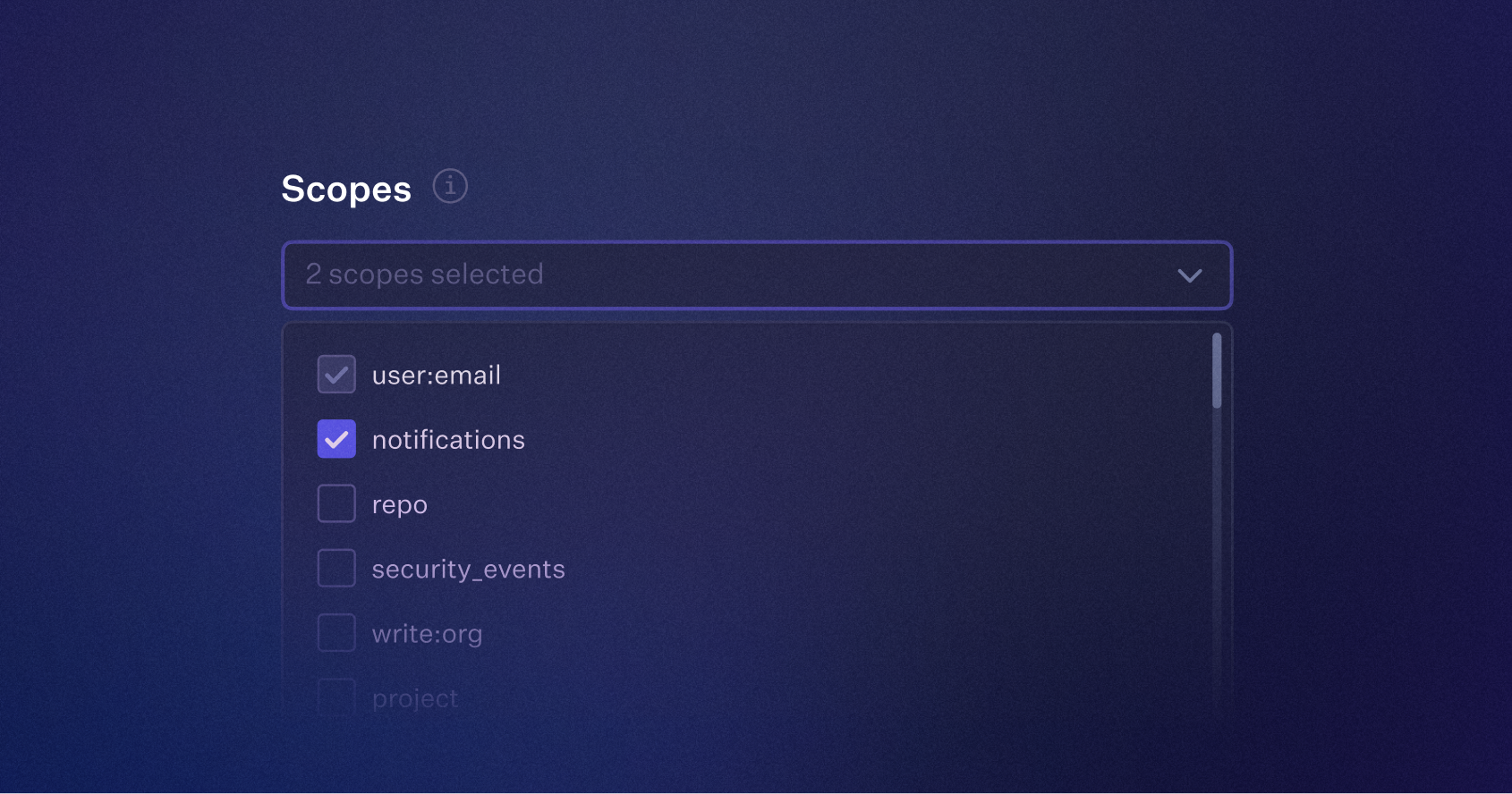
Developers can now configure custom OAuth scopes in the WorkOS Dashboard. When configured, the access token and refresh token from the OAuth provider will be passed through to your application, allowing access to user accounts with the granted permissions. Developers can also specify additional scopes dynamically using the new provider_scopes query parameter.
Check out the OAuth scopes docs →
Token refresh remembers most recent organization
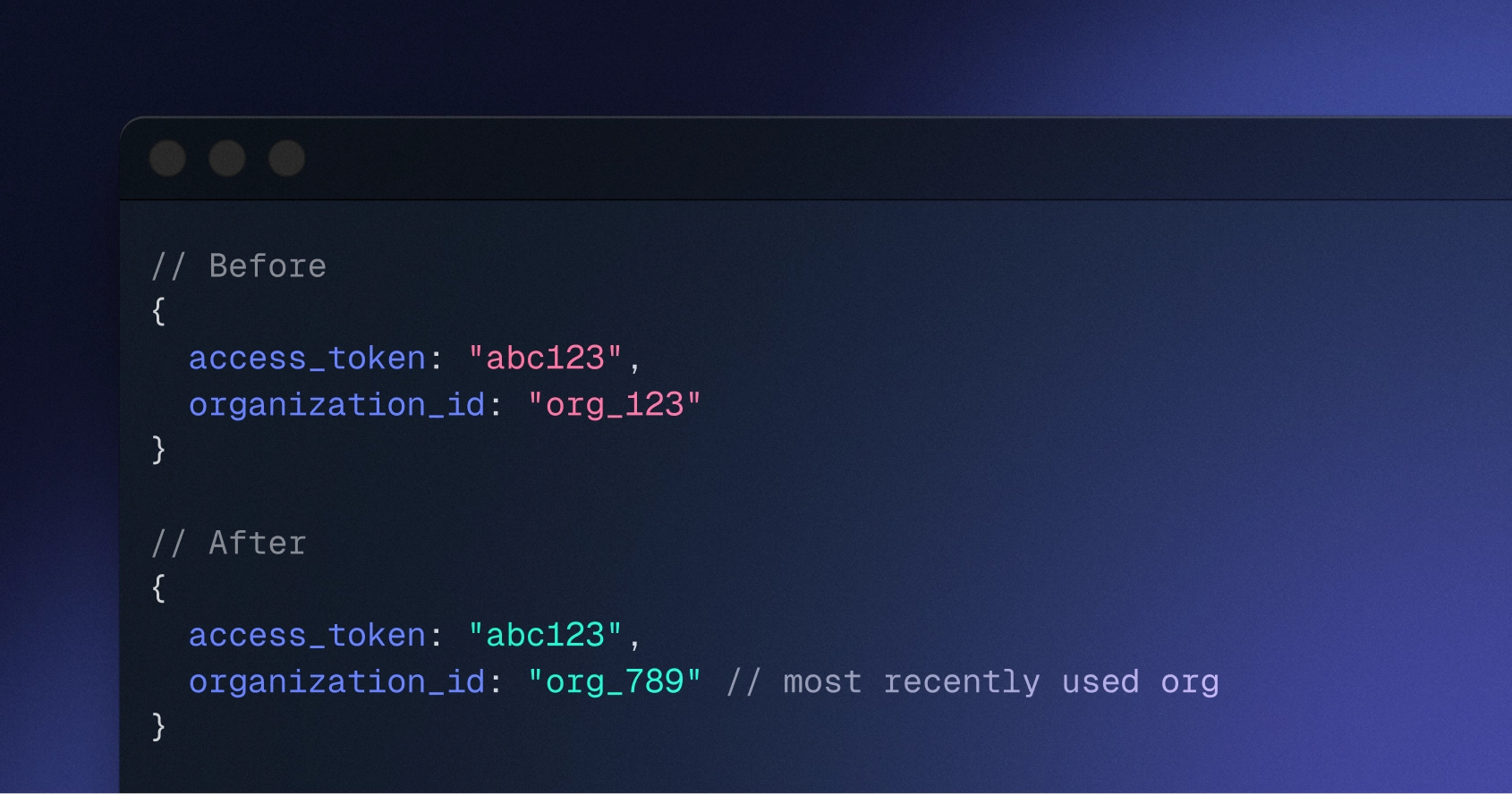
When developers’ applications authenticate with refresh tokens and do not specify an organization_id, the response now includes the most recently used organization for that session. Previously, the response only included the organization if it was part of the session’s initiation.This change is especially helpful for onboarding flows that create new organizations. Now, token refreshes will include the new organization membership even if the organization was created after the session was initiated.
Learn more about token refresh behavior →
Expanded Support for OIDC SSO Providers
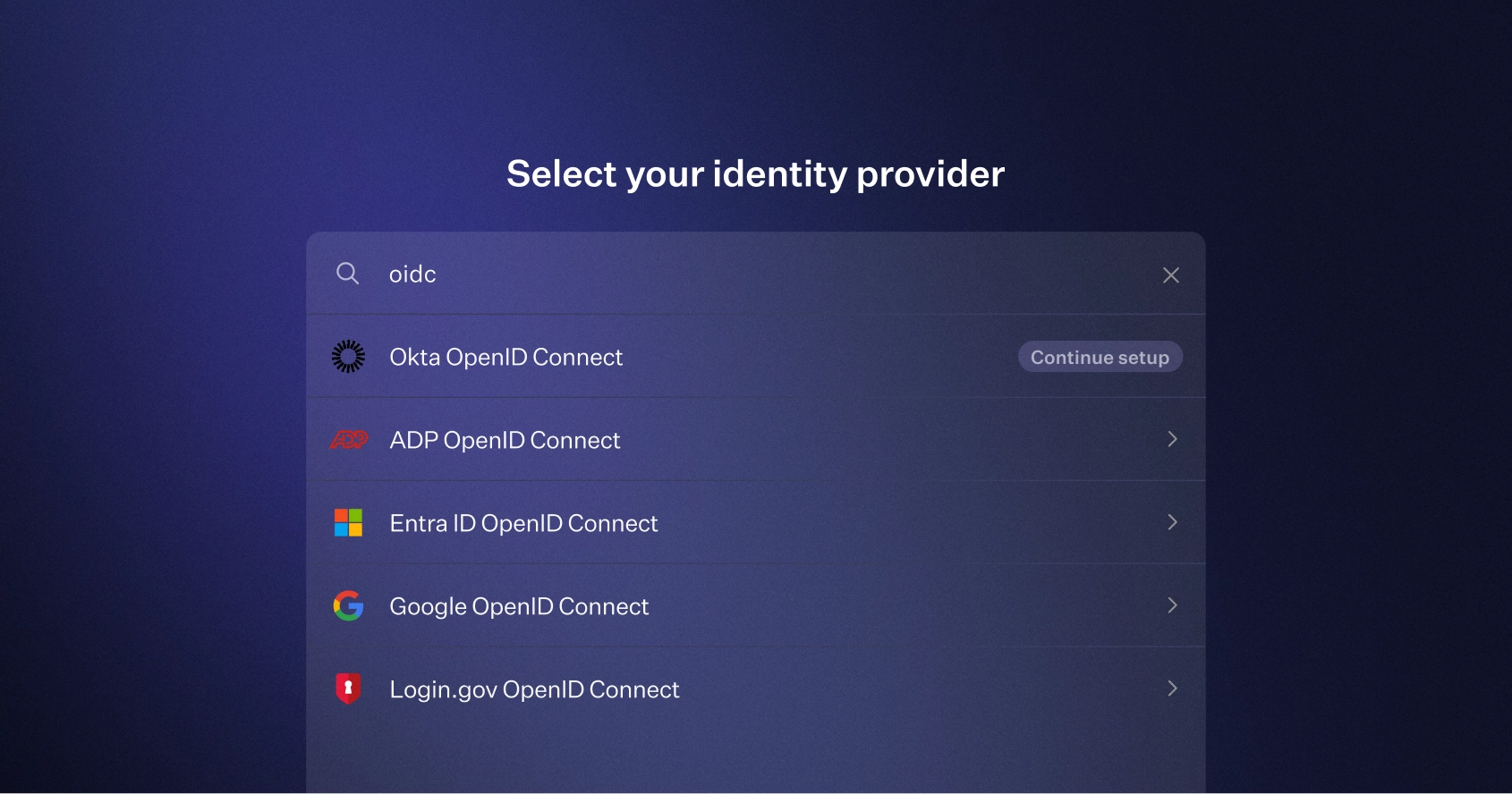
We’ve added support for three new OIDC-based SSO connection types: Okta OIDC, Entra ID OIDC (formerly Azure AD), and Google OIDC. These new options make it easier to integrate with modern identity providers using the OIDC protocol and include dedicated Admin Portal setup instructions to streamline configuration.
Explore all enterprise integrations →
More featured content